As hackers’ attack tactics, techniques, and procedures (TTPs) evolve rapidly, enterprise's cybersecurity teams need a more up-to-date security defense platform that can identify the latest threats and hunt threats that attempt to bypass detection. However, to quickly and effectively defend against new types of attacks, it is not enough to rely solely on the rule-based threat detection technology used by most EDRs.
How can we identify the latest threats in a timely manner?
There are many known threat alarms, but the latest threats are sneaking in quietly. How can we identify them quickly and effectively?
General EDR detects the threats based on known indicators of compromise (IoC). IoCs may include information about the attack, such as malware type, C2 IPs, malware signatures, and other technical information that can help security teams determine whether an attack has occurred. At the same time, YARA rules are created per the file or memory attributes to track malicious programs.
However, for security personnel, thousands of abnormal incident alerts are received every day through EDR detection, and it is still a big challenge to effectively identify the real high-risk incidents. At the same time, if you want to successfully detect the latest threat techniques, you must frequently update IoCs to defend against zero-day attacks. This will undoubtedly become a daily burden for security personnel who have been immersed in threat identification and analysis for a long time.
Sigma rule detection makes the latest threats invisible
Similar to Yara rules that use IoCs to help identify and classify malware, Sigma rule detection can be specified by security personnel to compare common threats in logs to enhance incident detection capabilities.
The biggest advantage of Sigma rules is that they adopt a standardized format, which breaks the barriers of different SIEM (Security Information and Event Management) platforms using specific formats or languages. It allows security personnel to write a rule once and then share and apply it through a standard format. In different SIEM solutions, there is no need to rewrite rules, which improves detection efficiency and reduces the burden on security personnel.
A Sigma rule is an open-source standard, which allows network security experts to share and improve them through sharing platforms such as GitHub. On the one hand, it encourages everyone to share knowledge and exchange through a public environment. On the other hand, it can enable novices and experts to contribute their experience and learn from each other, thereby narrowing the gap in cybersecurity skills and alleviating the pressure that corporate organizations generally face a shortage of security personnel and urgently need to improve their professional capabilities.
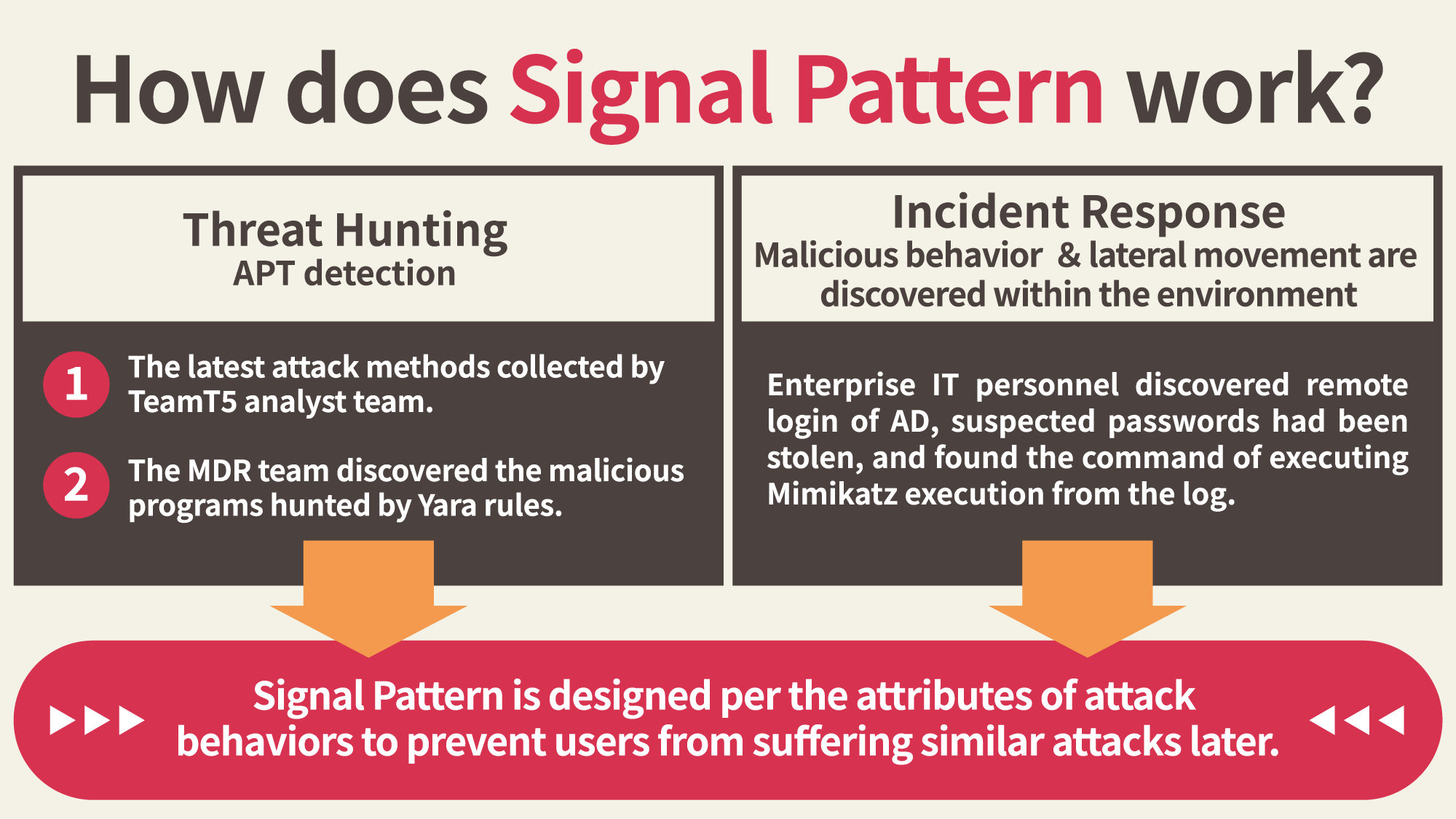
Signal Pattern of ThreatSonar grasps threat "signals"
Compatible with Sigma rules, TeamT5 transforms its long-term research and analysis of hacker attack behaviors and the latest threat attack methods into ThreatSonar's latest Signal Pattern detection engine, which uses behavioral rules to instantly detect whether there are suspicious programs on the endpoints.
