Continuous Monitoring, No Threats Can Hide
Through the engine's self-learning mechanism, it can automatically identify commonly used or new malicious programs and effectively detect encrypted files.
Beyond Detection:
Proactive Intelligence-driven Defense
ThreatSonar Anti-Ransomware Endpoint Detection & Response platform to stay ahead in continuous threat intelligence prediction and to monitor abnormal behaviors at all times. The platform is dedicated to fight against advanced persistent threats (APTs) and ransomware.
Through the engine's self-learning mechanism, it can automatically identify commonly used or new malicious programs and effectively detect encrypted files.
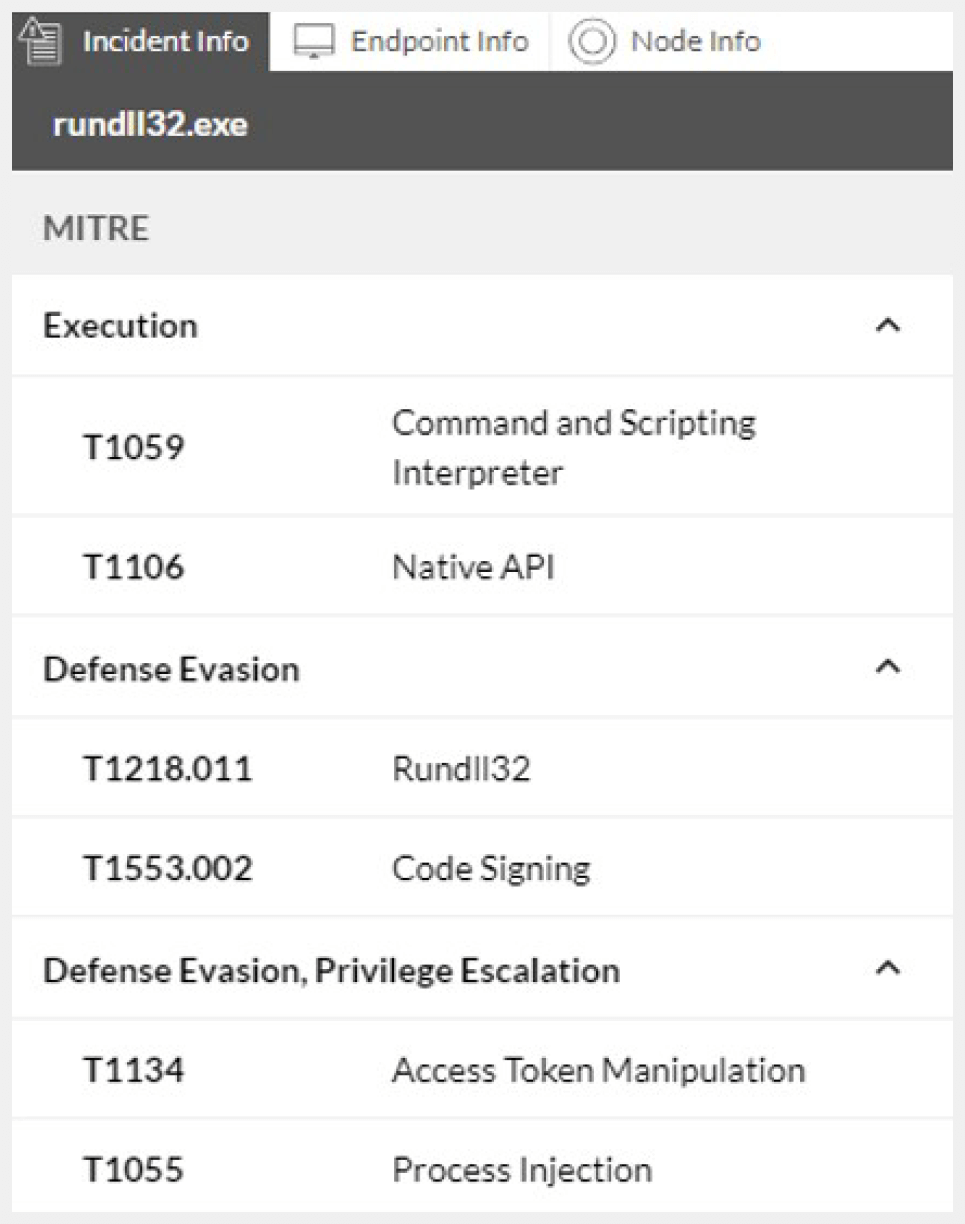
Since each security event is tagged with the relevant ATT&CK tactics and techniques, the cybersecurity team can instantly assess the effectiveness of their defenses against certain adversary groups.
