We were glad to announce that TeamT5 was again accepted at Black Hat USA. And this time, our vulnerability research team, D39, presented their latest exploit research on Samsung S10 secure bootloader at the Black Hat Briefings. We were very honored to share our research findings with researchers and security experts all over the world in this annual flagship conference.
 TeamT5's vulnerability researcher presented on Black Hat USA 2020.
TeamT5's vulnerability researcher presented on Black Hat USA 2020.About D39's Vulnerability Research Finding
D39 has been focusing on vulnerability research and has identified several critical security flaws. We have found several vulnerabilities in Samsung Secure boot, which can break through Samsung Knox protections. In Black Hat USA 2020, we elaborated how did we discover and exploit the vulnerabilities in detail, demonstrated the exploit on a Samsung Galaxy S10 smartphone, and had a discussion on the possible impact of these vulnerabilities.
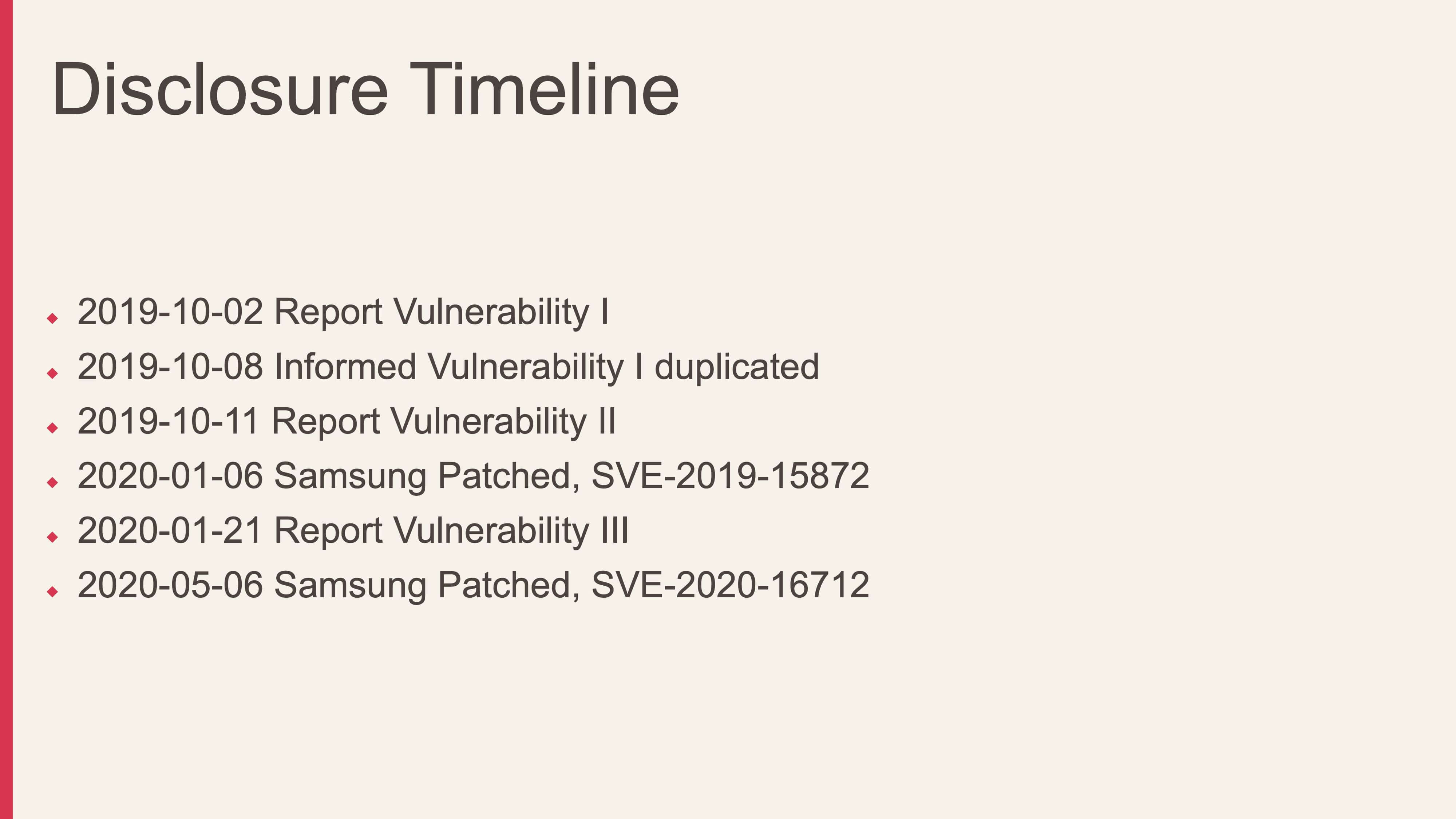 Timeline of the vulnerability disclosure, patch release and assignment of SVE IDs.
Timeline of the vulnerability disclosure, patch release and assignment of SVE IDs.About Black Hat
Black Hat is the world’s leading information security event, and remains the best and biggest event of its kind. It provides attendees with cutting-edge security research, development and trends, and has the ability to define tomorrow’s information security landscape. Black Hat USA 2020 went fully virtual this year, held over the same dates from 1 to 6 August, in light of the coronavirus pandemic.
*Image courtesy of Black Hat from https://www.blackhat.com/us-20/
Related Post
News
2022.03.22
【Cybernews】Sung-ting Tsai, TeamT5: “companies shouldn’t claim themselves as 100% secured or unhackable”
ThreatSonar, cyber security, ThreatVision, cyber threat intelligence, threat hunting
Technical Analysis
2020.06.10
BlackHat's Talk: Breaking Samsung's Root of Trust - Exploiting Samsung Secure Boot
vulnerability research , D39, Black Hat, cyber threat intelligence, threat hunting
Technical Analysis
2021.02.17
A Deep Dive into PowerShell's Constrained Language Mode
PowerShell, Constrained Language Mode, cyber threat intelligence, threat hunting
Events
2022.02.09
TeamT5 Presents Latest Analysis on Information Operation on CTI Summit 2022
seminar, cyber threat intelligence, threat hunting