The incident response team of TeamT5 discovered a worm virus named Win32.Parite during an incident investigation. In the incident, the executable file in the victim host was infected by Win32.Parite. The infected host could spread to other execution files and wait for the attacker to connect; if the connection succeeds, the attacker can perform various communication and data collection behaviors on the infected host, which will have a profound impact.In this blog, we provide a detailed analysis of the worm virus and develop a scanning program with instructions on how to remove it, to help companies improve their cybersecurity defenses. We also urge companies that are still using 32-bit operating systems (e.g. WinXP/2003/7) to use scanning programs to scan their internal network systems.
Basic Information of Malware Win32.Parite
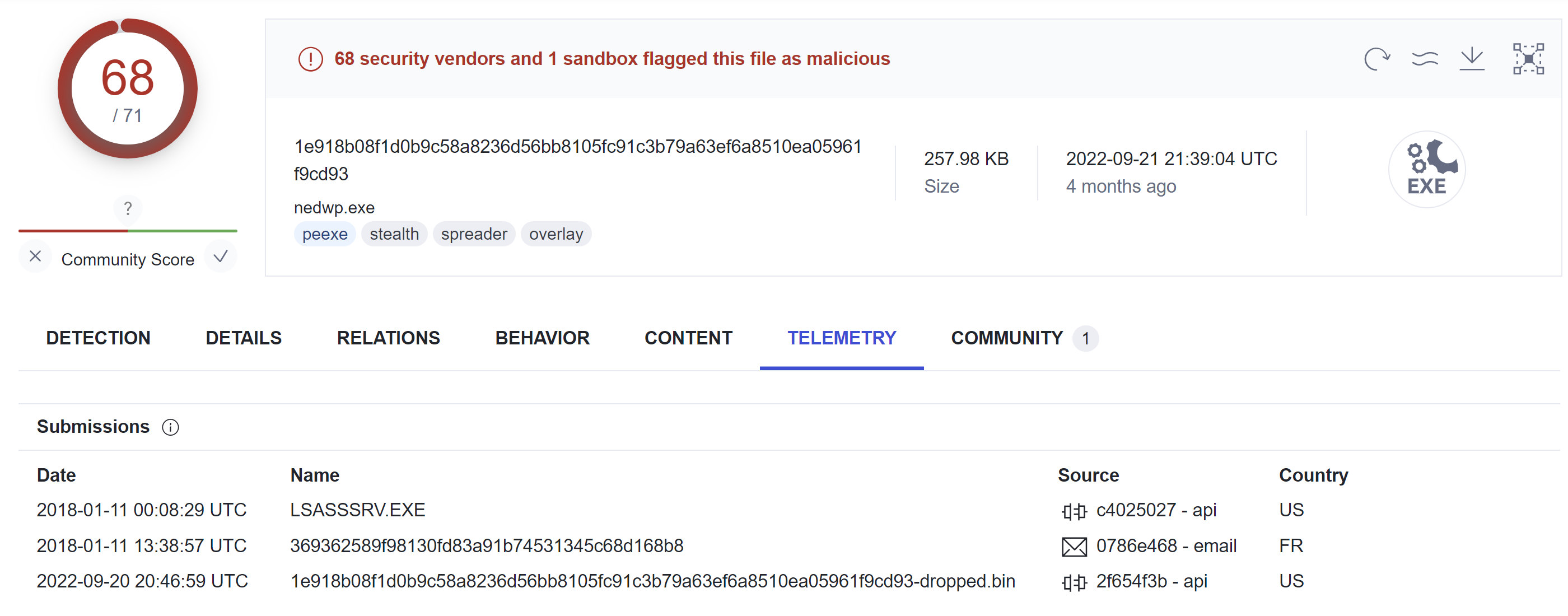 Image source: VirusTotal
Image source: VirusTotalMalware Analysis
Win32.Parite: Shellcode
TeamT5 obtained the malicious file. We use Stud_PE to observe. There is a section named .heb, and the program entry point is pointed to this section. The characteristic of the Win32.Parite virus is that it inserts itself in the last section whose name is a random combination of letters.