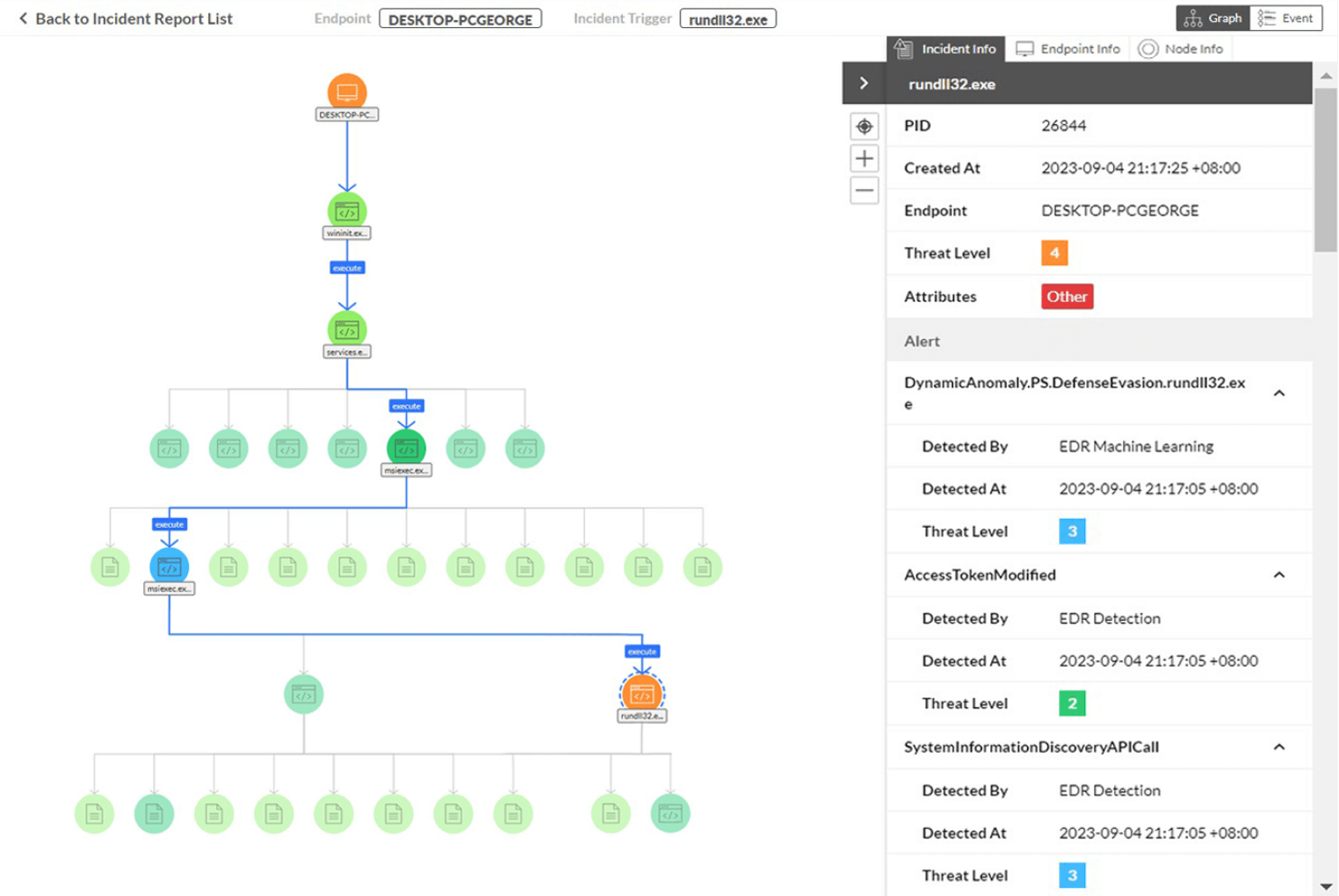
By visualizing the path of attack, cybersecurity analysts can easily identify and gain a deeper understanding of the attacker's behavior, facilitating rapid incident recognition and enabling effective mitigation measures.
