One root cause of cyber incidents stems from employees installing unauthorized proxy servers and cloud-based hosting tools on company computers. These tools create unapproved “external channels,” allowing outside systems to connect directly to the internal network. If exploited, these channels could become entry points for intrusions, data exfiltration, or further compromise of internal systems.
This highlights a broader challenge faced by many enterprise IT teams. Their responsibilities extend far beyond routine server maintenance and account management; the greater difficulty lies in maintaining visibility into what software is installed across hundreds of employee devices. As organizations grow, ensuring that staff use only approved and legally compliant applications becomes one of the most complex and urgent tasks in modern cybersecurity.
A tool that appears harmless—perhaps installed by a developer for testing—can quietly introduce risk if no proper review or monitoring process is in place. It may even create unintended “external access channels” or serve as a launchpad for attackers. Common maintenance utilities like PsExec and ProcDump are often exploited in internal intrusions and privilege escalation. Meanwhile, VPN clients, remote desktop tools, and portable applications can bypass security policies and increase the risk of data leakage.
So, how can enterprises determine whether these software tools that pose potential risks exist within their environment?
ThreatSonar Anti-Ransomware can help enterprises identify potentially unsafe software programs
In addition to real-time threat detection, TeamT5’s ThreatSonar Anti-Ransomware, Endpoint Detection and Response Platform can perform historical retrospective analysis. Through the rules of ThreatSonar Anti-Ransomware's threat tracking feature, the software programs mentioned above can be identified. The relevant rule sets are shown in the figure.
