The average dwell time of cyberattacks fell to a median of eight days in the first half of 2023, but attackers are moving faster.[1] It only takes about 16 hours for an attacker to gain access to the Active Directory (AD) system and perform various malicious activities through privilege escalation and lateral movement.
At the same time, ransomware attacks continue to grow. According to the annual crime report released by cryptocurrency-tracing company Chainalysis, the number of ransomware attacks in 2023 increased significantly by 70% compared with 2022, causing ransomware payments to hit a record $1.1 billion. [2]
EDR is indispensable to enhance defense in depth
As attackers' techniques continue to evolve and attack faster, it becomes necessary for enterprises to adopt a "defense-in-depth" cybersecurity strategy in order to effectively respond to cybersecurity risks. Through a variety of cybersecurity solutions, corporate networks and digital assets are protected at multiple levels. Even if an attacker destroys one layer of defense, the existence of other security defense measures can effectively prevent the attacker from accessing the network or internal resources, effectively mitigate the threat, and reduce the damage to the overall environment.
EDR is critical for defense in depth, used to protect servers, mobile devices and other endpoints from network security threats. It should be able to check files and programs in a timely manner, quickly identify potential threats, and effectively respond to possible malicious attacks and reduce enterprise cybersecurity risks.
ThreatSonar Anti-Ransomware Endpoint Detection & Response platform provides comprehensive endpoint protection, while improving defense in depth and solving pain points in enterprise cybersecurity deployment.
