In recent years, network attack methods have become more complex, and some have even bypassed traditional EDR defense mechanisms.
For example, the attack technique HookChain does not directly disable the API hook, but instead manipulates the API process to bypass the EDR monitoring function; this technology has an extremely high EDR detection bypass rate, with a demonstrated success rate of 88% [1]. In addition, there are various types of malware that damage EDR [2], as well as attack methods that bypass EDR defenses, such as abusing hardware breakpoints [3] and using low-privilege users [4].
The previous article in this series has analyzed how attackers bypass EDR and invade enterprise systems; this article will further explain how enterprises and organizations can respond, particularly through the use of compromise assessments.
How to effectively deal with attacks that bypass EDR
To effectively defend against hidden threats that bypass EDR detection, multi-faceted cybersecurity defense solutions must support and reinforce each other.
1. "EDR" detects abnormal behavior in real time
- Real-time detection through continuous monitoring
- Wide-range collection of OS events and process operations for further analysis
- Automatically detect and prevent suspicious behavior using rules and machine learning
2. Active “Threat hunting”
- Explore potential risks where necessary
- Actively discover known and unknown suspicious behaviors
- Analysts conduct detailed analysis of logs, etc. to identify undetectable threats
3. "Rapid Forensic" for cybersecurity status check
- When a cybersecurity incident occurs, detect it through lightweight digital forensic tools
- Sample check of memory and critical file status
- Detect anomalies early and determine whether a full investigation is needed
Therefore, in order to supplement the existing EDR detection and defense coverage, an intelligence-driven threat identification platform has become an indispensable solution. By collecting various data (such as logs and memory data) and analyzing the results, organizations can transform these insights into intelligence-driven threat hunting, effectively identifying latent and hidden threats that bypass EDR detection to strengthen the information cybersecurity posture.
At the same time, the threat forensics platform must be capable of collecting and analyzing live system memory data to detect traces of intrusions that traditional EDR solutions might easily overlook. From the perspective of the process from malware intrusion to execution, when the CPU is executing malware deployed in memory, EDR can detect and control suspicious behavior in real time. However, if you can identify and hunt for threats through regular memory scanning, you can prevent malicious code from being extracted into the memory early and block the execution of malicious software in advance.
TeamT5's intelligence-driven "ThreatSonar - Threat Forensic Analysis Platform" has memory scanning and forensics features. ThreatSonar can quickly detect APT attacks and cyber espionage activities based on the latest threat intelligence, improving cybersecurity protection effectiveness. At the same time, ThreatSonar can quickly and fully obtain critical data from disks and memory, conduct a comprehensive analysis of past and present behaviors, identify indicators of future threats, and quickly check whether there are any suspicious behaviors, allowing the cybersecurity team to effectively handle incidents. In addition, ThreatSonar does not require a cumbersome installation process and has the advantage of lightweight deployment. It can run on Windows, Linux or Mac OS, ensuring that it can be quickly deployed and used in large-scale environments.