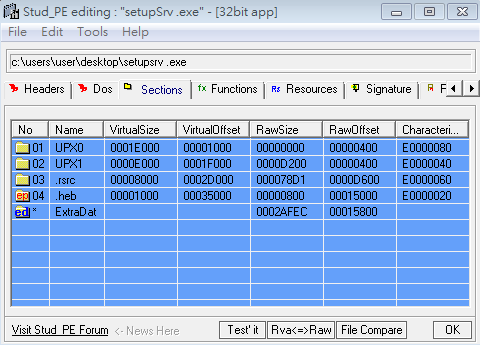
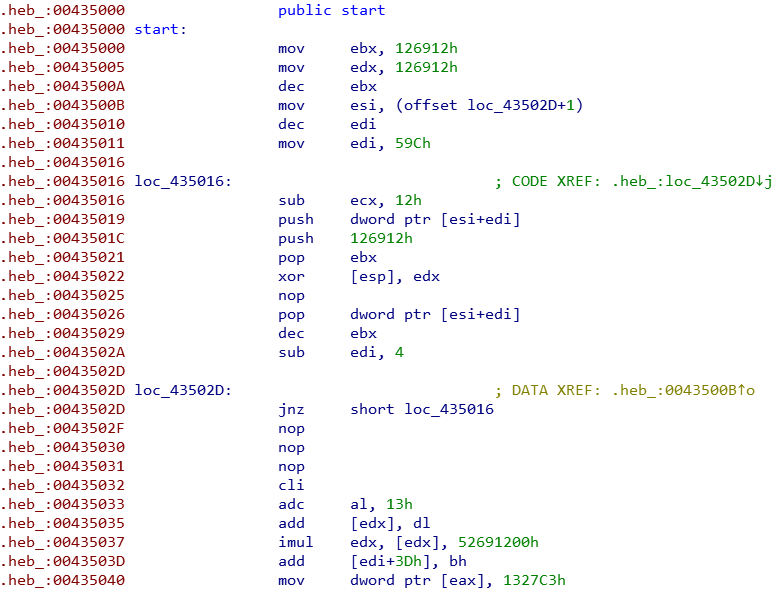
The entry point is a small decoder. The edx in the temporary register is the operation value of xor decoding, while esi is the address of the encoded data, and edi is the size of the encoded data.
When decoding, the operation is 4 bytes at a time, and the range of all addresses is 0x43502E+4~0x43502E+0x59C, because the method of [push/pop] dword ptr [esi+edi] is used, so the target address of xor here will be is [esp].
After understanding the above, you can use 010 Editor to do the XOR operation. After unpacking, there is a piece of shellcode.