- Comprehensive monitoring of endpoints: Different from stacking multi-layered defense architecture on the network, ThreatSonar Anti-Ransomware provides 7x24 full-time monitoring of endpoint security.
- Compatible with other solutions: Solving the limitation that enterprises can only choose one product for endpoint defense.
- Lightweight deployment: Unlike most endpoint APT threat solutions that require driver installation.
Visualize attack trajectories to investigate incidents and response in a timely manner
ThreatSonar Anti-Ransomware provides real-time threat detection and in-depth threat hunting functions. It not only supports high-risk threat alerts, but also finds objects and logs related to the threat through correlation analysis, which facilitate the security personnel to understand the full picture of intrusion through the incident timeline.
In order to allow users to quickly understand potential threats, the incident page of ThreatSonar Anti-Ransomware can provide an overview of the incident trajectory, starting from the hosts that were severely compromised in the incident, to comprehensively take stock of the endpoint security status.
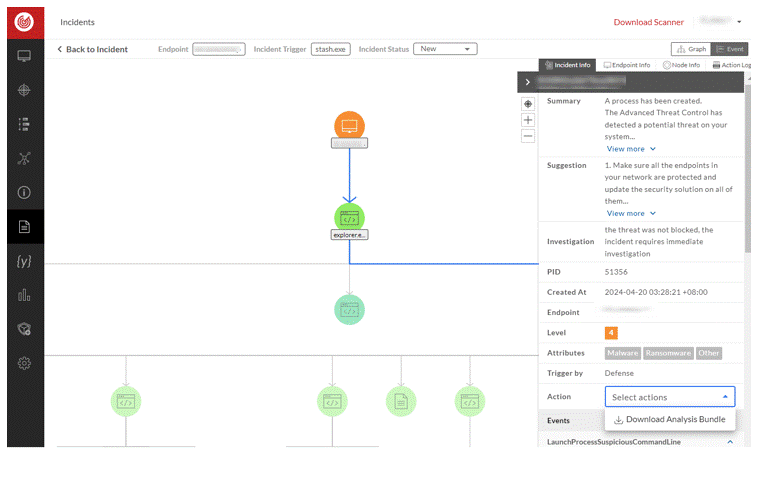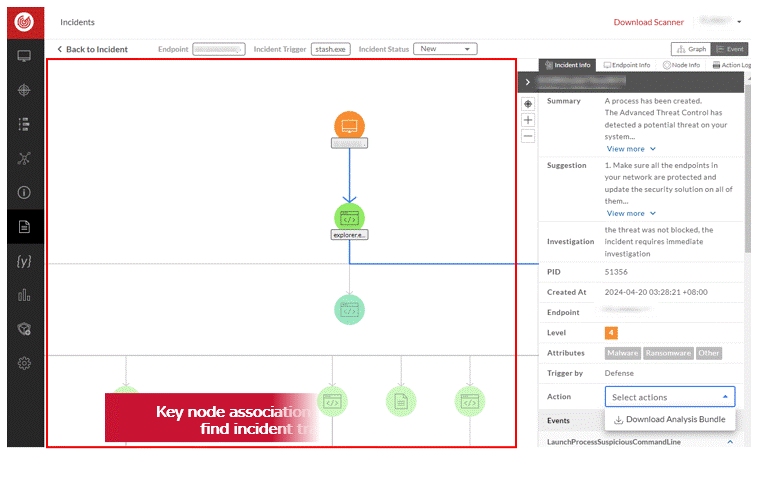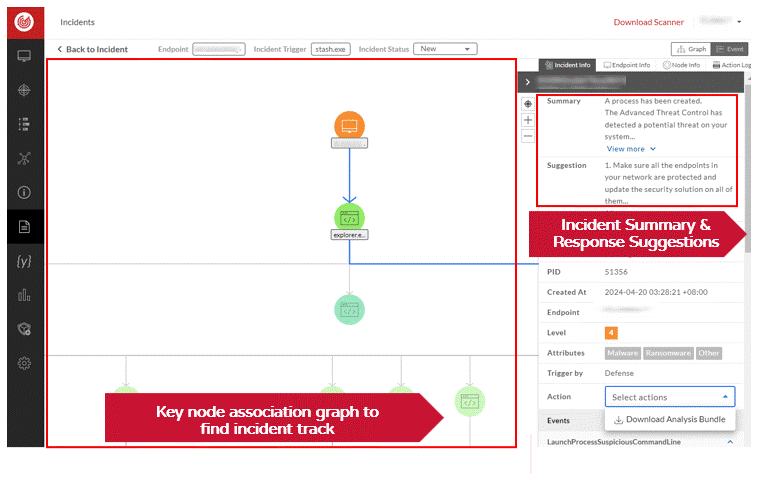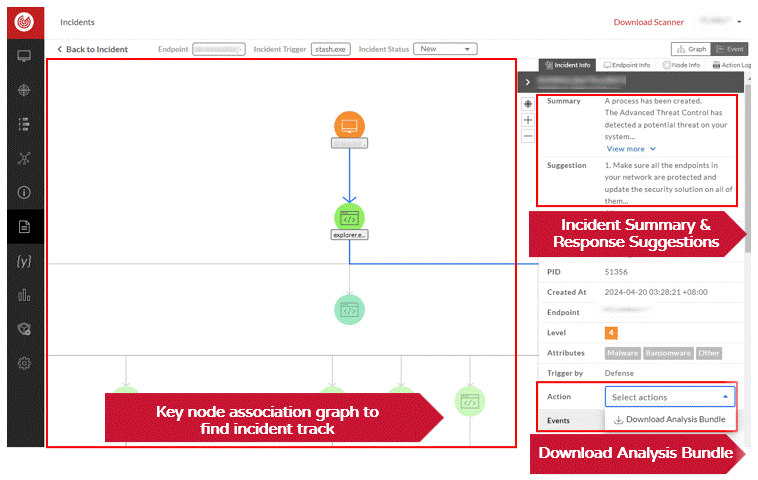
1. Real-time Detection:
Once ThreatSonar Anti-Ransomware detects a threat incident, iit automatically provides an incident summary and response suggestions, grasps the incident status, and handles it in a timely manner to reduce the risks caused by the threat.
2. In-depth Analysis:
If users would like to have further incident investigation, the analysis report bundle can be directly downloaded to make analysis more efficient.
3. Take Actions:
Users can take actions and dispatch the tasks, such as scan and isolation, on the endpoints.
