Understanding and countering threats effectively requires precise, timely, and context-rich intelligence. This is where localized intelligence becomes a critical asset. At TeamT5, we specialize in leveraging localized intelligence to provide unparalleled insights into cyber threats, particularly those emanating from the APAC region. But what exactly is localized intelligence, and how is it crafted?
The Concept of Localized Intelligence
Localized intelligence refers to the collection and analysis of information directly from the regions where specific cyber threats originate. Imagine you're an organization or a government entity aiming to thwart attacks from a terror group based in the Middle East. Would you rely on intelligence from a company entrenched in the region, familiar with the language, culture, and ongoing activities, or from a company situated thousands of miles away with limited exposure to these threats? The choice is clear: proximity and direct engagement with the threat landscape are invaluable.
Taiwan: A Hotspot for Cyber Threats
To illustrate the power of localized intelligence, consider Taiwan. In the first half of 2023, Taiwan experienced an astonishing 15,000 cyber attacks per second. This relentless onslaught is a direct result of its geopolitical situation, making Taiwan a unique vantage point for gathering cyber threat intelligence. At TeamT5, we harness this continuous exposure to cyber threats to develop first-hand, accurate, and timely intelligence on adversaries targeting the APAC region.
Challenges Faced by Western Organizations
Western organizations often struggle with gathering detailed intelligence on overseas adversaries for several reasons:
- Geographical Distance: Being far from the source of threats means fewer attack instances to study, resulting in less comprehensive data.
- Cultural and Language Barriers: Understanding the nuances of an adversary's communication, tactics, and motivations requires fluency in their language and deep cultural insights.
- Limited Access: Accessing forums and chat rooms where adversaries plan and discuss their activities can take years of reputation-building, a process challenging for distant organizations.
The TeamT5 Approach to Localized Intelligence
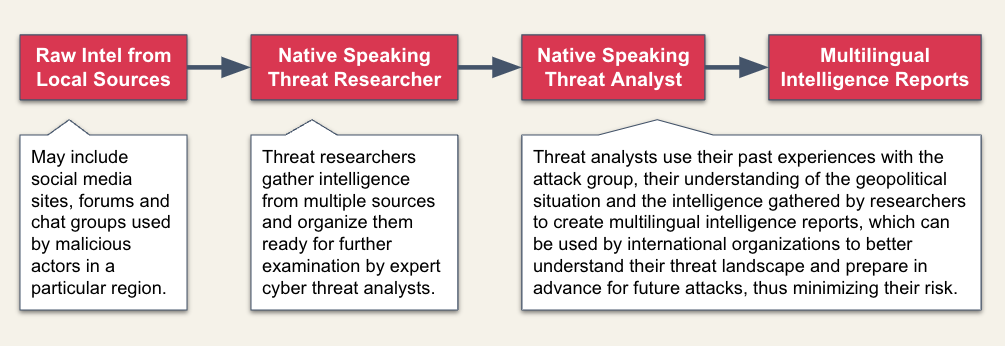
At TeamT5, our methodology for creating localized intelligence is rigorous and multifaceted:
1. Data Collection from Frequent Attacks: We gather extensive data from previous attacks, including logs, sample malware, and telemetrics. This data serves as the foundation for our intelligence reports.
- Native Expertise: Our threat researchers are native speakers of the languages used by adversaries and have a deep understanding of the local culture. This expertise enables them to decipher coded messages and signatures that would otherwise go unnoticed.
- Long-term Engagement: Building trust and gaining access to closed forums and chat rooms used by adversaries requires long-term commitment and meticulous reputation building.
- Comprehensive Analysis: Our analysts synthesize the gathered data, combining their understanding of the geopolitical landscape with the latest intelligence to produce actionable reports.
Components of Localized Intelligence
Localized intelligence from TeamT5 includes several critical elements:
- Target Scope: Identifying which regions, countries, and industries are being targeted.
- Tactics, Techniques, and Procedures (TTPs): Detailing the methods and tools used by adversaries.
- Command and Control (C&C) Infrastructure: Analyzing the infrastructure adversaries use to orchestrate their attacks.
The Power of Localized Intelligence in Practice
Take, for instance, TeamT5’s campaign tracking report.

Each Campaign Tracking Report report includes:
- Research Highlight: A summary of the report’s key topics.
- Target Scope: Information on the targeted regions and sectors.
- TTPs: Insights into the adversaries' latest techniques and malware.
- C&C Infrastructure: Details on the infrastructure supporting the attacks.
- Special Topics: In-depth case studies on specific attack campaigns.
Utilizing Localized Intelligence
Organizations can leverage localized intelligence in various ways. Some prefer manual review of intelligence reports, while others integrate indicators of compromise into automated detection systems. The optimal approach combines both methods, allowing for proactive threat prevention and informed risk management.
Conclusion
Localized intelligence is a cornerstone of effective cyber threat defense, providing the detailed, contextual understanding necessary to counter sophisticated adversaries. At TeamT5, we are committed to delivering the highest quality localized intelligence to help organizations worldwide stay ahead of emerging threats. For more comprehensive insights, consider downloading our white paper, "Understanding Cyber Threat Intelligence and the Cyber Threat Landscape with TeamT5”.
Learn more about how localized intelligence can help your organization by contacting us today!
(cover source: pexels)