Introduction
Over the last few years, Network Attached Storage (NAS) has seen a dramatic increase in popularity, especially during the pandemic. It is now commonplace to see a NAS box in the office of most small or medium businesses.
With the rise of these NAS servers, we have begun to see a huge increase in the number of DDNS domains associated with popular NAS providers such as Synology and QNAP.
In fact, during our research, we were able to estimate that there were at least three million active NAS units from Synology available on the world wide web. QNAP, by contrast, had a much lower market share of only ten thousand.
More NAS Servers = More Attacks
Unsurprisingly, this increase in NAS servers has seen a corresponding increase in cyberattacks. Perhaps the most famous to date was the Synolocker ransomware attack of 2014.
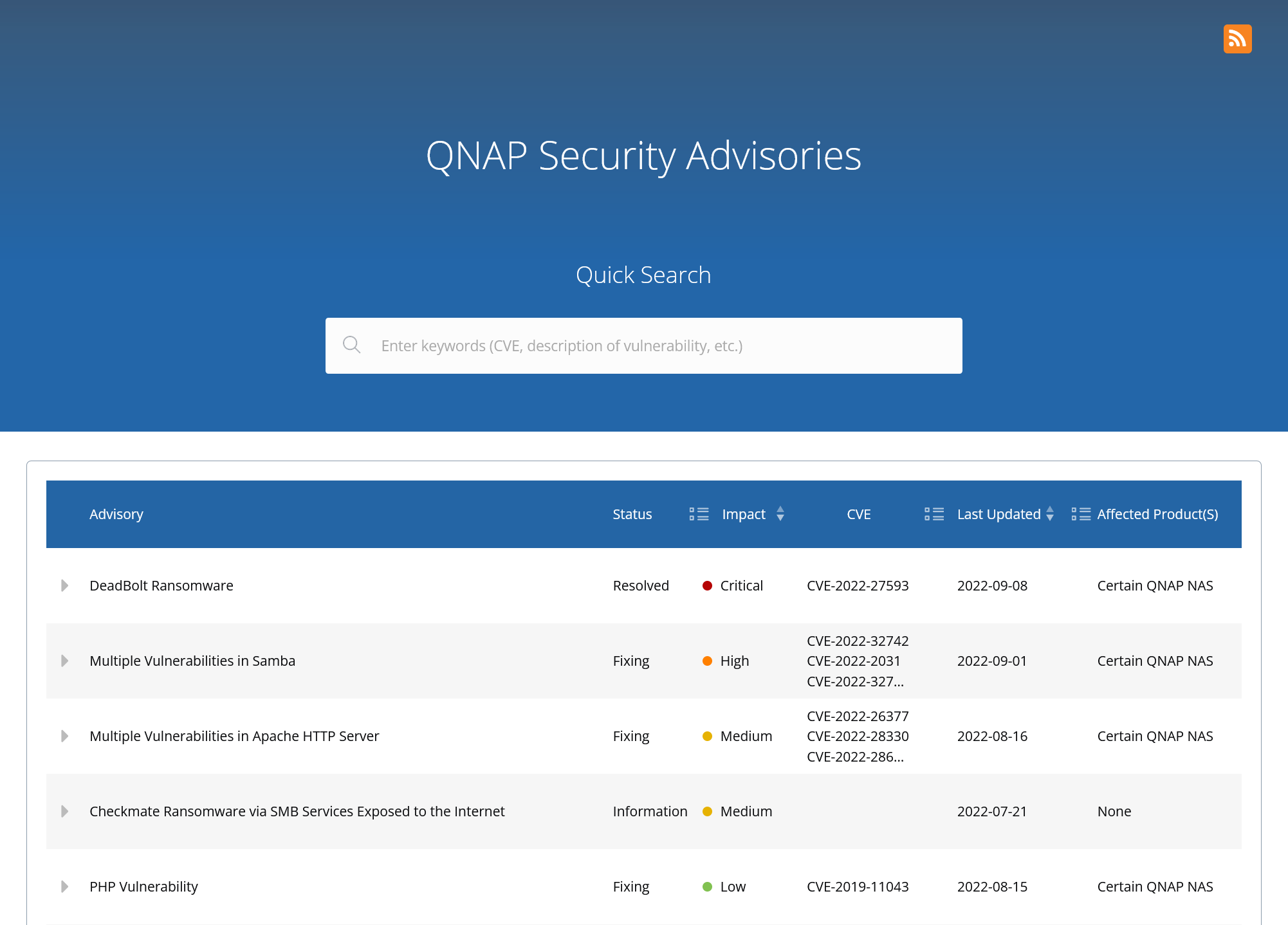
And, in the last 12 months, we can see that QNAP has published at least 37 advisories marked with a severity level between Medium to Critical. Specifically, these mentioned several ransomware campaigns involving: -
In addition, other types of malware or PUPs such as crypto miners and/or botnets were spotted on these systems.