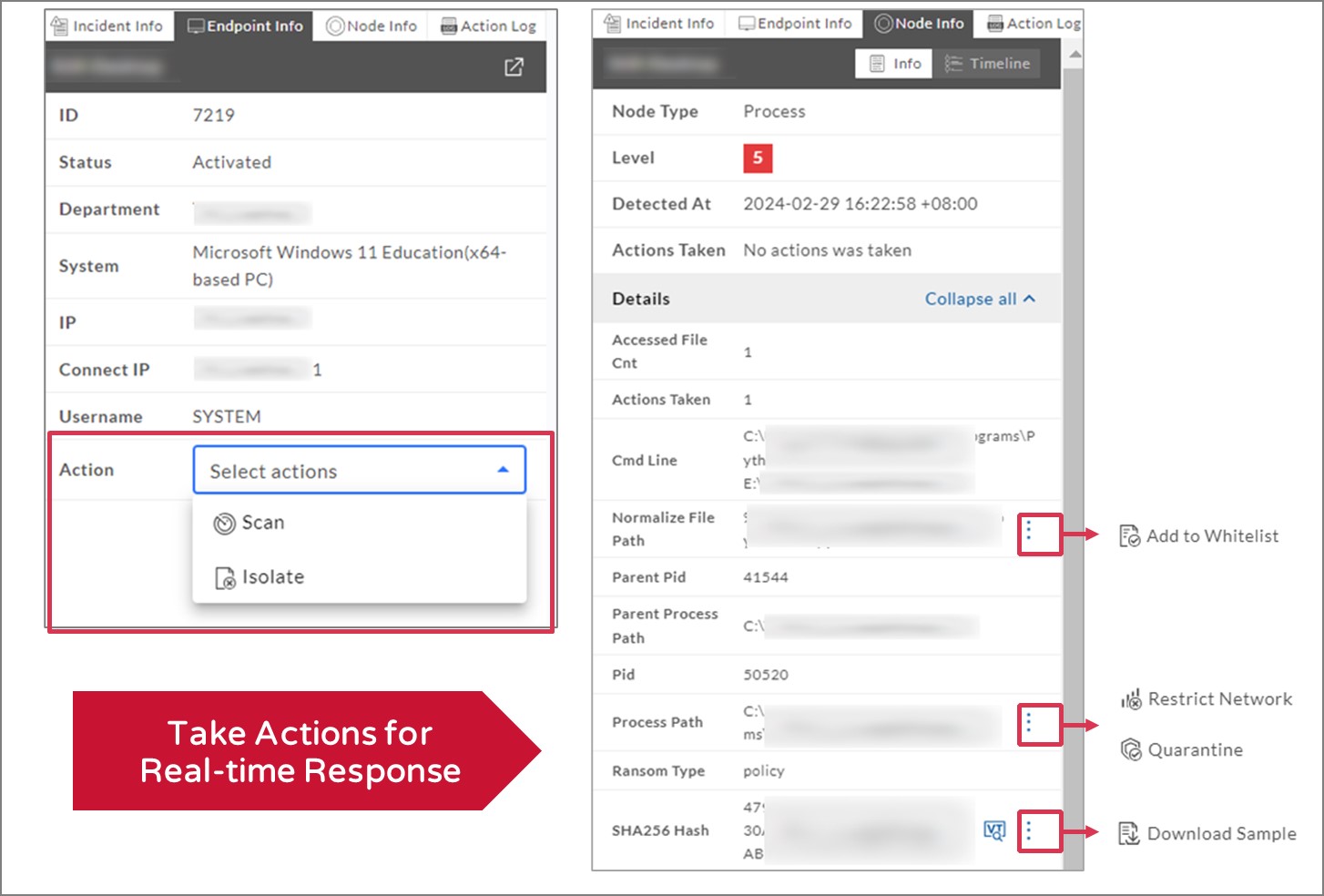
When a ransomware attack occurs, ThreatSonar Anti-Ransomware can promptly detect, immediately respond, and grasp the attack path. Ransomware can be blocked immediately when hitting the policy rule. With the detailed incident reports of ThreatSonar Anti-Ransomware, users can understand endpoint information and malware execution process. Also, users can furtherly investigate the intrusion access points of hackers, obtain the root cause of intrusion, analyze the hacker's movement path, and check damages of the compromised assets.
[1] “Attack Dwell Times Fall but Threat Actors Are Moving Faster”, Infosecurity Magazine, 2023
[2] “Ransomware Payments Hit a Record $1.1 Billion in 2023”, WIRED, 2024
TeamT5 consists of top cyber threat analysts. Leveraging our geographic and cultural advantages, we have the best understanding of cyber attackers in Asia Pacific. TeamT5 is frequently invited to share insights at top cybersecurity conferences. Our threat intelligence research expertise and solutions are recognized as the 2023 Company of the Year Award in Taiwanese Threat Intelligence by Frost & Sullivan.Contact us and know more of intelligence-driven cybersecurity solutions https://teamt5.org/en/contact-us/
Related Post
IR Service Resources
2022.11.22
[Incident Response] How to Deal with Ransomware Attacks?
ransomware, ransomware attack, incident response