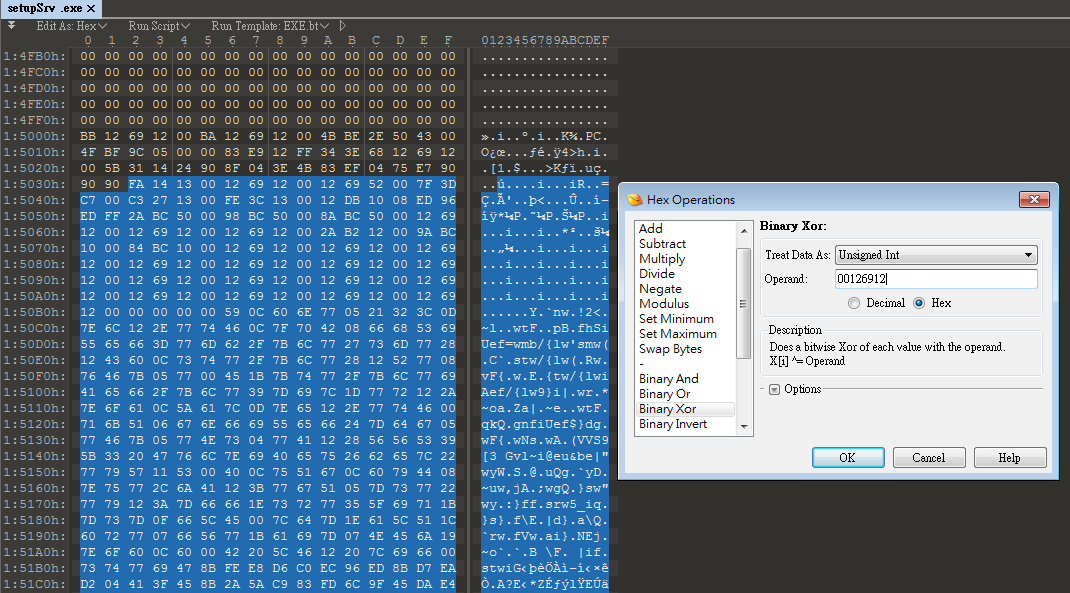
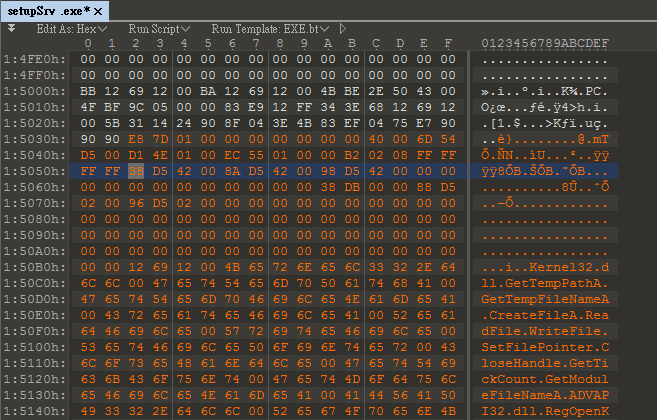
What is interesting is that this worm virus also has a deformation function . Observing the three infected files, we found that the shellcode commands are different, but the purpose is the same. They all aim to obtain the decoded value, encoded address, and size of encoded data.
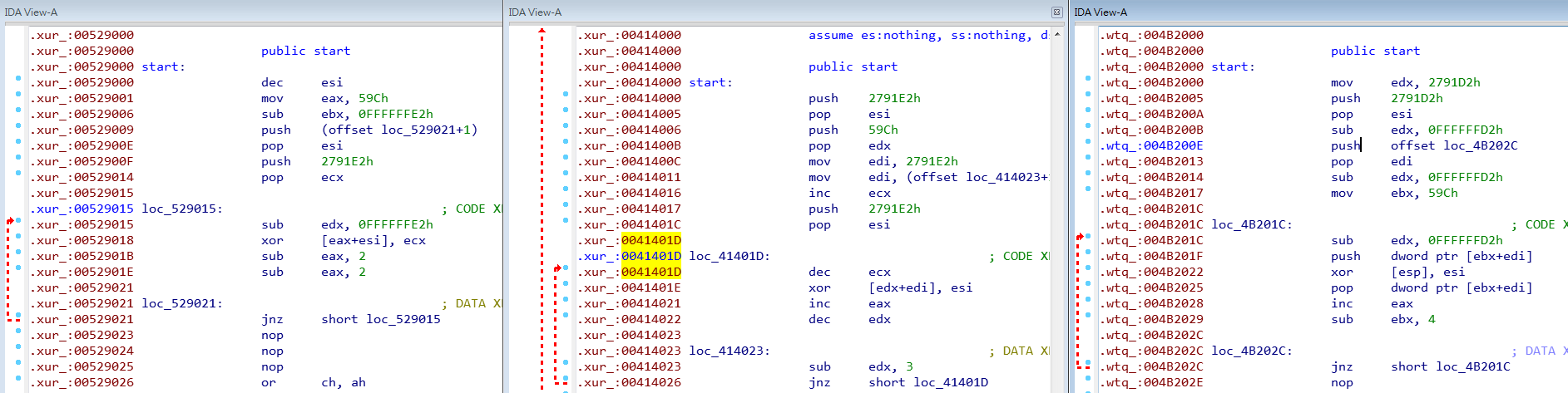
After decoding, continue to analyze the shellcode. The first group of instructions after unlocking is a call, followed by a Parite custom structure. The interesting thing is that the original entry point is protected by an encoded program.
