Challenges
When an enterprise or organization faces a destructive cyber attack, time is of the essence in order to be able to respond and recover from it. If the attacker group can be detected at an early stage when they have infiltrated the victim organization's network, there is still a chance to effectively block the attacker group's behavior immediately, with less impact on the enterprise or organization.
However, the more serious situation that enterprises currently face is that they fail to detect cyber threats in the early stages of attackers' infiltration, or even discover them only after data has been stolen or the system has been damaged. When organizations lack the deployment of endpoint protection tools, ransomware attackers are likely to spread rapidly from the initial access point, encrypting other related systems and hundreds or thousands of important files, shutting down the business. This also makes enterprises facing more and more challenges to quickly recover from ransomware attacks and avoid business interruption caused by damaged networks.
How can enterprises or organizations respond to ransomware effectively? Through the following sharing of the case in which TeamT5 assists enterprises and organizations in cybersecurity incidents you may learn how to strengthen cybersecurity defense, not only prevent malicious attacks, but also minimize the losses caused by cyber threats.
Detect intrusions and respond quickly
TeamT5 received a notification from an information technology company in Taiwan on July 18 that important service hosts in the network environment were subject to encryption and ransomware, and ransomware information was displayed on the desktop of the VM environment.
Upon receiving this notification, the TeamT5 Cybersecurity Incident Response Team (CSIRT) grasped the critical time for incident response and took the following actions as soon as possible:
- Interviewed clients and clarified needs and case status
The incident response team directly held an emergency meeting with the client, clarified the client's needs through interviews, and the current situation of the site being hacked: the VM environment of the ESXi host in the site was encrypted, and ransomware information was displayed on the desktop in the VM environment .
- Provide attack-related information for clients to evaluate and make decisions
The TeamT5 team has more than 20 years of experience in cyber threat research. It immediately assists clients in interpreting the received ransomware information, confirms the ransomware group and other related information, and provides clients with the suggestions in decision-making process.
- Provide suggestions of blocking attackers’ control and proliferation countermeasures
In order to prevent other digital assets from being affected by the attack, the TeamT5 team provides countermeasures to block the attack, including network equipment disconnection and forensics, isolated endpoint scan, system backup and other emergency response measures. Before the root cause of the incident is clarified, it is recommended that relevant network equipment and systems should not connect to the Internet nor enable network communications to prevent attackers from entering the site again to cause damage.
- Collection of key evidence and customized response and investigation plan
In addition to providing information such as field network system configuration, related equipment information and log status, TeamT5 also proposes an overall incident investigation plan. By deploying ThreatSonar, TeamT5's self-developed threat forensic and analysis platform, it can perform evidence collection and forensic analysis on key hosts, and also confirm the cybersecurity posture of other hosts in the VM environment.
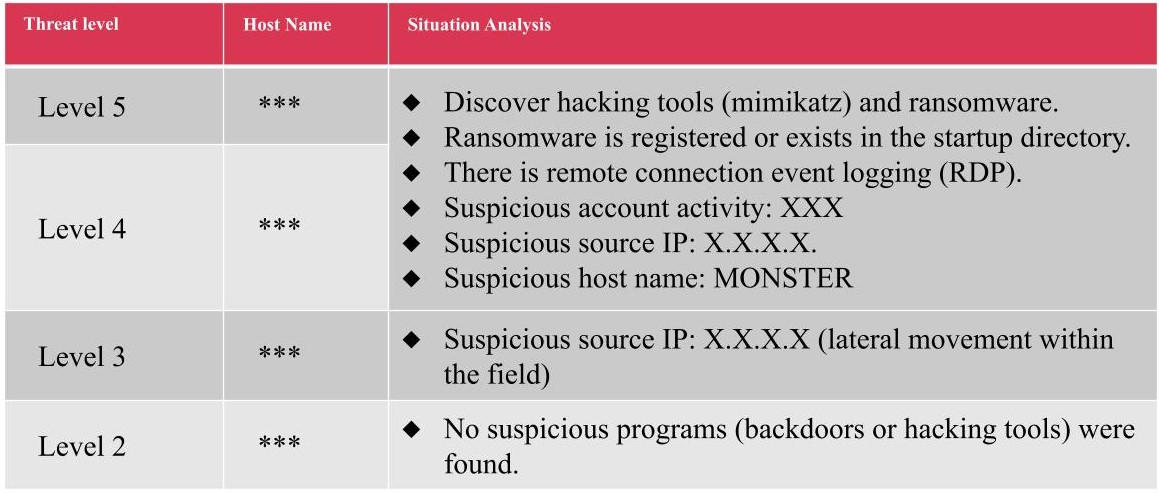
The scan results found that five hosts had high-risk (Level 5) threats and one host had medium-high risk (Level 4). The analysis included hacking tools, ransomware, suspicious accounts, IP sources, etc.
