Challenges
As we all know, hackers often use various network attack methods, such as zero-day attacks, phishing, brute force attacks, social engineering, malware, etc., in an attempt to gain system access and sensitive data. Then, the data is used to target enterprises, governments, or individuals. All these cyber threat events pose a major threat. Taking the leakage of personal information as an example, it causes people to lose money due to fraud and directly damages the reputation of enterprises.
According to an IBM report[1], the global average cost of data breach reached USD $4.45 million in 2023, including operating losses, business shutdowns, remediation, legal fees and other expenses. These losses alone may be enough to bankrupt a small company. In addition, Harvard Business Review[2] pointed out that data leakage may lead to reduction in credit rating, the loss of competitive advantage, and expose the company to higher borrowing costs and financial risks.
Therefore, how should companies or organizations effectively deal with cybersecurity incidents caused by malicious attacks? The following is a case in which TeamT5 actually assists companies and organizations in handling personal data breach. In this case, you may learn (1) how hackers obtain sensitive personal data through network attacks; (2) the emergency response measures required to deal with the incident; (3) how to reduce the losses caused by the incident threat to the minimum, and plan the defense priorities for future.
If a personal information breach is discovered, we will quickly assist in handling it.
When TeamT5 received the client's demand for cybersecurity incident handling - the company's information had been leaked, causing people to be defrauded, and important service hosts in the network environment had anti-virus alerts.
After receiving the client's request, TeamT5 Cybersecurity Incident Response Team (CSIRT) interviewed the client to understand the case situation, grasped the WebShell and malicious program alarm information of the website host , and provided relevant incident analysis and handling suggestions:
- Interpret alarm information and determine possible causes
The TeamT5 team has more than 20 years of experience in cyber threat research, and promptly assists clients in interpreting received alarms and determining possible intrusion routes for attackers.
- Provide response suggestions to control the spread of incidents
In order to prevent other digital assets from being affected, the TeamT5 team recommends taking emergency response measures such as disconnecting network equipment for forensics, endpoint isolation scanning, and system backup analysis. Before the root cause of the incident is clarified, the device will not be able to access the Internet and network communications to prevent attackers from entering the site again to cause damage. If a system cannot be isolated offline due to business operation requirements, it is recommended to adopt the minimum access principle to limit the system to only connect to relevant hosts and control the scope of service access.
- Collection of key evidence, investigation analysis and planning
In addition to the field network system configuration, related device information and log status provided by the client, TeamT5 also proposes a complete incident investigation plan by deploying TeamT5's self-developed threat forensic and analysis platform on the field host endpoint. ThreatSonar, coupled with professional forensic tool analysis, allows professional security incident investigators to confirm the security status of service hosts and other operating computers in the environment.
Endpoint detection and analysis to understand the scope of attacks
On the day of the incident, TeamT5 immediately assisted the client in taking the following key actions:
- Key forensic analysis: Based on the circumstances of the case, the TeamT5 team identified the host that may be the key incident, and used professional tools to conduct forensic analysis and network equipment communication records at the time of the incident for further investigation into incident correlation.
- Comprehensive scan of endpoints and list of compromised areas: ThreatSonar quickly scanned the security of hosts in the site and found that the host involved had high-risk (Level 5) threats. It analyzed the malicious threats that hit the APT detection rules, abnormal login events, suspicious file paths, and malicious relay station (C2) list and other threat information. ; Another host was detected to have malicious behaviors such as lateral movement and attackers using remote desktop services.