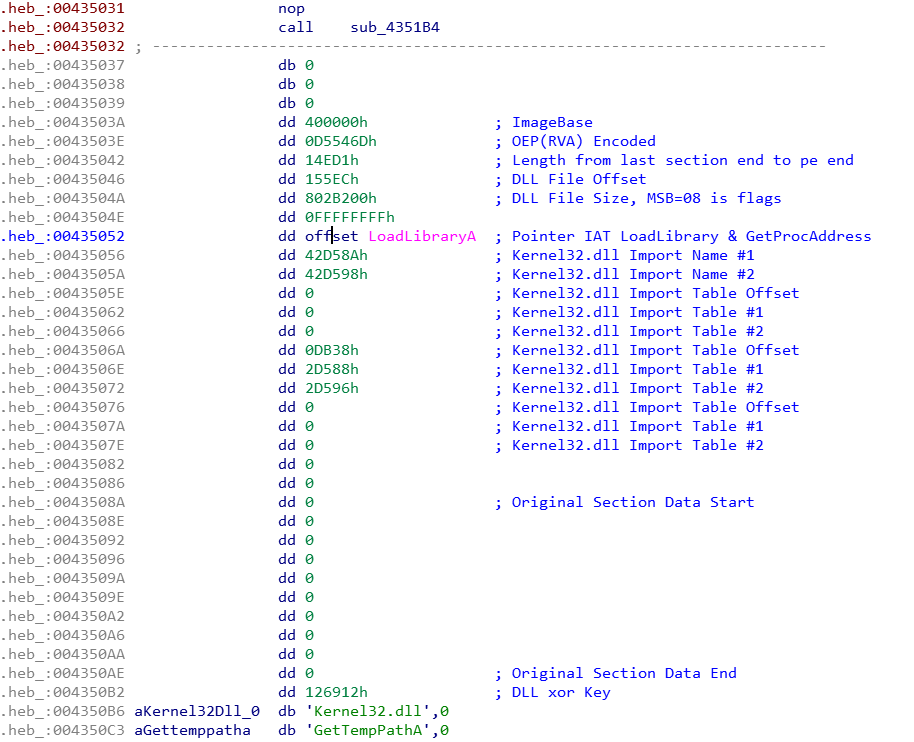
The main program of Shellcode has only a few functions:
- GetDeclareAPI: Obtain the API address when needed and store it in the Stack.
- RegQuery_PINF: Query whether the PINF code exists, and the content is stored in the path of the virus body.