Investigate the root cause of the incident and visualize the attack trajectory
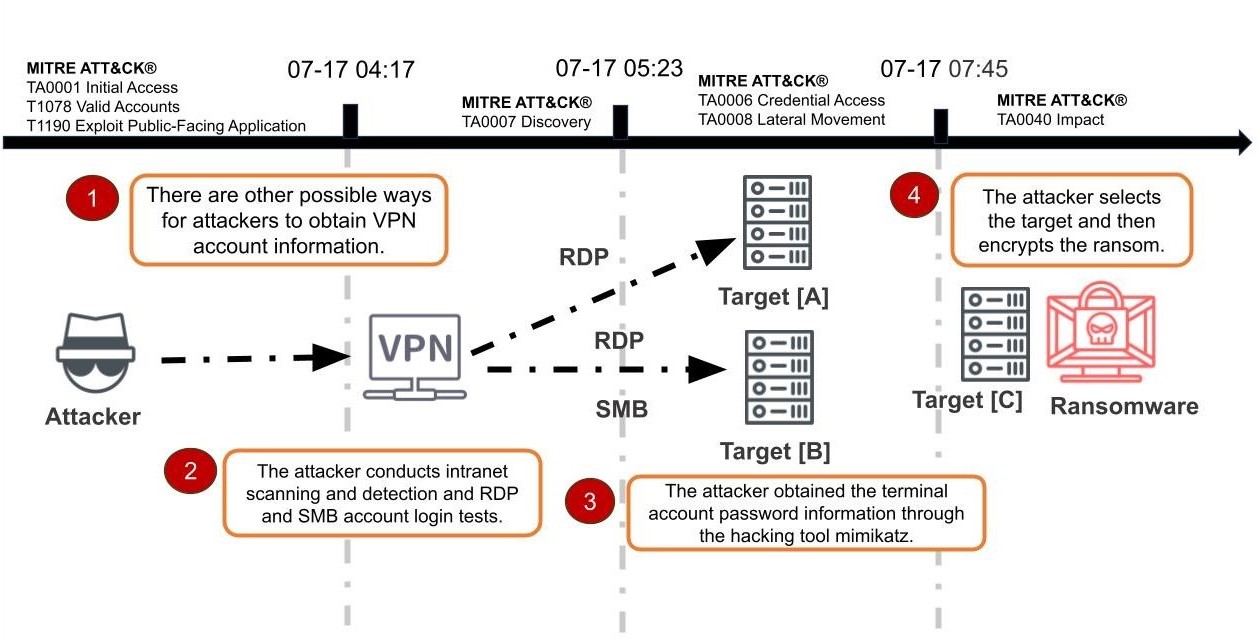
Based on the analysis of quick scan results of the field host and the network communication records, the TeamT5 team immediately carried out related investigation operations on the occurrence of the field incident, and grasped the attack time, tools and other details in detail as follows:
- Ransomware: Scanning analysis found that eight of the fourteen hosts were injected with ransomware.