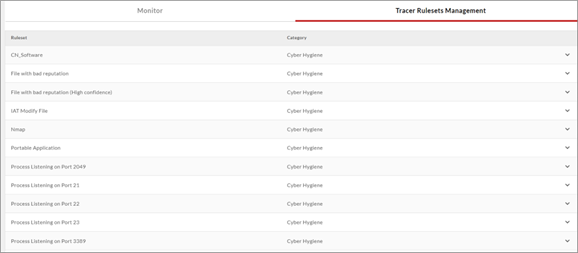
Besides existing rule sets, you can also search for software installed in the environment using criteria such as file name, hash value, and signature. In the example below, the signature is used as criteria to locate related software–even those with modified file names. Furthermore, you can query the file path and related signatures.
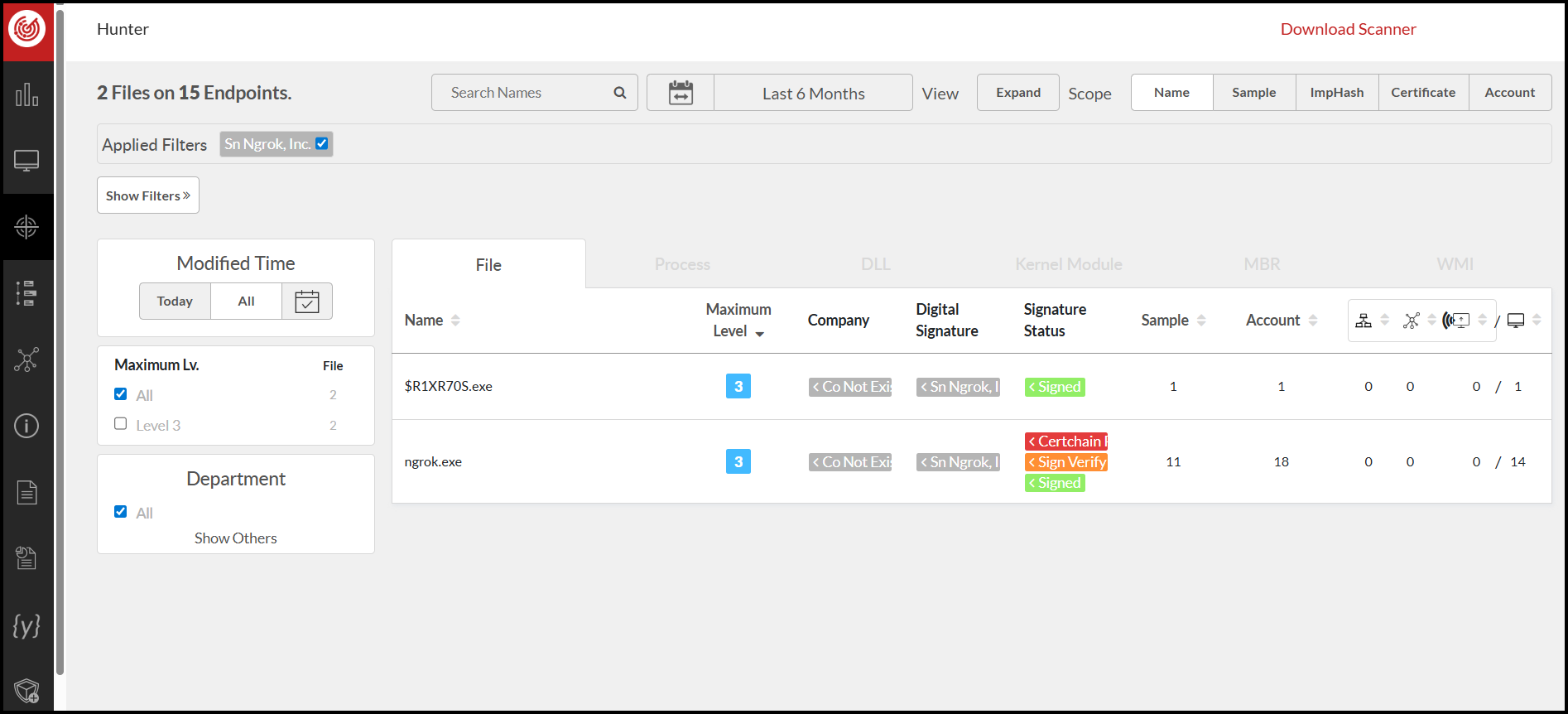
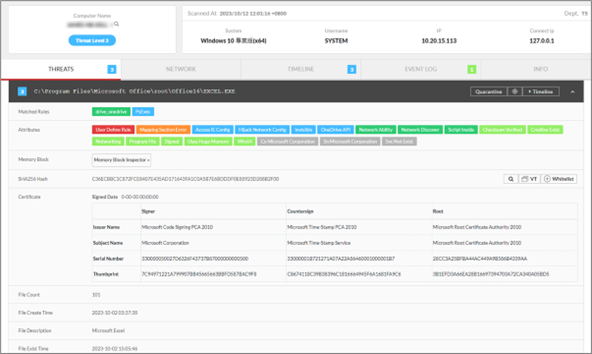
ThreatSonar Anti-Ransomware makes managed detection and response service more efficiently
For managed detection and response (MDR) service providers, ThreatSonar Anti-Ransomware offers more than just reactive alert handling. Instead of passively waiting for notifications before taking action, providers can use the platform to proactively hunt for hidden threats across the enterprise environment.
Through its advanced threat-hunting capabilities, providers can proactively detect grayware that is easily abused, as well as software that violates corporate cybersecurity regulations. This allows them to identify potential risks early and prevent incidents before they occur. In addition, providers can deliver regular threat-assessment reports and analysis, helping clients clearly understand the cybersecurity risks in their environment.
Understanding the current state of your environment is the best starting point for cybersecurity defense. Contact us for a free demo of business cooperation!
TeamT5 consists of top cyber threat analysts. Leveraging our geographic and cultural advantages, we have the best understanding of cyber attackers in Asia Pacific. TeamT5 is frequently invited to share insights at top cybersecurity conferences. Our threat intelligence research expertise and solutions are recognized as the 2023-2024 Company of the Year Award in Taiwanese Threat Intelligence by Frost & Sullivan.Contact us: link