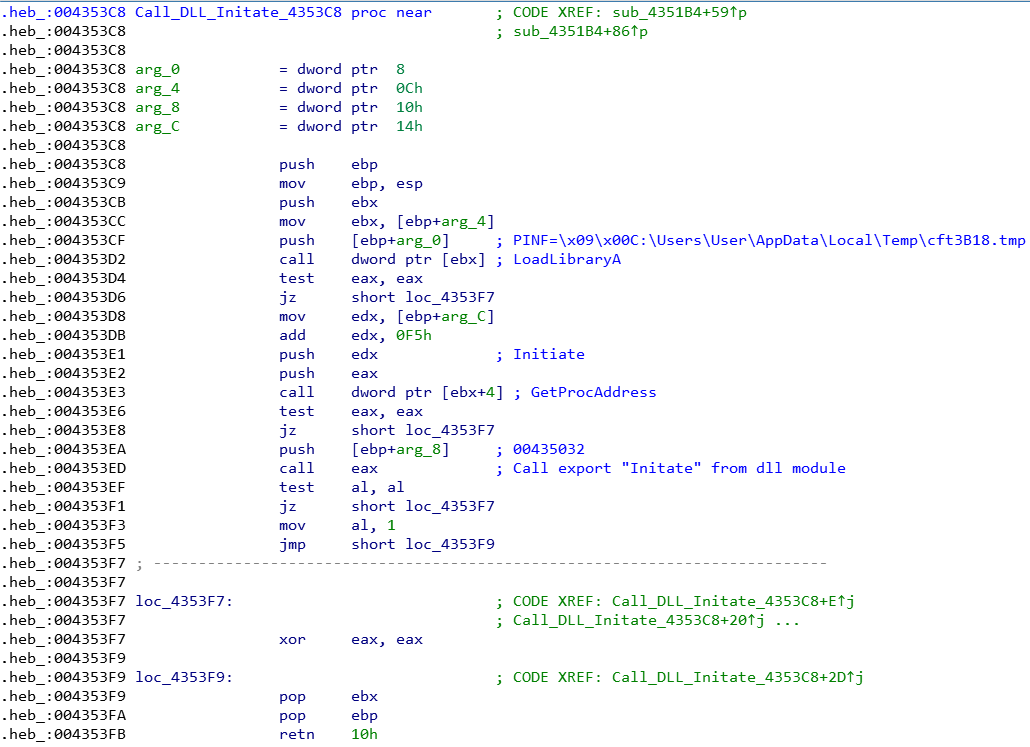
- Call_DLL_Initiate: Call “Initiate” in the main program DLL, which contains the original entry point for unlocking the EXE.
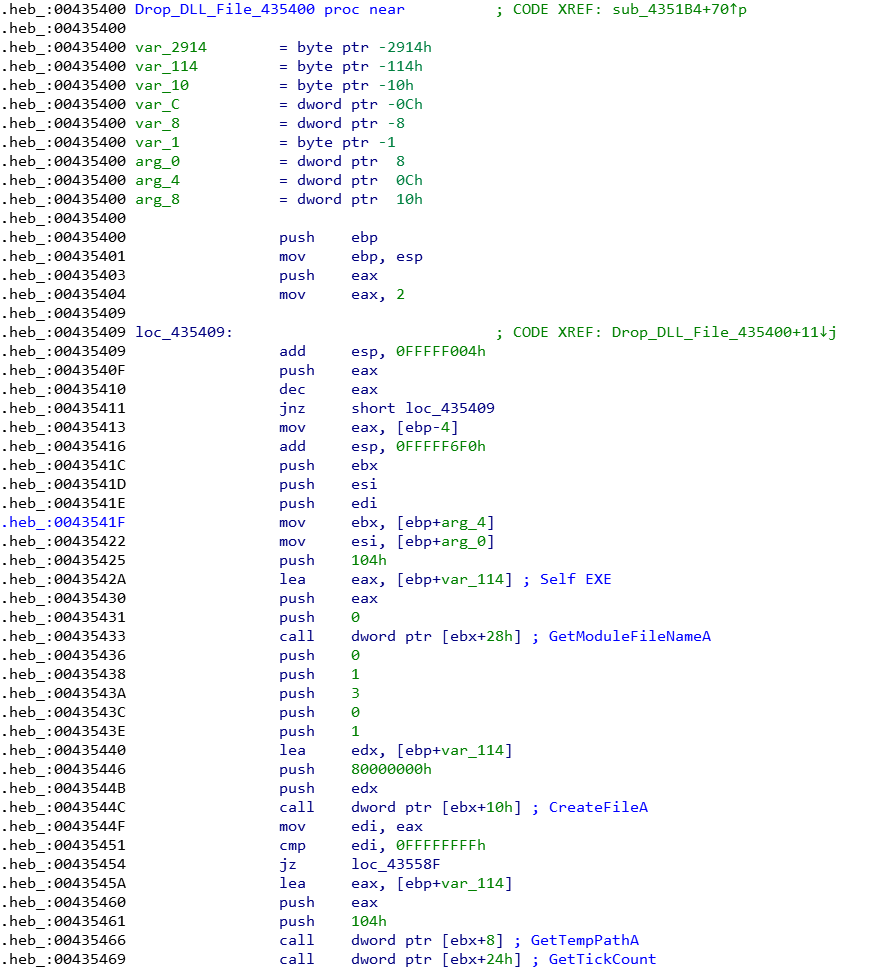
- Drop_DLL_File: If the PINF doesn't exist, it will drop the virus body (DLL) and create the key value of a PINF login file.
