Cybersecurity incidents occur frequently. The Global Risks Report 2024 of the World Economic Forum (WEF) predicts that cyber insecurity will be the main source of risk in the technology field between 2025 and 2026. Over the two-year period, cyber insecurity will be ranked fourth among top 10 severe global risks.
Since cybersecurity risks must not be ignored, enterprises and organizations should seek appropriate security measures. The endpoints, such as the desktops and laptops, are part of a defense-in-depth strategy for security controls. Regardless of Windows, MacOS or Linux operating systems, all endpoints are all likely to be targeted and invaded by attackers.
In order to reduce cybersecurity risks for enterprises and organizations, Managed Security Service Providers (MSSPs) need efficient endpoint detection and response tools (EDR) to help cybersecurity teams quickly defend against evolving threats, prevent cybersecurity attacks from disrupting daily operations, and reduce possible operational risks.
To achieve efficient cybersecurity measures with simplicity, EDR needs to have the following 3 key features:
1. Automatically track potential threats, simplify the troubleshooting process, and improve threat hunting efficiency
EDR monitors endpoints and detects threats in real time, automatically tagging abnormal behaviors (such as malware execution or unusual logins) without complex manual analysis. Compared with conventional multi-layered tools, EDR has an easy-to-use interface that allows security teams to quickly focus on high-risk issues.
2. Visualized display of cybersecurity situation, easy to grasp potential risks
Transform complex suspicious paths into understandable information with EDR’s threat event timeline and visualized reports. Compared with the lengthy logs generated by conventional tools, visualized endpoints associated with high-risk events can help teams quickly determine the compromised scope to facilitate further response measures.
3. Automatically generate summary reports to improve management efficiency
Automatically generate summary reports that summarize key information about cybersecurity incidents, such as threat sources, lists of high-risk endpoints, and other related information. This saves cybersecurity teams efforts in manually sorting through large amounts of data, making it ideal for managers to quickly understand endpoint status.
ThreatSonar Anti-Ransomware: User-friendly Interface, Easy Management, Quick Response
The intuitive interface of the ThreatSonar Anti-Ransomware can help the cybersecurity team to easily manage and quickly handle cybersecurity incidents.
Visualized Dashboard: Understand the endpoints status and potential risks at a glance
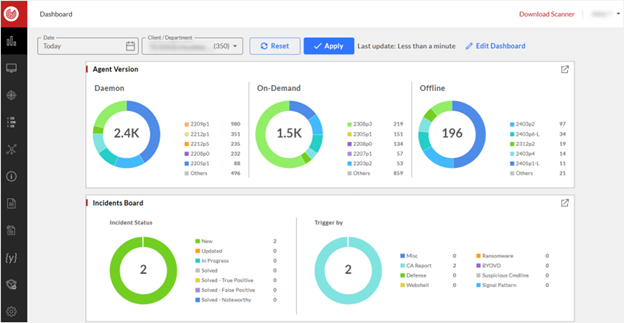
To allow users to comprehensively grasp potential threats, the dashboard has the following features:
1. Visualize key indicators to easily overview the cybersecurity posture
- Display the current status of important endpoints by easy-to-understand charts, saving time in collecting data and statistics, and improving management efficiency.
2. Flexible interface design for easy customization to meet diverse demands in different management scenarios
- Users can easily add or remove widgets from the dashboard.
3. Interactive user-centric design to better present information
- Easy-to-use intuitive design enables users to preview advanced information of each section by hovering, quickly grasping key information.
- If further details are needed, users can click on the links to be directed to the relevant pages.
Threat Tracer: Automatically track potential threats, simplify the troubleshooting process, and improve threat hunting efficiency
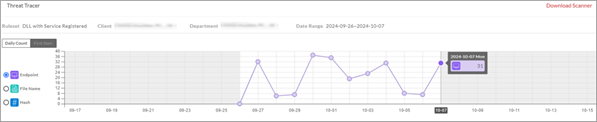
With pre-defined threat hunting rulesets, the cybersecurity team can save time on processing threat hunting routines, focusing on potential threats in the environment, and quickly reviewing the status of automatic threat hunting. The rulesets can assist the team accurately grasp threat risks to facilitate subsequent incident investigation and analysis.
The main threat hunting rule types of ThreatSonar include:
- Cyber Hygiene: Check whether there is any software that may pose a security threat, such as remote desktop software (RDS) and portable software.
- Suspicious Files: Check whether there are suspicious programs that disguise as system files, files with suspicious creation times, suspicious files being located and deleted, etc.
- Suspicious Processes: Check whether there are any injected suspicious processes, auto-run programs, suspicious ransomware behaviors, etc.
- Suspicious Dynamic Link Libraries: Check whether there are suspicious dynamic link libraries (DLLs) with path hijack, suspicious DDLs with hidden file attributes, etc.