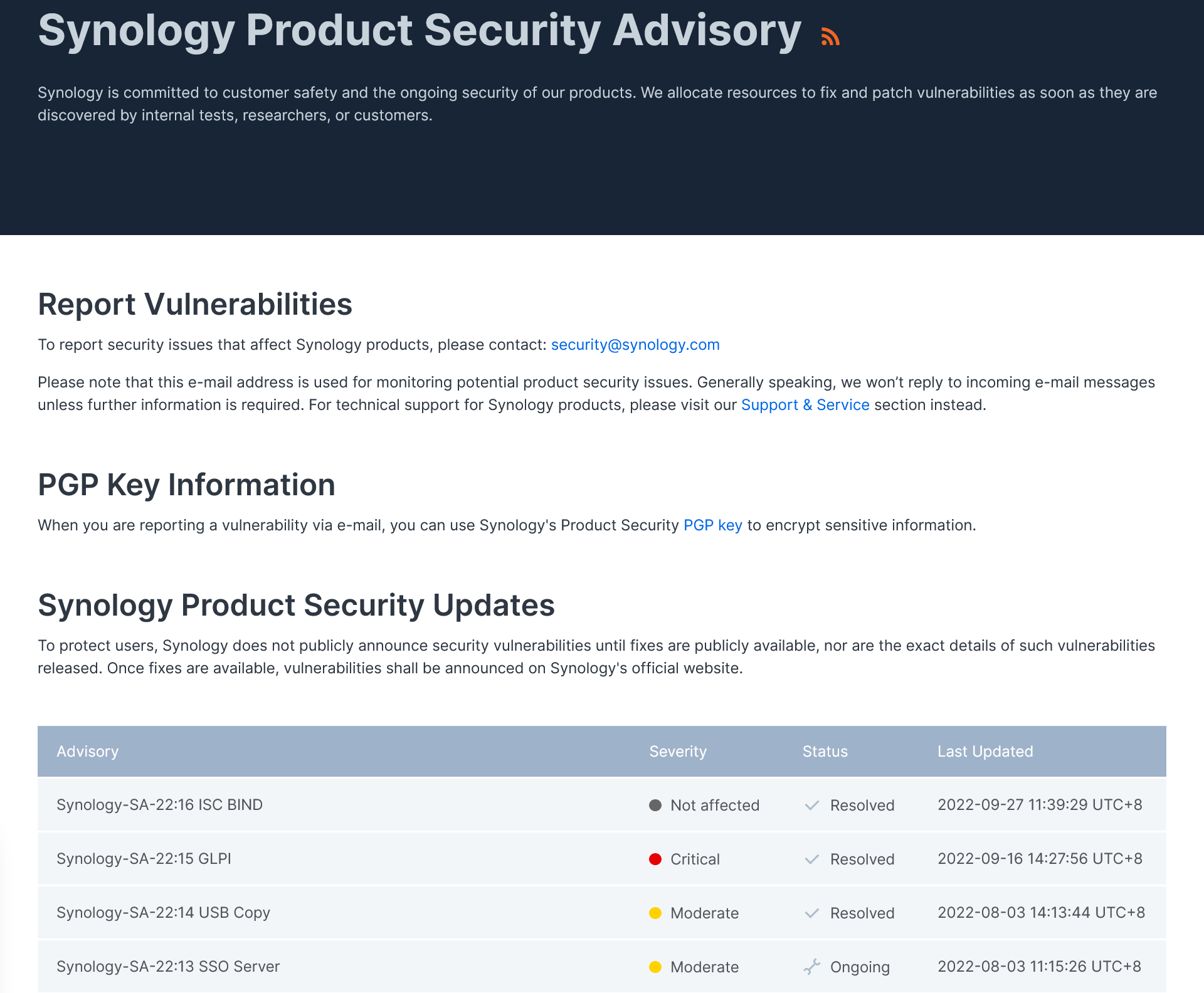
Meanwhile, in the same timeframe, Synology had published around 18 advisories marked between Moderate to Critical.