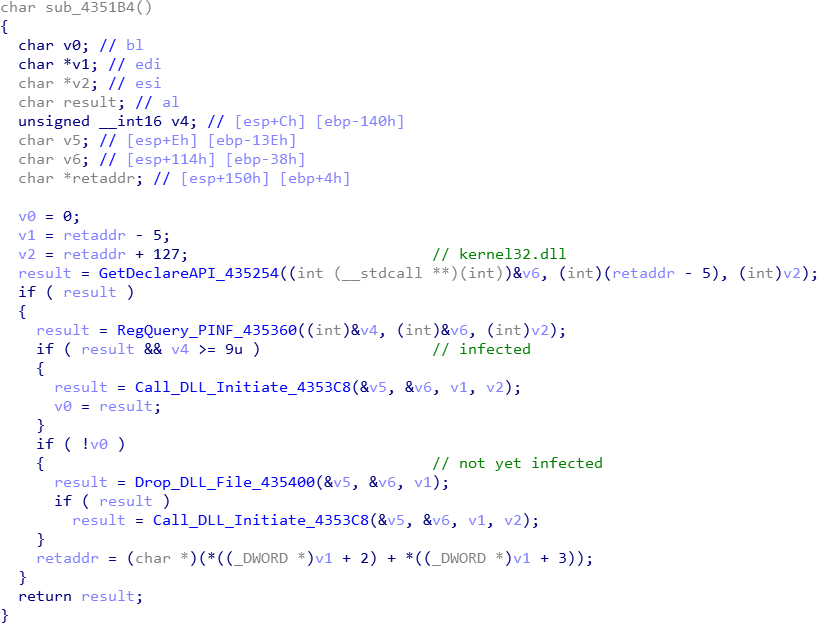
Shellcode obtains some necessary Windows APIs through GetDeclareAPI(sub_435254), and then queries the PINF key value located in HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer through RegQuery_PINF(sub_435360).
