In today’s increasingly complex threat landscape, organizations should evaluate the effectiveness of cybersecurity solutions not merely by their listed specifications, but through empirical data that reflects their real-world defense capabilities.
Recently, TeamT5’s ThreatSonar Anti-Ransomware Endpoint Detection & Response Platform successfully completed Breach and Attack Simulation (BAS) testing conducted by Leukocyte-Lab. The results demonstrated strong defensive capabilities against real-world attack scenarios.
This article explains how the solution performs in a simulated cyber kill chain, which specific attack techniques it effectively blocked, and how organizations can interpret these test results as a valuable reference when selecting cybersecurity solutions.
What Is Breach and Attack Simulation (BAS)? Why Should Cybersecurity Solutions Undergo BAS Testing?
BAS is an automated testing method that simulates the adversarial tactics observed in real-world cyberattacks to verify whether security defenses can effectively detect and respond to threats in real time. Unlike traditional penetration testing, BAS emphasizes continuity and repeatability, allowing organizations to periodically evaluate the effectiveness of their defense strategies and immediately uncover potential gaps in protection.
For cybersecurity solutions, successful completion of BAS testing serves as empirical verification of both functional integrity and operational effectiveness. It enables users to understand a solution’s actual protective capabilities under real attack conditions—whether it can detect attacks, correlate anomalous events in a timely manner, and execute effective response and remediation. Consequently, BAS testing results offer enterprises objective, evidence-based data to evaluate and select cybersecurity solutions.
How Cybersecurity Solutions Perform in a Simulated Attack Chain
BAS testing simulates complete attack lifecycle derived from real-world APT incidents, covering stages from initial intrusion and lateral movement to data exfiltration. The simulation begins with Bypass User Account Control (UAC)—a common attacker tactic that exploits system vulnerabilities or techniques to grant administrative privileges without user approval. The next stage involves privilege escalation to enable malware or an attacker to perform high-privilege operations without triggering UAC prompts, eventually deploying ransomware.
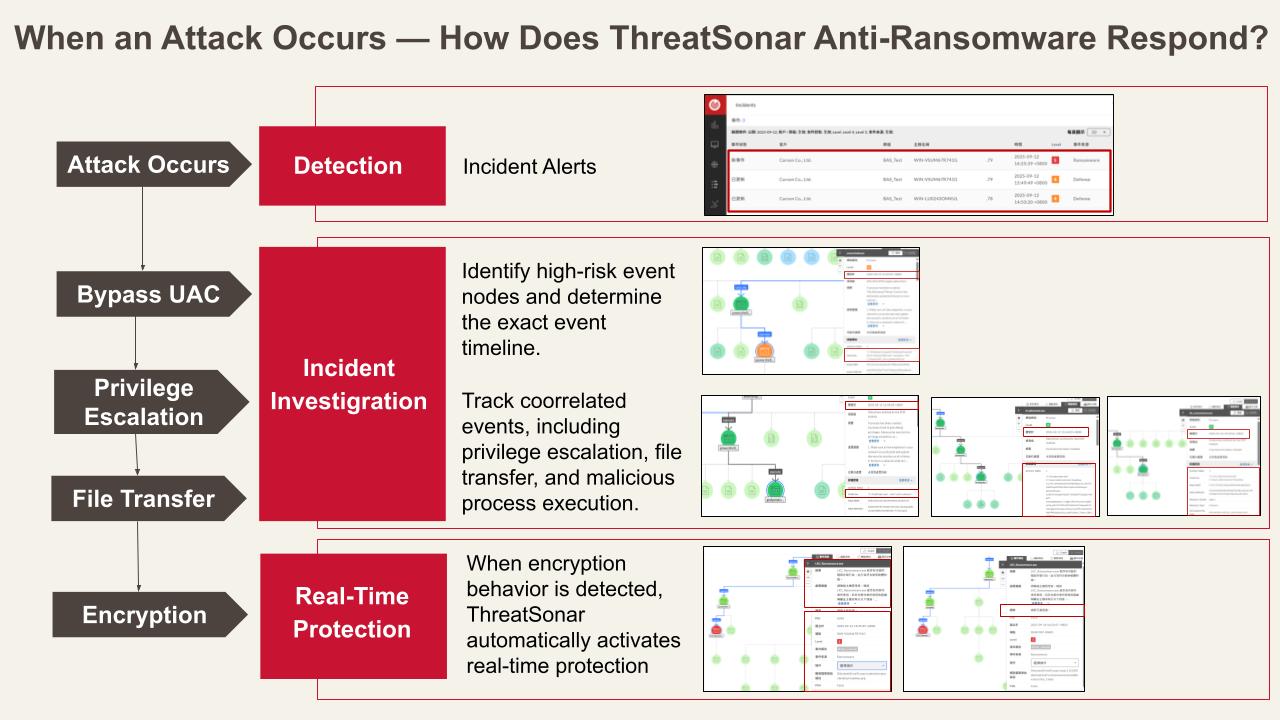
During the simulated attack, TeamT5’s ThreatSonar Anti-Ransomware Endpoint Detection & Response Platform not only passed the BAS test and promptly blocked malicious behaviors, but also demonstrated the following key defense capabilities:
- Real-Time Alerting and Process Blocking ThreatSonar Anti-Ransomware’s Protect Plus feature strengthens protection by detecting file encryption behavior and immediately terminating the malicious process to prevent further propagation.
- Detect Correlated Attack Behaviors and Response Beyond isolated event alerts, ThreatSonar Anti-Ransomware correlates endpoint behaviors with threat intelligence to reconstruct the full attack chain, accelerating incident response and remediation.
How Organizations Can Leverage BAS Testing to Evaluate Cybersecurity Effectiveness
Many organizations evaluate cybersecurity solutions primarily based on technical features. BAS testing offers objective and quantifiable performance indicators, helping organizations understand their true defense effectiveness.
Organizations can interpret BAS test results from the following three perspectives:
- Protection coverage: Evaluate the solution’s detection and blocking capabilities to identify blind spots in the attack lifecycle, and verify the completeness of existing defenses.
- False positive rates: An effective defense system should accurately identify threats while minimizing alert fatigue and reducing the risk of missed detections—ensuring robust protection without disrupting daily operations.
- Response speed and visualization: Assess whether the system can quickly visualize attack paths and impact scope, enabling faster incident triage and investigation.
By analyzing protection coverage, accuracy, and response speed, organizations can make more informed decisions when selecting solutions and continuously improve their overall defense posture.
Summary
In an era where cybersecurity decisions demand absolute precision, BAS testing provides organizations with objective evidence of a solution’s reliability.
The ThreatSonar Anti-Ransomware Endpoint Detection & Response Platform, validated by Leukocyte-Lab, has demonstrated exceptional defense accuracy and effectiveness in simulated attack scenarios—proving its ability to block sophisticated threats and safeguard organization environments.
TeamT5 consists of top cyber threat analysts. Leveraging our geographic and cultural advantages, we have the best understanding of cyber attackers in Asia Pacific. TeamT5 is frequently invited to share insights at top cybersecurity conferences. Our threat intelligence research expertise and solutions are recognized as the 2023-2024 Company of the Year Award in Taiwanese Threat Intelligence by Frost & Sullivan.Contact us and know more of intelligence-driven cybersecurity solutions - https://teamt5.org/en/contact-us/.