In recent years, cyber attack methods have become more complex, and some have even bypassed traditional EDR defense mechanisms.
For example, the attack technique HookChain does not directly disable the API hook, but manipulates the API process, achieving an 88% success rate in circumventing EDR defensive layers, rendering them ineffective against this evasive approach [1]. In addition, there are various types of malware that damage EDR [2], as well as attack methods that bypass EDR defenses, such as exploiting hardware breakpoints [3] and leveraging masquerading and path obfuscation to disguise malicious payloads as legitimate processes [4].
In this series of articles, we will first analyze how attackers bypass EDR and invade enterprise systems; and in the other article, we will further explain the countermeasures that enterprises and organizations can take to deal with such attacks.
Attackers’ methods of bypassing EDR detection

EDR consists of the following elements:
- Agent: The software, installed on each endpoint, monitors system operations. It is responsible for receiving telemetry data collected by sensors and sending it to the management server for analysis.
- Management Console: Comprehensively analyzes collected data and identifies signs of attacks and incidents.
To detect signs of attack, EDR detection mainly focuses on: application and user behavior (such as the execution of suspicious programs and unusual privilege escalation); abnormal communication between the system and external (Command & control) servers; and analysis of registry changes, script execution, and abnormal behavior in memory.
However, attackers continuously develop new evasion techniques to bypass EDR detection, such as:
1. Stopping the Agent itself: Forcefully terminate the EDR agent
The specific method is to use BYOVD (Bring Your Own Vulnerable Driver), where the attacker implants a vulnerable core driver into the target system to elevate permissions. This allows the attacker to access the core, disable EDR, and then carry out malicious actions.
The specific method is to use BYOVD (Bring Your Own Vulnerable Driver), where the attacker implants a vulnerable core driver into the target system to elevate permissions. This allows the attacker to access the core, disable EDR, and then carry out malicious actions.
2. Stopping the logging function: Disable logging and delay detection
Attackers may also disable Event Tracing for Windows (ETW), a mechanism to record Windows system operations, to prevent records of suspicious operations from being left behind. This will prevent EDR from detecting signs of attack and greatly affect EDR's detection capabilities.
Attackers may also disable Event Tracing for Windows (ETW), a mechanism to record Windows system operations, to prevent records of suspicious operations from being left behind. This will prevent EDR from detecting signs of attack and greatly affect EDR's detection capabilities.
Attackers can also interfere with normal EDR operations by:
3. Disabling EDR monitoring: Remove endpoints from EDR monitoring scope to bypass detection
Since APIs are interfaces that allow programs to use functions provided by the operating system and applications, EDRs usually connect to important system APIs to monitor signs of attacks. Attackers can avoid EDR monitoring by disabling API hook techniques, thereby creating an environment where malware can run freely.
Since APIs are interfaces that allow programs to use functions provided by the operating system and applications, EDRs usually connect to important system APIs to monitor signs of attacks. Attackers can avoid EDR monitoring by disabling API hook techniques, thereby creating an environment where malware can run freely.
4. Impersonating the call stack of a function: Make malware look like legitimate software
Call Stack Spoofing is a malicious technique that spoofs the call stack (i.e. the execution history of a program) to make the attacker's actions appear to be executed from a trusted program. Attackers use this method to make it easier for EDR and cybersecurity products to ignore anomalies and fail to detect the attacker's malicious actions.
Call Stack Spoofing is a malicious technique that spoofs the call stack (i.e. the execution history of a program) to make the attacker's actions appear to be executed from a trusted program. Attackers use this method to make it easier for EDR and cybersecurity products to ignore anomalies and fail to detect the attacker's malicious actions.
In addition, methods to leverage areas outside of EDR monitoring include:
5. Exploiting areas without EDR monitoring by default and then abusing certain software behaviors not typically monitored by EDR
An attacker could also abuse Windows fibers, a lighter-weight program switching mechanism than threads, but some EDRs do not monitor this operation. Attackers can exploit this feature to execute malicious code while avoiding EDR detection.
An attacker could also abuse Windows fibers, a lighter-weight program switching mechanism than threads, but some EDRs do not monitor this operation. Attackers can exploit this feature to execute malicious code while avoiding EDR detection.
Finally, attackers may also resort to tactics to disrupt or block EDR server communications, such as:
6. Block communication with EDR server: prevent the transmission of endpoint detection results and disable monitoring
EDRs typically send detection results when communicating with management servers, but attackers can block this communication and isolate the EDR to prevent it from reporting anomalies. This effectively prevents the management from understanding the status of the endpoint and results in a loss of monitoring capability, creating an environment in which attackers can operate more freely.
EDRs typically send detection results when communicating with management servers, but attackers can block this communication and isolate the EDR to prevent it from reporting anomalies. This effectively prevents the management from understanding the status of the endpoint and results in a loss of monitoring capability, creating an environment in which attackers can operate more freely.
By using these methods—individually or in combination—attackers can bypass EDR detection and remain hidden for extended periods, giving them time to carry out malicious activities. The consequences can be severe, including data breaches, theft of trade secrets, ransomware-related disruptions, and damage to critical systems. Such incidents can also erode trust among customers and partners. The longer an attack goes undetected, the greater the impact, making response and recovery significantly more difficult for organizations.