And, whilst it is clear that Synology NAS devices suffered from fewer security incidents than QNAP, they were still unfortunately targeted by ransomware gangs that abused the critical Netatalk-related vulnerability.
Xpenology AND QuickConnect
Unfortunately, Synology also had another issue to worry about - Xpenology, also known as 黑群暉 in the Taiwanese community. In a nutshell, this custom bootloader allows non-standard hardware to boot into Synology's Linux-based DSM (Disk Station Manager) system.
On top of Xpenology, Synology also had to worry about the emerging threat of QuickConnect abuse.
QuickConnect allows the NAS to be opened to WAN without any additional port forwarding setup, and the NAS is assigned a custom subdomain under
synology.me or other QuickConnect-related domains during this process.Normally, QuickConnect requires a matching combination between the NIC MAC address and the serial number in order to function. However, the community at large had figured out a way to generate the relevant credentials required to bypass this check a few years back, though most of them are likely patched by now.
Suspicious Activity in NAS Servers
Why specifically does this matter, though? During our investigations against cases that were related to various Chinese adversaries, we found that some of the IP addresses related to the incidents were directly related to various Synology QuickConnect-related subdomains.
For example, at some point in our investigation, we stumbled across the IP
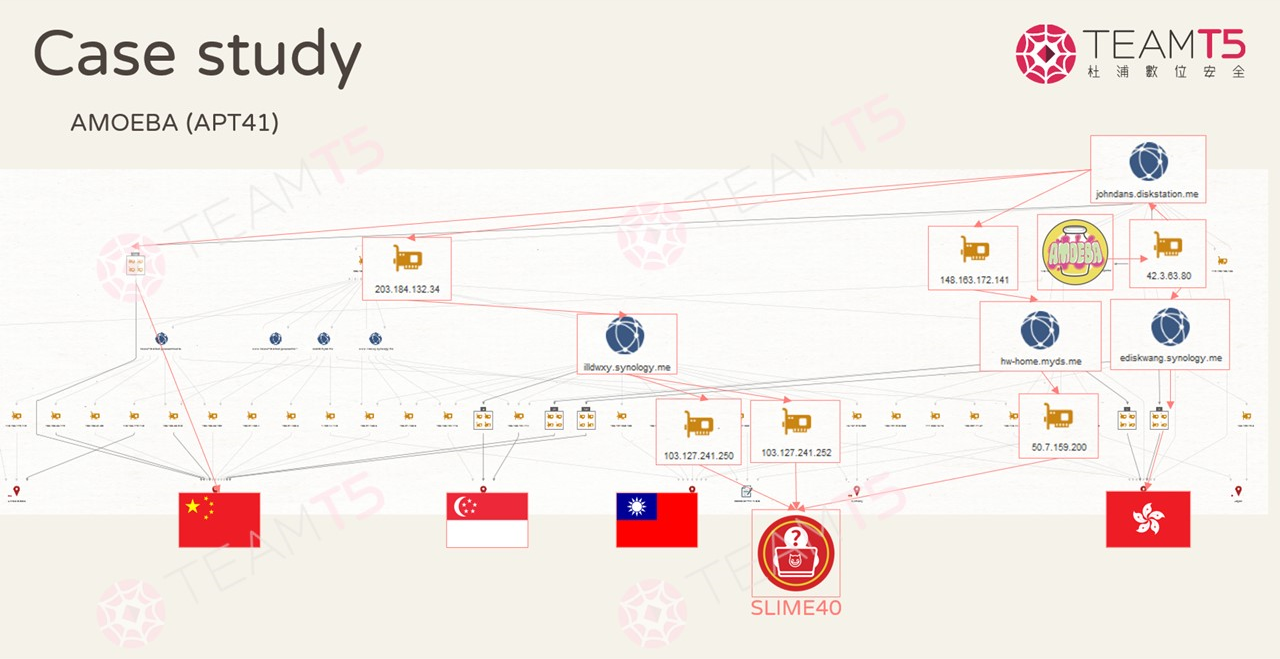
42.3.63[.]80. This IP address was resolved to johndans[.]diskstation.me and ediskwang[.]synology.me shortly prior to the security incident. Both these subdomains had extremely suspicious DNS records, jumping in rapid succession between various IP addresses from China and Hong Kong.By following the relevant IP addresses, we realized some of the IP addresses resolved were previously discovered in other cases that were directly linked to various Chinese adversaries, such as Amoeba (APT41) and SLIME40 (FamousSparrow). Based on our internal research, we came to the conclusion that these subdomains were likely normal NAS servers taken hostage by the APTs.