ThreatSonar in Action
Many companies focus on the defense against APT attacks and unknown threats. In addition to installing EDR for timely threat detection, they also conduct regular intrusion assessments. From the previous analysis of the case of EDR bypass attack method, we can see that although the enterprise had EDR and anti-virus software installed, the attacker was able to disable EDR monitoring, allowing data to be stolen undetected for up to a year. In view of this, the company used the ThreatSonar threat forensics analysis platform to uncover potential threats and planned to conduct a compromise assessment on 10,000 endpoints within two weeks to quickly identify possible hacking paths and the scope of impact. The company implemented the following detection methods:
- Detect APT attack signatures with Yara rules (including IoC)
- Investigate fake documents impersonating specific organizations, 2,268 Ruby-related malicious files, Rokrat malware variants, API hook bypass
The testing process consists of five stages: "Environment Survey", "Deployment", "Scan & Auto-Analysis", "Research and Analysis", and "Reports":
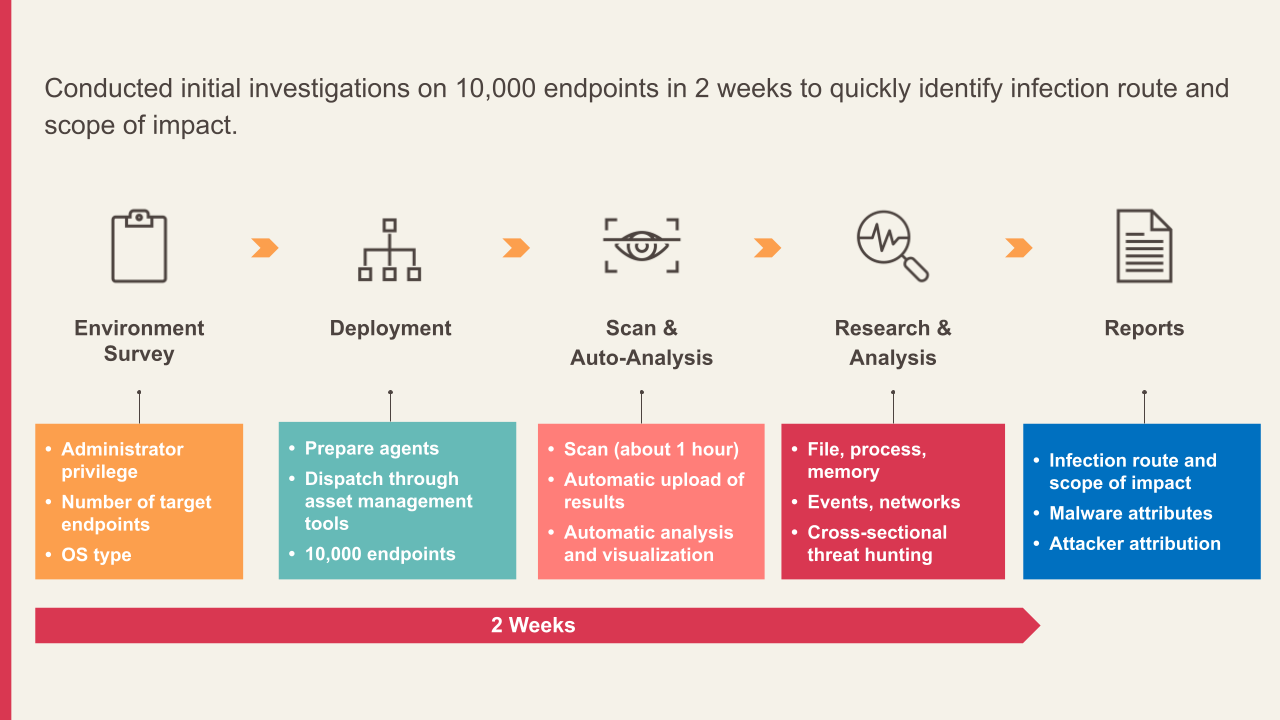

This survey shows the benefits of using a threat investigation tool like ThreatSonar:
- Accelerate investigation: In just two weeks, the main hacked devices, the scope of the hack, and the intrusion route can be identified.
- Minimize damage: Prevents the damage caused by information theft from expanding through rapid detection.
Conclusion
In order to effectively prevent attacks that bypass EDR detection, it is imperative to adopt effective corresponding defense mechanisms. Through the ThreatSonar threat forensics analysis platform, regular threat hunting and memory forensics can be achieved to realize multi-layered cybersecurity defense, while strengthening the ability to proactively discover potential threats in normal times.
Threat forensic analysis platform "ThreatSonar" is a solution developed by TeamT5 that combines threat intelligence analysis results with practical attack and defense experience to help the industry accurately grasp the source and spread of threats, hunt for unknown potential threats, strengthen in-depth defense, protect endpoint security, and avoid possible damage caused by future threats. ThreatSonar features include:
- Intelligence-driven threat forensics
- Lightweight deployment without affecting daily operations
- Offers the whole picture of the incident, shortening the investigation time
- Uncover the malicious programs hidden in the memory
- Threat hunting with visualization of correlating potential compromised endpoints
Welcome to contact us for a free trial.
Reference
[1] Cyber Security News, https://cybersecuritynews.com/hookchain-edr-evasion-technique/
[2] DARKREADING, https://www.darkreading.com/cyberattacks-data-breaches/novel-edr-killing-ghostengine-malware-stealth
[3] Cyber Security News, https://cybersecuritynews.com/bypassing-edr-detection-hardware-breakpoints/
[4] Cyber Security News, https://cybersecuritynews.com/bypassing-edr-as-standard-user/
[2] DARKREADING, https://www.darkreading.com/cyberattacks-data-breaches/novel-edr-killing-ghostengine-malware-stealth
[3] Cyber Security News, https://cybersecuritynews.com/bypassing-edr-detection-hardware-breakpoints/
[4] Cyber Security News, https://cybersecuritynews.com/bypassing-edr-as-standard-user/
(cover source:pexels)