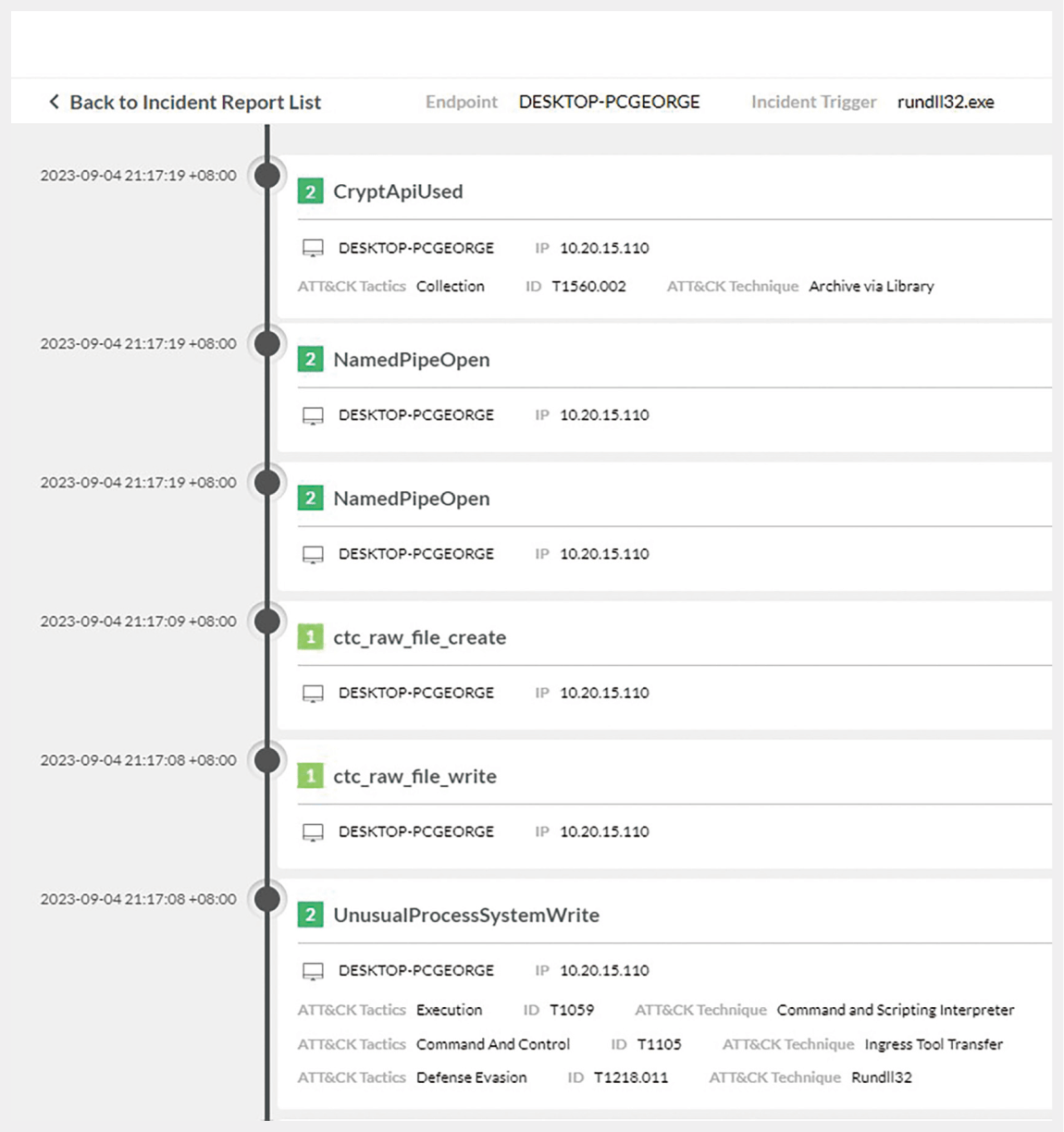
Through the event timeline, presenting in both node-focused and event-centric ways, the chronological analysis can speed up the incident investigation.
Threat Intelligence
Detect New Program
Real-time Response
System Restore Protection
High detection coverage, precise blocking of potential threats.
Automatically analyze threats, expedite incident handling.
Assist cybersecurity personnel in assessing risk levels, focus on handling high-risk incidents.
Automated intelligent threat hunting, proactively discovering lurking threats in the environment.
Prevent lateral movement, remediate threat damage.

ThreatSonar Anti-Ransomware solution is awarded 2024 Computex Best Choice Award - Golden Award
FAQs
ThreatSonar Anti-Ransomware is an endpoint detection & response (EDR) platform, assisting businesses and organizations to detect, identify and respond to threats, especially those endpoints encounter, such as ransomware, APTs, etc.
Strengthen endpoint defense in depth and multi-layered defense architecture
1. Improve security: Enterprises face various malware, ransomware attacks, etc. EDR provides real-time endpoint monitoring and accelerate responding time to threats.
2. Threat hunting: EDR can hunt threats and analyze incidents, track the malicious behaviors of attackers, and effectively prevent attacks.
3. Quick response: Automatic identification and response. Quickly isolate infected endpoints, prevent the spread of threats, and reduce losses.
Sure! ThreatSonar Anti-Ransomware not only detects malicious programs based on known malware signatures, but can also identify the latest and unknown threats through behavior detection, which can protect against ransomware before compromise.
Yes! The TeamT5 team has more than 20 years of experience in threat intelligence research and security incident response, and have mastered hacker attack techniques, turning them into intelligence in a proactive threat detection mechanism. Through the engine's continuous self-learning, it can automatically determine commonly used programs or new malicious programs. Once an unauthorized program attempts to access the system, response measures will be automatically triggered to promptly block malicious programs from ransomware encryption.
Yes! Upon detecting abnormal behavior, ThreatSonar issues real-rime alerts, visualizing the path of the attack and correlated devices. With the auto-generated incident summary, the relevant MITRE ATT&CK tactics and techniques and response suggestions, the security team can rapidly analyze incidents and execute endpoint isolation and scan. Shortening the response process, promptly reducing damage.
TeamT5 Managed Detection and Response (MDR) Service provides 7*24 endpoint monitoring and periodical threat hunting by a professional team of experienced experts to discover threats and provide response suggestions. Once there is a suspicious incident, TeamT5's MDR team will work with the businesses and organizations to respond, conduct in-depth investigation and analysis of the root cause of the incident, and optimize security defense measures.