Challenges
As hacker attack technology continues to evolve, advanced persistent threat (APT) techniques are becoming even more complex. More and more malicious programs are able to bypass EDR (Endpoint Detection and Response) and use legitimate tools to control endpoints. According to TeamT5's latest "APT Threat Landscape in APAC 2023" report, it is now common for hacker groups to use public or open source tools or exploit vulnerabilities of web servers to execute attacks.
The report also pointed out that in the entire Asia-Pacific region, Taiwan, South Korea and Japan are the countries most targeted by APT actors. In Taiwan, the government, IT industry, education and critical infrastructure sectors are the main targets of attacks. The reason why APT actors are so interested in the IT sector is that these IT companies possess good channels or privileges to access big companies or government entities through supply chain attacks.
To deal with endless APT attacks, how should enterprises or organizations effectively deal with them? The following case reveals how TeamT5 actually assists enterprise organizations to handle APT attacks. In this case, you may understand hacker attack techniques and how incident response measures reduce the losses to strengthen future cybersecurity defense.
Through TeamT5 endpoint security solution, suspicious APT attacks were discovered and timely assistance was provided.
Since APT attacks are hidden and targeting specific enterprises, there are usually no obvious signs. Threats must be found through threat intelligence or EDR with APT detection capabilities.
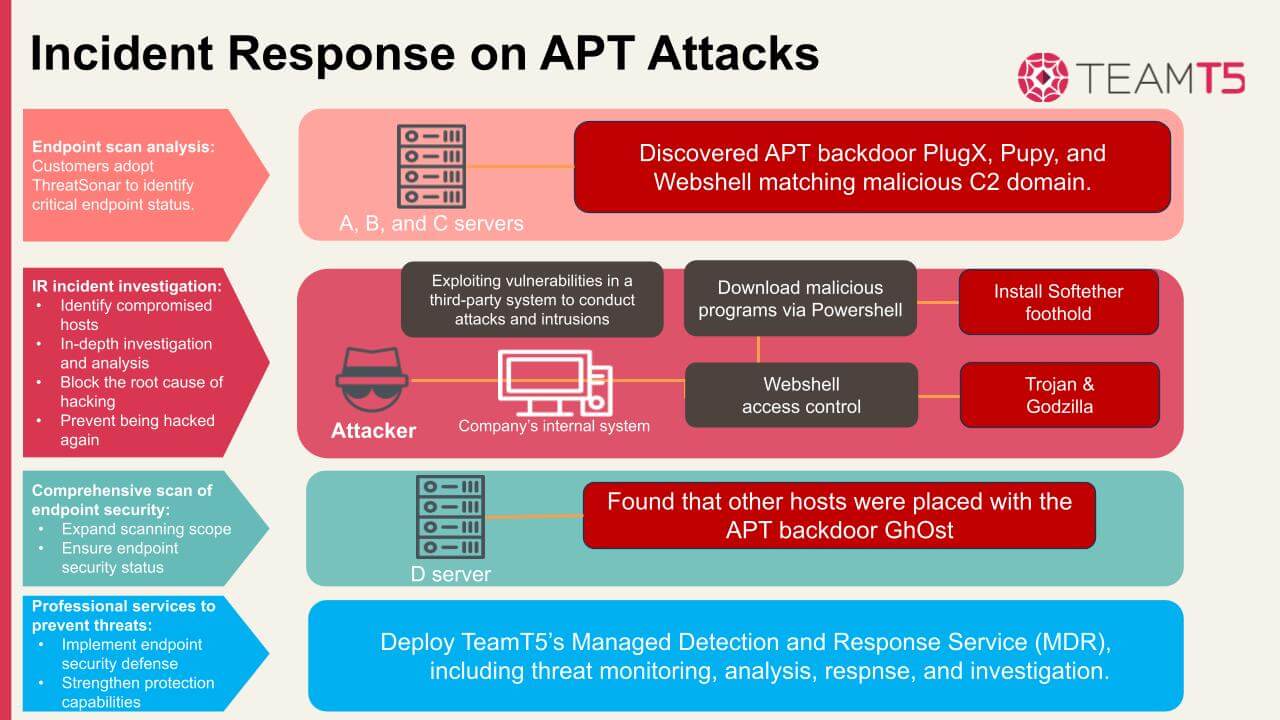
In a real case, a client used ThreatSonar, a threat forensic analysis platform developed by TeamT5, to conduct a scan of critical endpoints and analyze the scan results to understand whether there are potential threats. After inspection, it was gradually discovered that the hosts were installed with APT backdoors and Webshells. After receiving the detection report, TeamT5 immediately made further plans for the client, expanded scanning scope and analysis of endpoints in the field, and initiated the cybersecurity incident investigation service stage.