- Others: Check whether the credentials are used by SoftEther VPN attackers to penetrate the intranet.
Users can also use the chart to view the trend of the total number of endpoints, file names, and hashes that match the rulesets within a specific time period. This feature can automatically track potential threats over a long term, helping users to quickly understand significant changes. This can also benefit MSSP to save workforces and time on dealing with cybersecurity incidents.
Summary Report: Automatically generated, save your time and efforts
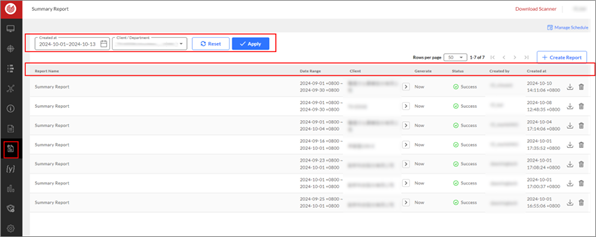
This function can help users to review the cybersecurity situation based on their needs, list high-risk endpoints that need attention, and automatically generate summary reports. It can also set up scheduled reports and group emails.
For Managed Security Service Providers (MSSPs), this feature includes a "Customer" option, allowing them to easily identify which reports belong to which customer. This enables MSSPs to monitor the status of all customers on a single screen without the need to switch views.
Summary reports automatically compile a variety of statistical data and present them in charts, eliminating the need for cybersecurity teams to manually sort through large amounts of data. At the same time, users can customize summary report items and schedules to facilitate MSSPs to manage endpoint monitoring for different customers, view potential threat risks of all endpoints, and improve response efficiency.
Examples:
1. Threat Level Stat. CA/Anti-Ransomware: Display the number of endpoints that have Level 1 ~ Level 5 threat incidents. Users can have the overview of endpoints with different threat levels from the chart.
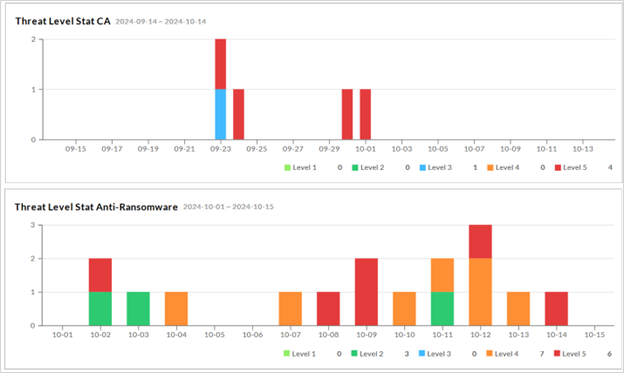
2. CA High-Level Analysis:
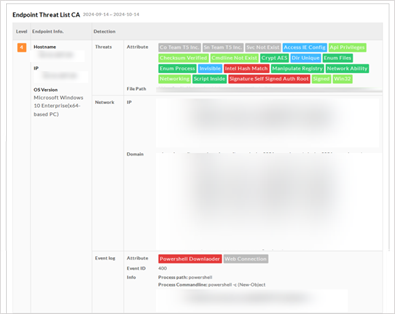
Display the number of endpoints that have Level 4 and Level 5 threat incidents for further analysis or status checking. The Level-5 and Level-4 endpoint list with detailed information, including hostname, IP, OS version and other information regarding "Threats", "Network" and "Event log".
The "Threats" information displays the attributes and file paths; "Network" displays the IP and domain; "Event log" displays the attributes, Windows Event ID and related information.
Summary
Since cyber threats have become a challenge that enterprises and organizations must address, it is imperative to adopt highly effective protection strategies. To minimize these risks, it is crucial to deploy an excellent EDR, which not only can enable efficient defense in an easy-to-use and easy-to-understand manner, but also facilitates enterprises to seize the opportunity and respond quickly to cybersecurity incidents.
TeamT5's endpoint detection and response solution "ThreatSonar Anti-Ransomware" delivers all the capabilities an effective EDR shall have, which are "Automatically track potential threats", "intuitive and visualized display of cybersecurity situation", "automatically generated summary reports to better management efficiency". It was honored with the COMPUTEX Best Choice Award - Golden Award, making it the best choice for enterprises and organizations. The intelligence-driven solution continues to help enterprises and organizations to cope with frequent cybersecurity attacks.
Contact us for a free trial.
TeamT5 consists of top cyber threat analysts. Leveraging our geographic and cultural advantages, we have the best understanding of cyber attackers in Asia Pacific. TeamT5 is frequently invited to share insights at top cybersecurity conferences. Our threat intelligence research expertise and solutions are recognized as the 2023-2024 Company of the Year Award in Taiwanese Threat Intelligence by Frost & Sullivan.Contact us and know more of intelligence-driven cybersecurity solutions - https://teamt5.org/en/contact-us/.
(cover source: pexels)