How attackers break into systems
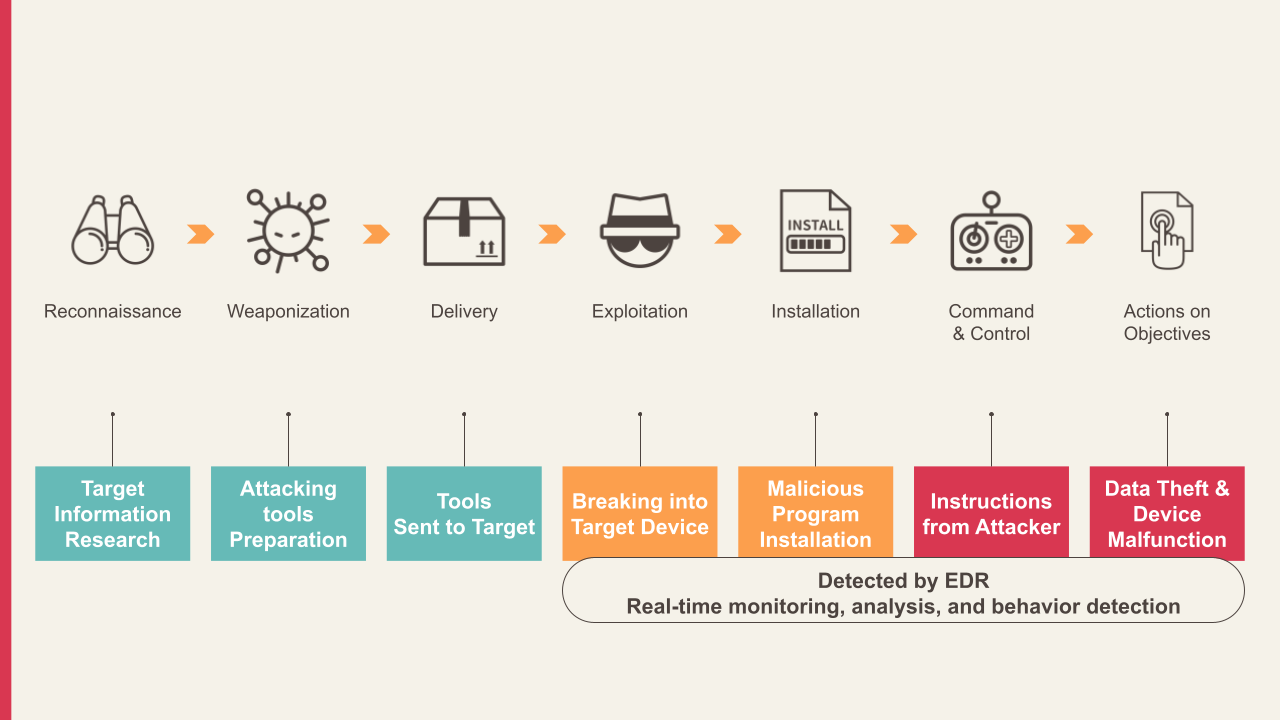
From the 7 steps of the cyber attack chain, you can understand how attackers who bypass EDR detection can penetrate the system and achieve their ultimate goal:
- Reconnaissance: The attacker first investigates information about the target (individual or organization).
- Weaponization: The attacker's preparation of attack tools and malware, as well as the means to use them after a breach.
- Delivery: Delivering the prepared attack tool to the target endpoint.
- Exploitation: Executing dropped malware or other attack files and exploiting vulnerabilities to penetrate the target system.
- Installation: The installation of malicious programs that allow attackers to gain long-term access.
- Command & Control: The attacker remotely controls the hacked endpoint through an external Command & control (C&C) server.
- Actions on Objectives: The attacker's goal is to steal information, disrupt business operations, or deploy ransomware.
Traditional antivirus software and firewalls can respond to attacks from attackers using known malware or specific network routers in the above-mentioned process from "delivery" to "exploitation", while EDR can prevent attacks from happening through real-time monitoring, analysis and behavioral detection. However, attackers continue to improve methods to bypass EDR mechanisms, such as: fileless malware, attacks that abuse legitimate tools, credential theft, and lateral movement within internal networks.
From the EDR defense mechanism and the attack methods used by attackers to bypass the mechanism, we can understand the core of the EDR defense mechanism, which is to instantly detect suspicious behavior of endpoints and analyze and block malicious operations. In order to prevent the aforementioned attackers from bypassing EDR defenses, an effective threat hunting solution is needed to provide accurate and effective defense by detecting abnormal behavior of endpoints.
Conclusion
As employees of corporate organizations use endpoint devices such as laptops more frequently to perform daily work, measures to address the aforementioned threats become even more necessary. Continue reading this series of articles "How Cybercriminals Bypass EDR — And What Your Company Should Do (2)" to learn how enterprises and organizations can use compromise assessment to effectively respond and reduce cybersecurity risks.
Welcome to contact us for a free trial.
Reference
[1] Cyber Security News, https://cybersecuritynews.com/hookchain-edr-evasion-technique/
[2] DARKREADING, https://www.darkreading.com/cyberattacks-data-breaches/novel-edr-killing-ghostengine-malware-stealth
[3] Cyber Security News, https://cybersecuritynews.com/bypassing-edr-detection-hardware-breakpoints/
[4] Cyber Security News, https://cybersecuritynews.com/bypassing-edr-as-standard-user/
[2] DARKREADING, https://www.darkreading.com/cyberattacks-data-breaches/novel-edr-killing-ghostengine-malware-stealth
[3] Cyber Security News, https://cybersecuritynews.com/bypassing-edr-detection-hardware-breakpoints/
[4] Cyber Security News, https://cybersecuritynews.com/bypassing-edr-as-standard-user/
(cover source:pexels)