ThreatSonar's Signal Pattern is researched and created by TeamT5 incident response experts and analysts. It can not only respond to newly revealed threats more quickly, but is also compatible with the open source Sigma rule standard. The Signal engine combines real-time collection of endpoint behavior logs and a new type of detection mechanism. This way, TeamT5's latest incident response experience and intelligence research can be integrated with the ThreatSonar detection engine to quickly respond to new types of threats or attack methods.
What is a Signal Pattern?
"Signal" (Sigma-based Threat Analytics Local-side Monitoring) echoes the meaning of "Sonar, " part of the name “ThreatSonar”. When using sonar to detect attacks initiated by adversaries, it can track whether there are suspicious “signals” on the endpoints. Even if the signal is weak or seems insignificant, by correlating different suspicious signals, the malicious behavior of hackers can be found in the early stage. Once a high-risk threat is identified by ThreatSonar's Signal Pattern, incident alerts are immediately sent, allowing users to take prompt action on the visualized user interface of ThreatSonar to prevent further attacks.
Benefits of Signal Pattern:
- Timely defense: TeamT5’s professional team quickly updates rules to effectively defend against the latest threats and zero-day attacks.
- Supports on-premise scanning: No network restrictions, quick response to attacks.
- Visualization: If the malicious attacks are hunted by rules, the user can grasp the incident trajectory on the Incident Report page.
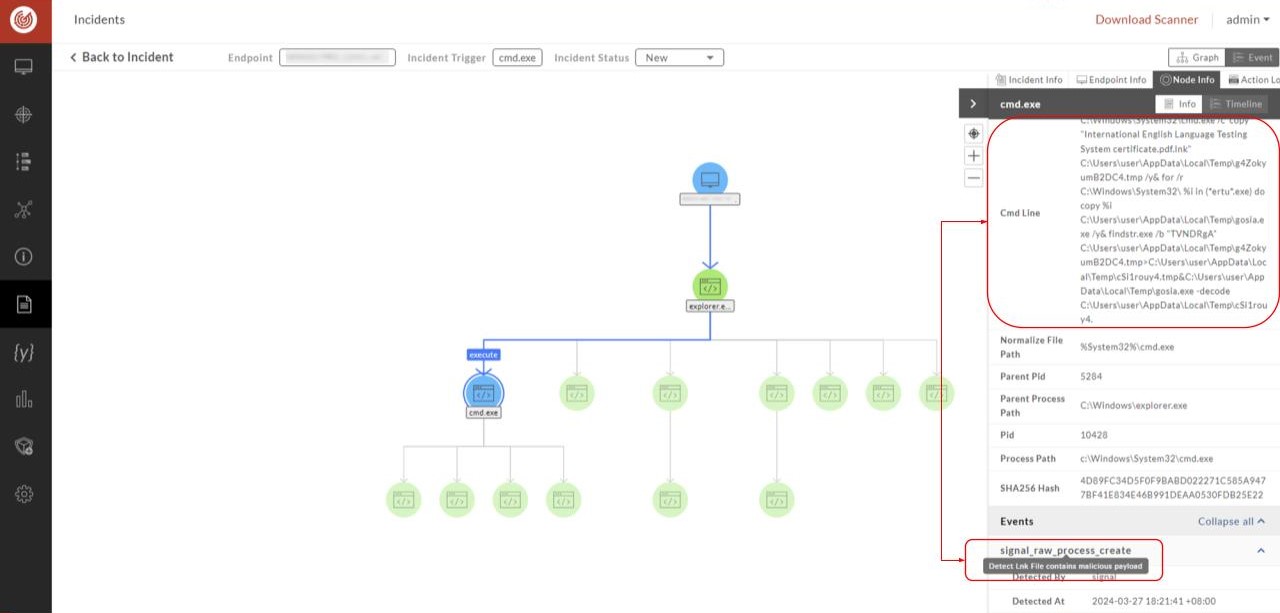
In summary, with the latest intelligence, significant vulnerabilities, and recent international cyber attacks that TeamT5 has obtained and researched, ThreatSonar's Signal Pattern is updated in a timely manner, allowing enterprises and organizations to immediately defend against hackers that their industry may currently encounter to reduce the risk of being hacked.
TeamT5 consists of top cyber threat analysts. Leveraging our geographic and cultural advantages, we have the best understanding of cyber attackers in Asia Pacific. TeamT5 is frequently invited to share insights at top cybersecurity conferences. Our threat intelligence research expertise and solutions are recognized as the 2023-2024 Company of the Year Award in Taiwanese Threat Intelligence by Frost & Sullivan.Contact us and know more of intelligence-driven cybersecurity solutions - https://teamt5.org/en/contact-us/.
(cover source:pexels)