Cybersecurity incidents often occur in subtle places. If you don’t pay special attention, you may not be able to respond and contain them in time.
As the developer of the MITRE ATT&CK framework, non-profit organization MITRE has also faced APT attacks.
Starting in January 2024, hackers exploited two zero-day vulnerabilities in Ivanti Connect Secure—CVE-2023-46805 and CVE-2024-21887—to perform reconnaissance on the MITRE organization's network and bypass the multifactor authentication (MFA) protecting the system with session hijacking. The attackers moved laterally and dug deep into MITRE network’s VMware infrastructure using a compromised administrator account and deployed complex backdoors and webshells to gain persistent access to credentials.
The past, present and future of cybersecurity incidents
MITRE's response process of this cybersecurity incident is worth discussing and learning from. First, if organizations would like to prevent the occurrence of incidents, detection is very important. Real-time anomaly detection is necessary. Second, network isolation is used to prevent attackers from getting to the core, allowing the damage to be within control. What is more important is threat intelligence feeds, which make it possible to evaluate and handle the vulnerabilities. In the process of adversary engagement, organizations should consider how to take measures to minimize the damage.
When a cybersecurity incident occurs, through a series of incident response processes, it is nothing more than three aspects of the incidents: "What happened in the past?", "How to deal with it now?" and "How to strengthen the response in the future?" to figure out:
- What is the attacker's initial access point?
- Did the attacker spread to other resources? If so, how did lateral movement happen?
- Has the attacker gained a foothold in the environment? If so, what is their method of persistence?
- What impact do breaches have on businesses? For example, credentials leakage, etc.
- How can this be prevented next time?
Understand cyber kill chain and formulate security maintenance strategies
According to TeamT5’s long-term experience in handling incidents, initial attacks are often caused by credential leakage and vulnerabilities. For cybersecurity personnel, their daily work not only requires close attention to security threats posed by adversaries, but also the state of digital assets in the environment, especially on the latest vulnerability information related to their assets. In addition, by understanding the attack process and implementing the measures in daily cybersecurity maintenance, the organization's defense capabilities can be improved.
From the cyber kill chain, you can understand all aspects before, during, and after the occurrence of a security incident. Attackers understand the environment through reconnaissance, researching exposed vulnerabilities, entering the environment to install intranet penetration tools, and finally taking actions to attain the attacker's ultimate goal. For example, APT involves stealing credentials through lurking in the environment, and ransomware is used to encrypt important data, etc.
Corresponding to the process of the attack incident, we can summarize the standards, countermeasures and defensive measures that can be followed security control from the Cyber Security Framework (CSF) 2.0 released by the National Institute of Standards and Technology (NIST):
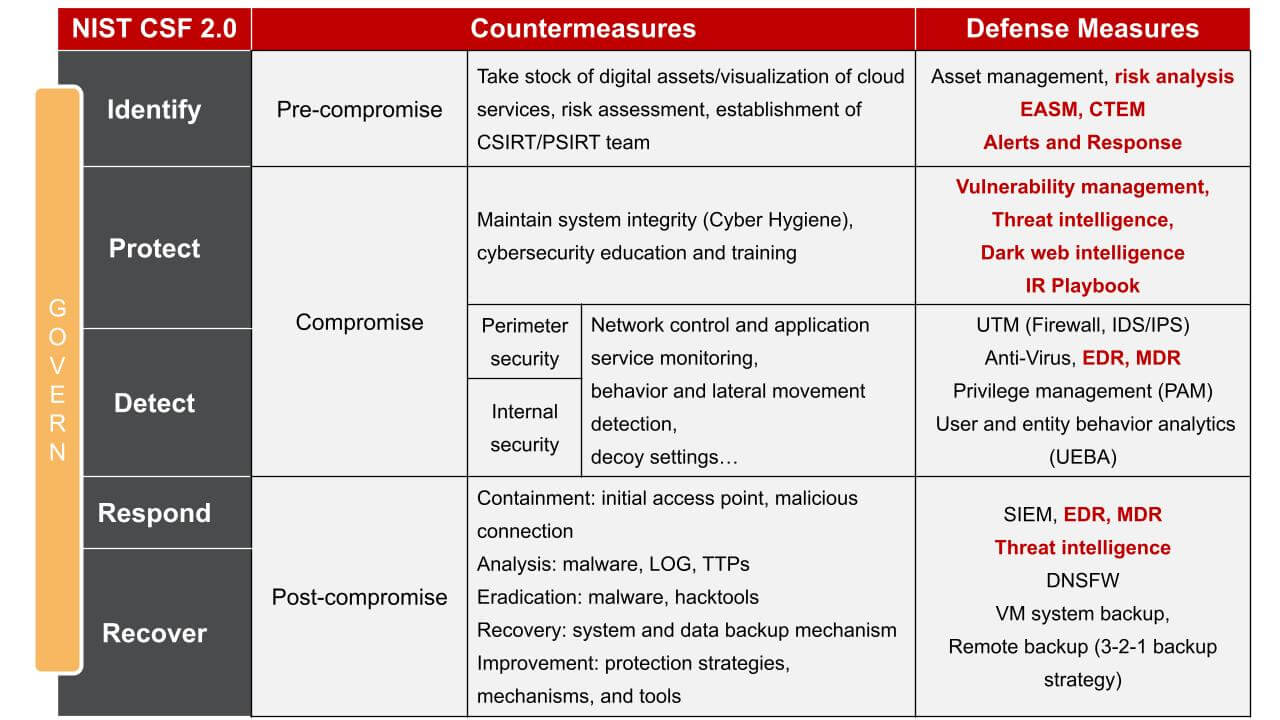
During the pre-compromise process, organizations can get prepared by adopting red team/blue team simulations to understand which assets in the environment may be at risk. When an incident occurs, it is necessary to work with external incident response experts to understand the source of the attack, follow-up prevention, incident analysis, etc. Collaboration between the two parties is also very important. Only after these countermeasures and defense measures are integrated, effective responses can be taken when an incident occurs.
How do we strengthen security resilience?
According to the top cybersecurity trends for 2024 released by Gartner, the importance of security resilience is particularly emphasized. Cyber resilience, as defined by NIST, refers to the organization’s ability to anticipate, withstand, recover from and adapt to attacks, such as service interruption, data leakage, encryption ransomware, etc. and defense against future attacks.
Therefore, to strengthen security resilience, we must consider how to optimize incident response planning. For example, since incident investigation takes time, how can we respond in a short time? Meanwhile, how can we quickly restore system operations after being attacked? Therefore, it is extremely important to optimize cooperation with third parties so that you will not be in a fluster when an incident occurs.
ThroughTeamT5’s experience of incident response, we suggest organizations to examine the following aspects and prepare in advance to strengthen the security resilience and reduce risks of damage:
- Asset security status: Which assets in the environment are impacted by cybersecurity incidents? What is the situation?
- Attack surface analysis: Analysis and identifications of initial points in the environment that may be exploited by attackers.
- Threat intelligence: What impact will these threat intelligence related to the organization, such as APTs, darknets, extortion groups, etc. impact on our assets?
- Determine risk priorities: Based on the information, organizations can evaluate the risk status of the site and have suggestions for subsequent contingency measures.
- Risk management: Backup and restore important assets, collect evidence required for investigation, resume operations when the incident is controllable, and improve the procedures required for incident investigation.
- Control the security situation: Based on the contingency measures taken, continuously monitor and control the situation of the environment, observe whether there are still malicious attacks, and eliminate hidden malicious threats.