In recent years, with the rapid increase in software adoption, the challenge of managing vulnerabilities has reached unprecedented levels. The evolution of digitalization has ushered in a new era of productivity and efficiency, but alongside it, a surge in potential security risks.
The Landscape of Vulnerability Management
The digital transformation of enterprises has significantly expanded the attack surface, making comprehensive vulnerability management a daunting task. The integration of third-party open-source tools into development processes has further complicated this landscape, as each tool brings its own set of vulnerabilities that can potentially be exploited by malicious actors.
Challenges in Prioritization
One of the greatest hurdles faced by cybersecurity professionals today is effectively prioritizing vulnerabilities. The sheer volume of information and the constant influx of potential threats often create a cacophony of alerts, making it difficult to distinguish critical issues from background noise. This complexity demands sophisticated solutions that not only identify vulnerabilities but also prioritize them based on their severity and potential impact.
Introducing ThreatVision Vulnerability Solutions: A Proactive Approach to Vulnerability Management
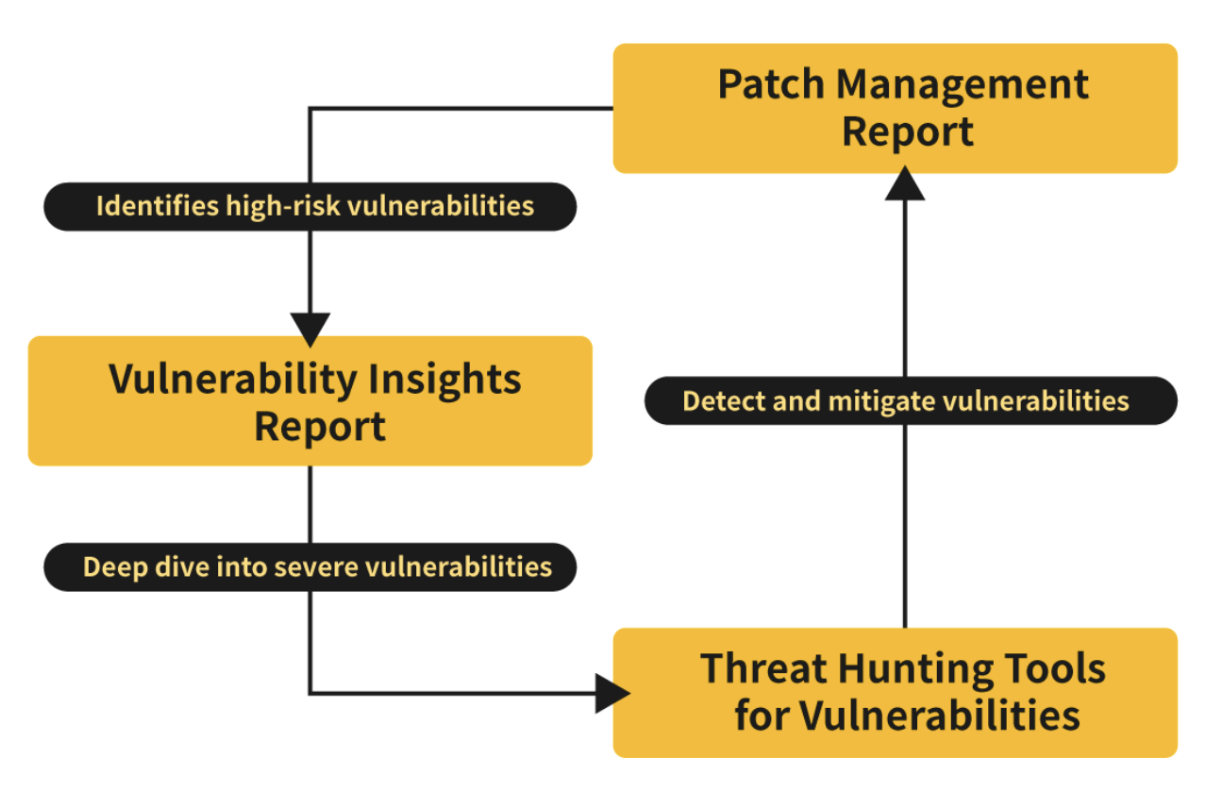
Patch Management Report (PMR)
At TeamT5, we understand the urgency of addressing high-risk vulnerabilities promptly. Our Patch Management Report provides weekly updates summarizing approximately 100 critical vulnerabilities. These reports are meticulously curated by analysts, who evaluate each vulnerability's proof of concept, risk assessment, and real-world implications. Subscribers can thus streamline their patch management efforts, focusing on vulnerabilities most susceptible to exploitation.

Vulnerability Insights Report (VIR)
Complementing the PMR, our Vulnerability Insights Report zooms in on a single critical vulnerability from the PMR, offering in-depth analysis, exploit scenarios, and global incident highlights. This report not only arms stakeholders with remediation strategies but also equips them with proactive mitigation techniques for vulnerabilities that cannot be immediately patched.
Threat Hunting Tools
Our arsenal includes cutting-edge threat hunting tools developed by analysts. These tools, incorporating YARA Rules, SNORT Rules, SIGMA Rules, and various scripts, enable proactive detection of vulnerability exploitation behaviors within client networks. By swiftly identifying vulnerabilities being actively exploited, organizations can promptly mitigate risks and fortify their defenses.
Benefits of ThreatVision’s Vulnerability Solutions
- Timely Action: By leveraging ThreatVision's reports and tools, organizations can swiftly confirm and mitigate vulnerabilities before they can be exploited.
- Comprehensive Coverage: From comprehensive patch management insights to detailed vulnerability analyses, ThreatVision offers a holistic approach to safeguarding digital assets.
- Proactive Defense: Armed with actionable intelligence from ThreatVision, cybersecurity teams can proactively defend against emerging threats and minimize potential damage.
Summary
Staying ahead of vulnerabilities is not just a strategy but a necessity. With ThreatVision, TeamT5 empowers enterprises to navigate the complexities of vulnerability management effectively. By prioritizing critical vulnerabilities and providing actionable insights, ThreatVision ensures that organizations can safeguard their digital infrastructure against evolving threats.
At TeamT5, we remain committed to advancing cybersecurity practices, helping enterprises mitigate risks, and empowering them to thrive in an increasingly digital world. Stay secure with ThreatVision and stay ahead of vulnerabilities.
Learn more about ThreatVision and enhance your cybersecurity strategy with TeamT5 today.
Contact us to schedule a consultation or subscribe to our reports for proactive vulnerability management.
(cover source: pexels)