Businesses face increasingly complex and frequent online threats. This surge in cyber threats poses a significant challenge to network security personnel, who must navigate a constant stream of alerts and incidents. Without a clear understanding of these threats, companies risk making incorrect judgments that can lead to wasted resources and serious damages. Here’s how ThreatVision’s Indicators of Compromise (IoCs) can make a substantial difference.
Overcoming Cyber Threats is Hard...
As business operations become more digitized, the complexity and prevalence of cyber threats grow. Network security teams often deal with frequent alerts that are difficult to fully understand without professional intervention. This ambiguity can lead to incorrect decisions, resource wastage, and significant damage from overlooked signs of intrusion. Outsourcing every incident investigation isn't sustainable due to high costs and fragmented vendor involvement.
Let TeamT5’s ThreatVision IoCs Help You!
TeamT5, with years of experience studying hacker behavior in the Asia-Pacific region, has refined its expertise into precise Indicators of Compromise (IoCs). These IoCs are essential for effective cybersecurity operations, enabling businesses to identify and block intrusions.
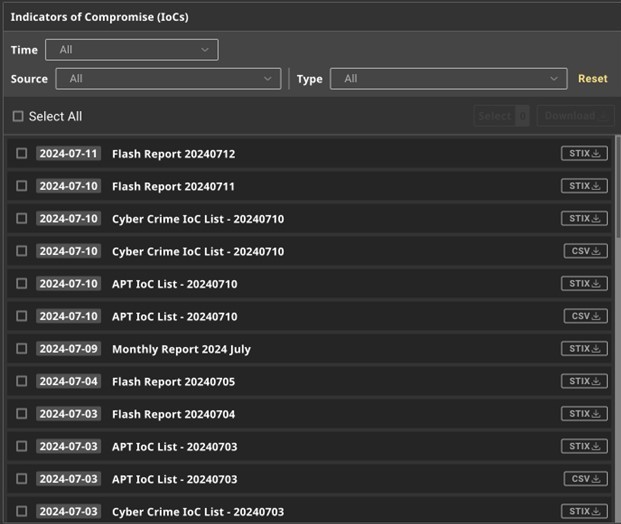
Key Features of ThreatVision IoCs
- High-precision APT IoCs: These are derived from complex investigations and provide insights into specific adversaries and their methods, offering valuable intelligence to strengthen your cybersecurity posture.
- Broad-ranging Cybercrime IoCs: Cover a wide array of cyber threats including infostealer, crypto miner, vulnerability weaknesses and more, ensuring comprehensive protection.
- API Integration: Seamlessly integrates with various network defense devices and firewall applications, facilitating easy and automated deployment.
- Traceable Sources and CSV/STIX Format Support: Ensures IoCs are easily deployable and verifiable.
How ThreatVision IoCs Enhance Cybersecurity
Accurate Alert Judgement
By importing ThreatVision IoCs into your network devices and software tools, you can establish robust monitoring across your environment. When an IoC is detected, it triggers an alarm, allowing cybersecurity personnel to swiftly block, isolate, and clear the threat. This proactive approach significantly reduces the risk and impact of cyber attacks.
Comprehensive Threat Understanding
ThreatVision IoCs link to three rich data types within the platform:
- Adversary Database: Understand the background and motivation of adversaries to deploy defenses for specific digital assets in advance.
- Malicious Program Database: Gain technical details to select and deploy effective defense tools.
- Threat Intelligence Reports: Confirm your situation against recent threats and ensure your defenses are up-to-date.
Proactive Defense Measures
Using ThreatVision IoCs, enterprises can:
- Deploy IoCs Properly: Ensure complete and consistent deployment using our API.
- Respond to Alerts Immediately: Block, quarantine, and remove malware to minimize damage.
- Investigate Thoroughly: Identify the source and purpose of the attack to better understand adversary tactics and tools.
Benefits of ThreatVision IoCs
- Enhanced Alert Accuracy: Make better-informed decisions based on precise IoCs.
- Proactive Threat Management: Understand threats in-depth to take preemptive measures. 3. Ease of Automation: Simplify deployment and management through API integration.
- Rapid Deployment: Utilize generic file formats like CSV and STIX for quick implementation.
Summary
In the battle against cyber threats, understanding both your capabilities and the adversary's tactics is crucial. TeamT5’s ThreatVision platform, with its extensive database of adversaries, malware, and comprehensive threat intelligence reports, empowers enterprises to navigate the threat landscape effectively. By leveraging ThreatVision’s powerful features, businesses can enhance their cybersecurity posture and safeguard against evolving threats.
Making the most of ThreatVision IoCs - contact us !
(cover source: pexels)
Related Post
ThreatVision Resources
2024.04.08
Raw Intel’s Role in Modern Cyber Threat Intelligence
cyber threat intelligence, ThreatVision
ThreatVision Resources
2024.07.31
Staying Ahead of Critical Vulnerabilities with ThreatVision
ThreatVision, cyber threat intelligence