The discovery we made above led us to speculate on other possibilities. What if a threat actor were to host their own Synology proxy stations using both of the attack vectors mentioned above?
To validate our suspicion, we gathered around ~10,000
synology.me and ~5,000 myqnapcloud.com subdomains as our dataset and filtered them based on the following conditions,- Is the NAS hosted on a known VPS ASN?
- Is the NAS subdomain seen traveling across various different country?
- Are multiple NAS subdomains resolving to the same IP addresses?
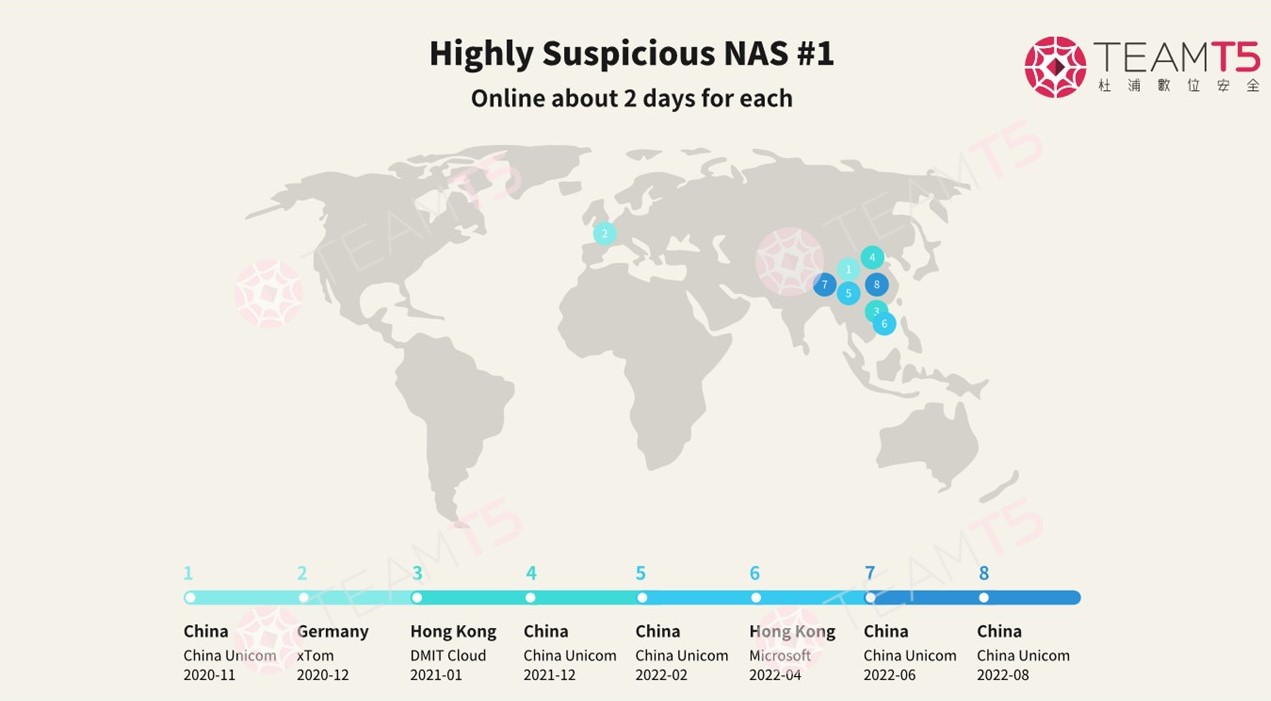
From the queries, we noticed there were indeed several suspicious-looking NAS DDNS subdomains. For instance, in the following example, the NAS was seen traveling between EU and the East Asian region for several years with the resolve record for each being as short as two days. The device was hosted between various cloud providers, such as xTom, Microsoft Azure, and DMIT Cloud.