Injection location: C:\Documents and Settings\All Users"Start" menu\Programs\Startup\fast.exe
- Hacking Tools:
Location: C:\WINDOWS\Temp\temp(mimikatz)
- Incident correlation:
RDP login information: Source IP, Target User, Source Workstation (MONSTER), Logon Type 10 (RDP)
Through threat hunting, lateral movement trajectories are visualized, allowing clients to clearly understand the root causes of incidents and carry out subsequent enhanced cybersecurity defense plans.
Restore the pre-invasion environment and strengthen defenses to prevent similar attacks.
After completing the incident investigation and identifying the root cause of the incident, TeamT5 works with the client to help confirm whether the following response actions to the cybersecurity incident have been implemented.
- Confirm endpoint cybersecurity posture
First confirm that there is no running ransomware on the endpoint. You can try to start in the system safe mode. After removing the ransomware, use ThreatSonar to continuously scan other endpoints to confirm the cybersecurity status of the endpoint.
- Check network access policy
Check the access rules for service hosts in the field to reduce the risk of attackers moving laterally.
- Confirm system account usage
For accounts found to be exploited in the case, if they are not known accounts, they must be immediately deactivated and the account creation time must be confirmed; domain administrator and user passwords must be changed immediately, and AD reconstruction must be evaluated.
- Confirm the source of the attack
It is found that the source of the attack in this incident is the firewall. It is recommended to confirm the status of the firewall device, update the version, and check the device access status.
Learn from incidents to optimize long-term strategies for Cybersecurity defense
TeamT5 provides a complete incident investigation report. In addition to detailing the root cause of the incident, hacker groups, attack methods, etc., it also provides targeted remedies and further practical suggestions for long-term cybersecurity defense:
1. Block the source of hacker control and reduce the risk of secondary hacking:
- Digital assets assessment: Confirm the security status of endpoints, grasp the security status of service interfaces that are exposed and may be attacked, and reduce the risk of being controlled by hackers, encrypted and extorted, causing service shutdown.
- Confirm the security of VPN equipment and systems: Based on the client's actual site environment, it is recommended to patch equipment vulnerabilities, prohibit multiple people from sharing accounts, and enable the two-stage verification mechanism and device verification mechanism to prevent attackers from gaining access and moving laterally to cause damage.
- Control network access management : When clients use Remote Desktop (RDP), if remote management is not implemented, it is recommended to strengthen the management interface and access control of important hosts to prevent attackers from accessing important hosts through internal hosts and encrypted ransomware.
- Improve personnel security awareness: You need to be security aware of phishing emails and website downloads to avoid account and password theft or execution of malicious programs.
2. Strengthen cybersecurity monitoring measures to detect abnormalities early:
- Endpoint detection and protection: It is not only necessary to rely on anti-virus software, but also to establish a terminal security defense mechanism to reduce the risk of threats such as malicious programs, encryption ransomware, and lateral movement.
- Enable event log: Enable event logs such as Event ID 4688 (program execution), Event ID 4625, 4624 (login audit), etc. AD and account authorization management: Confirm the usage of privileged accounts and general accounts to avoid password theft.
- Network communication policy settings: Confirm the systems or terminals allowed by the rules and their open connection settings to reduce the risk of access control threats.
- Check the server service log: Confirm whether there is any detection or attack situation, detect it in advance, handle it as soon as possible, and prevent intrusion detection.
3. Improve data backup and system restoration mechanisms to minimize hacker losses:
- Strengthen the 3-2-1 backup principle to ensure that normal operations can be restored when data is damaged or encrypted, and can prevent threats such as encryption blackmail and service shutdown.
By reviewing the entire cybersecurity incident handling process and reviewing whether there are any areas that need to be strengthened, firstly, this can reduce the possibility of similar attacks happening again, and secondly, even if similar cybersecurity incidents are faced again in the future, they can be handled more effectively.