Investigate the root cause of the incident and visualize the attack trajectory
Based on the analysis of quick scan results of the field host and the network record analysis, the TeamT5 team performed related investigation operations on the occurrence of the field event, enabling them to understand the attack path and the root cause of the hack:
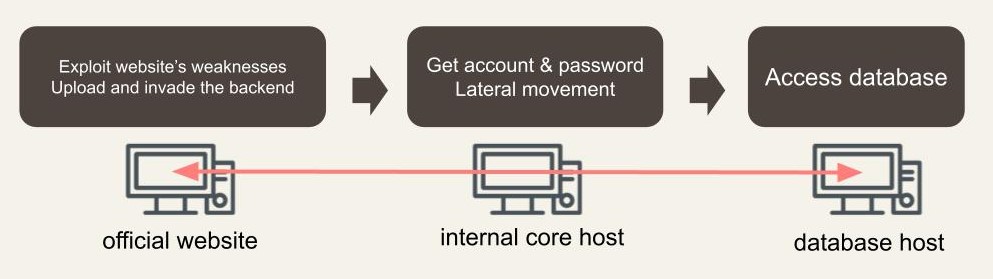
- Incident investigation and analysis: It was found that weak passwords (weak passwords) that are easily cracked were exploited on the website management page. Webshell was detected on the website. After inspection, it was found that the hacker uploaded the malicious web program to the target server through a vulnerability of file upload. At the same time, it was discovered that there was a leakage of relevant file information on the official website.
- Field evidence correlation: From the host event log, it was discovered that there were subsequent behaviors such as Powershell and lateral movement, and the accounts that may have been controlled and used were summarized, as well as the attack source IP information.
- Comprehensive investigation results: Through the visual summary of event trajectories, clients can understand the attack path of the incident and clearly understand how the attacker exploited the website's weaknesses and accessed the website's backend through different IPs, and then obtained a privileged account to have lateral movement.
Block the source of the attack and restore the incident environment
After completing the incident investigation and identifying the root cause of the hack, TeamT5 works with the client to help determine the relevant response actions required for the security incident:
- Confirm whether the security status of field endpoints is clean Through the endpoint security scanner, first confirm whether the endpoints in the field have malicious threatening behaviors, such as backdoors, hacking tools, lateral movement, etc., and then scan and confirm with anti-virus software, and then allow the endpoints to access the Internet one by one.
- Review whether network access rules are strict Check the rules for network management and general users in the domain to access the service host to prevent all hosts from being able to remotely log in to the service host, such as RDP, WinRM, SMB, Anydesk, etc., and block the risk of lateral movement of attackers.
- Confirm whether the system account permissions are appropriate For the exploited account, if it is not a known account, it must be deactivated immediately and the account creation time must be confirmed; in addition, if AD has been implanted with a backdoor or lateral movement, the domain administrator and user passwords must be changed immediately, Evaluate whether to rebuild AD.
- Confirm whether system vulnerabilities can be controlled Analyze and investigate system records such as websites, APs, and DBs to confirm whether there are malicious sources and behaviors, block the discovered malicious sources, and repair possible vulnerabilities. Analyze and investigate the connection source of the firewall and account usage, confirm the device status and update the version. You must ensure that the device is safe before going online for service.
Review cybersecurity strategies and strengthen future defenses
In order to prevent similar incidents from happening again, TeamT5 recommends that clients follow the US NIST Cybersecurity Framework and review the identification, protection, detection, response, recovery, etc. in the enterprise field. Five major aspects of defense:
1. Strengthen field system security (identification, detection, protection)
1. Strengthen field system security (identification, detection, protection)
- Understand the configuration and operation of system endpoints in the field.
- Strengthen backend management accounts and restrict access sources.
- Control data access sources and restrict the use of dangerous pre-stored programs.
- Systems with files upload function need to have a malicious file detection and prevention mechanism.
2. Strengthen monitoring and analysis measures (identification, detection, protection)
- Import endpoint scanning and monitoring mechanism to provide real-time alerts and block malicious behaviors.
- Strengthen network behavior monitoring and system service record backup and analysis mechanisms.
- Establish a threat information output mechanism to detect suspicious threat sources and field weaknesses early.
3. Establish incident response mechanism (response & recovery)
- For the types of high-risk incidents that may occur (such as ransomware, personal data theft, APT intrusion, etc.), follow the NIST Incident Response Plan to establish an IR Playbook and formulate incident handling procedures (including pre-incident monitoring and analysis, mitigation and elimination during the incident, and post-incident recovery improvement, etc.) so that you can follow the instructions when an incident occurs.
Reference
[2] Keman Huang, Xiaoqing Wang, William Wei, and Stuart Madnick, 2023,“The Devastating Business Impacts of a Cyber Breach,” Harvard Business Review