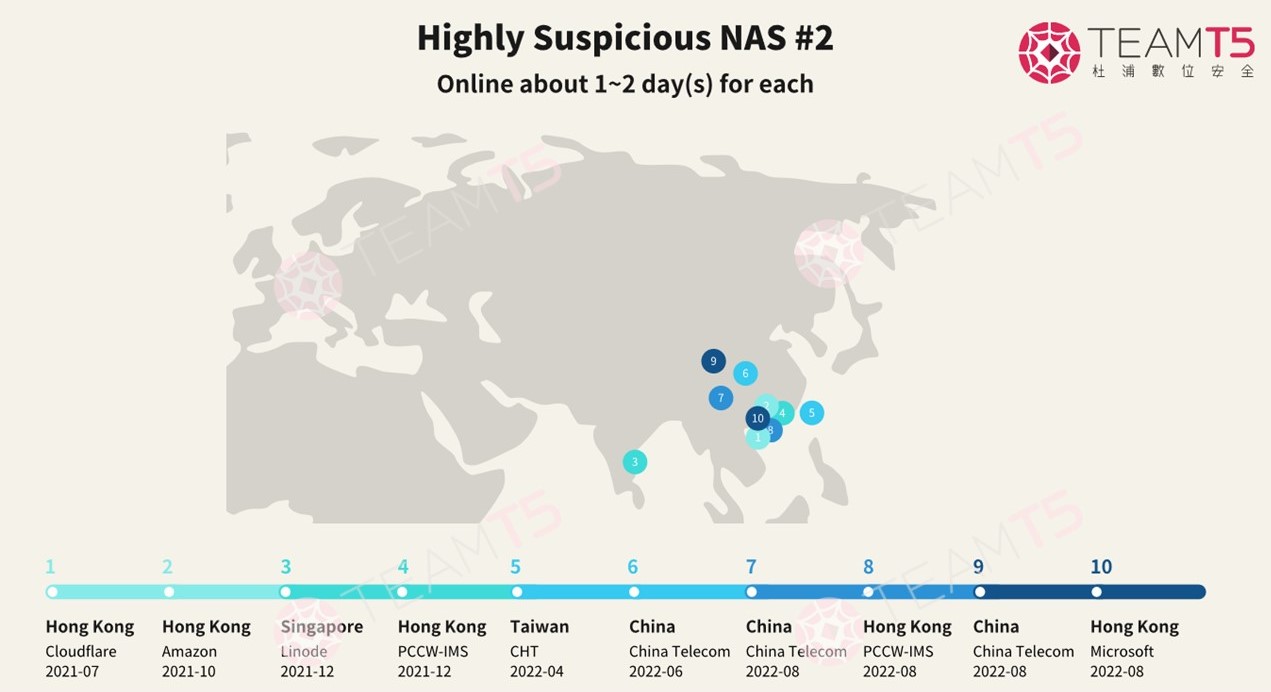
In another instance, we noticed one of the NAS devices was traveling between Hong Kong, Singapore, Taiwan, and China at various IP addresses owned by cloud hosting providers such as Linode, AWS, Cloudflare, Microsoft Azure, and more.
While we cannot conclusively attribute any of these NAS instances as necessarily “malicious” - as these instances could have simply be behind a network-wide VPN in some home solutions - we could at the very least mark them as relatively suspicious compared to the standard use cases of NAS DDNS.
The Threat Landscape is Evolving. Makes sure you keep up.
To sum up this research, we have looked at the traditional threat landscape that is present in the NAS industry (e.g., ransomware, cryptominers, PUPs, etc.) and how it may evolve into another type of threat with the use of convenient features such as QuickConnect.
One thing is clear.The threat landscape of NAS devices may still evolve over time. As such, we encourage our readers and our customers to regularly update their device firmware and to check if there are any irregularities with their home devices.
The research is first published in HITCON PEACE 2022. This blog is the key abstract of our speech in HITCON PEACE 2022, "Your NAS is not my BOT".
*Image courtesy of Pexels
Related Post
Events
2022.05.15
【Black Hat Asia 2022】Chinese APTs are Looting the Online Entertainment Industry, TeamT5 Researchers Publish Analysis at Black Hat Asia
threat hunting, cyber threat intelligence
Events
2022.05.15
【Black Hat Asia 2022】New Trend of Modular Backdoor and APT Attacks, TeamT5 Researchers Publish Analysis at Black Hat Asia
threat hunting, cyber threat intelligence
Threat Intelligence
2022.05.09
Hiding in Plain Sight: Obscuring C2s by Abusing CDN Services
cyber threat intelligence, threat hunting