TeamT5’s Cyber Security Incident Response Team (CSIRT) assists clients in accessing the situation and the attacker's possible intrusion methods, and provides clients with immediate suggestions to block the attacker's control and proliferation to avoid affecting other digital assets.
Endpoint detection and analysis to understand the scope of attacks
In order to clarify the scope of attacks in the environment, TeamT5 helps clients take the following key actions:
- Key forensic analysis: Based on the circumstances of the case, the TeamT5 team identified the major compromised host. Per its operating system, forensic analysis by professional tools, and analysis of the network equipment communication log at the time of the incident, TeamT5 conducted incident-related investigations.
- Deploy endpoint scanning to identify the scope of attacks: By deploying ThreatSonar to perform endpoint scanning, it was found that the memory of a host hit the APT rule, triggering a high-risk (Level 5) threat alert. After analysis by TeamT5, it was confirmed that a backdoor program, a malicious threat, was placed into the memory along with threat information such as suspicious file paths and malicious C2 server lists. It is recommended that clients block malicious C2 servers and check whether the firewall has records of endpoints trying to connect to the servers.
Uncover the root cause of the incident and investigate the trajectory of the attack
Based on the incident investigation report generated by ThreatSonar and network record analysis, the TeamT5 team performed correlation investigations of on-site incidents to understand the attackers’ path and root cause of the incident:
- Analysis of critical endpoints’ scan results: A malicious threat is found in the connection record of an executable file on the field host, and the malicious C2 domain of the threat information was hit.
- Incident investigation to find out the root cause: After identifying the risk host, investigation and analysis were initiated to find out the hacker control chain. From the correlation between the Web Log and the Event Log of the system with abnormal conditions, it was discovered that as early as half a year ago, the system had been implanted with a Webshell by attackers. After the attackers took advantage of the system vulnerability of the third-party service to gain control, they then used Softether and a set of Trojans to establish footholds. Further tracing back on the attack incident, we learned that the attacker abused PowerShell commands for execution by SQL permissions, and summarized the accounts that may have been controlled, as well as the IP information of attack source.
- Comprehensive assessment of the endpoints’ security status: In order to ensure the security status of endpoints in the site, the scanning scope was expanded. From the memory analysis, it was found that other on-site hosts were injected with the GhOst backdoor program.
- Introducing professional cybersecurity monitoring services to strengthen cybersecurity protection: TeamT5 Managed Detection and Response Services (MDR) provide clients with one-stop services such as threat monitoring, analysis, response, and investigation, reducing the burden of enterprise cybersecurity operations while achieving comprehensive risk control.
Review cybersecurity strategies and strengthen cyber defenses
To prevent similar incidents from happening again, TeamT5 provides clients with the following cyber defense suggestions:
Block the sources of hacker control
take complete review of the security status of digital assets, confirm VPN equipment and system vulnerability patching, strengthen access control of critical hosts, and improve personnel's security awareness of phishing emails or website downloaders.
Strengthen monitoring and analysis measures
establish an endpoint security monitoring mechanism to provide real-time alerts and block malicious behaviors; confirm the settings of network communication rules or the settings of terminal connections.
Establish an incident response mechanism
Develop incident response procedures for the high-risk incidents that may occur, including pre-compromise monitoring and analysis, mitigation during the incident, and subsequent recovery and improvement, etc., so that they can be followed when an incident occurs.