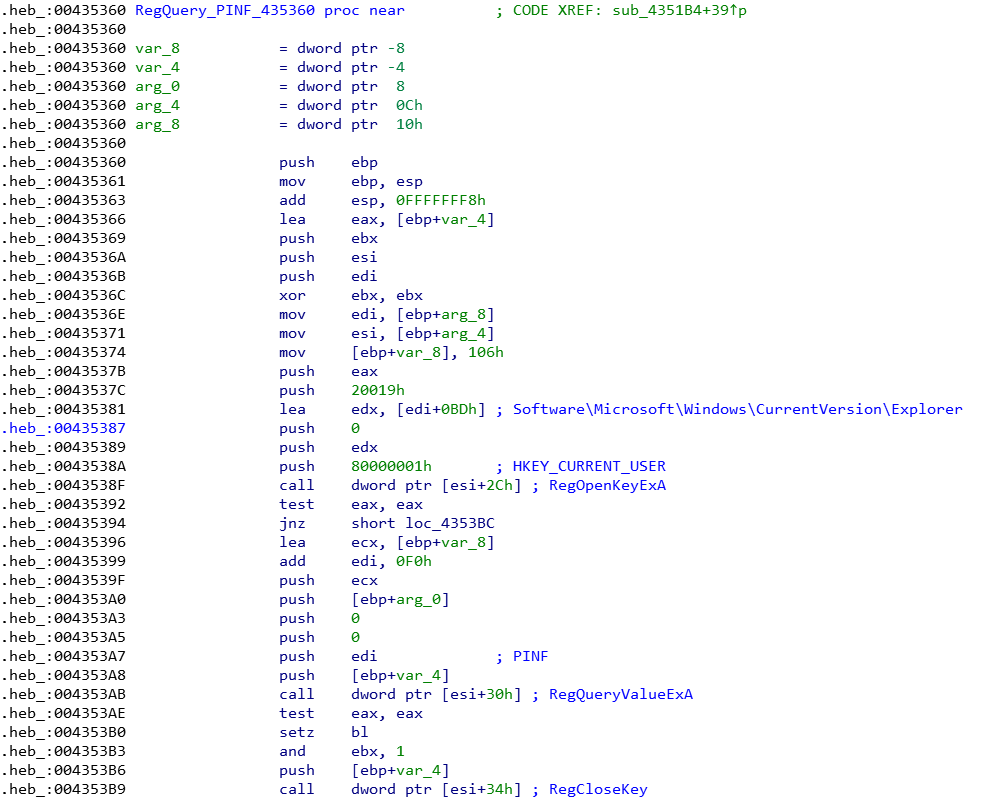
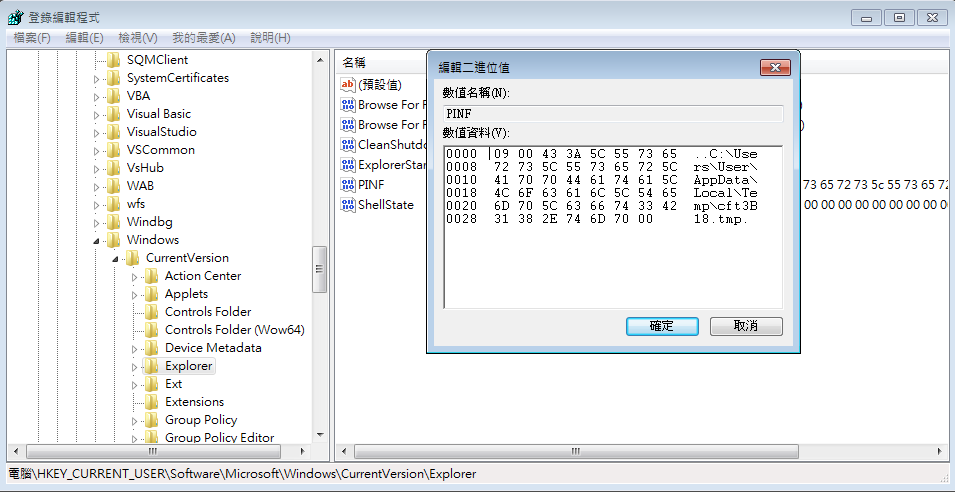
In the infected host, it can be seen that the value of PINF is \x09\x00, where 9 is the virus version, separated by \x00, and then followed by the DLL path.
If the key exists and the value of the first 2 bytes is greater than or equal to 9, the shellcode will load the DLL module of the virus body through Call_DLL_Initate (sub_4353C8), and use GetProcAddress to obtain the address of the Initiate function. Then, it passes in the configuration address of 000435032 and jumps into execution.
If the key value does not exist, the shellcode will decode the virus body (DLL) at the back through Drop_DLL_File (sub_435400) and throw it out. Then, it executes Call_DLL_Initate (sub_4353C8) to load the DLL module of the virus body.
The offset address and file size (Size) of the DLL, as well as the encoded XOR key, can be seen in the configuration.
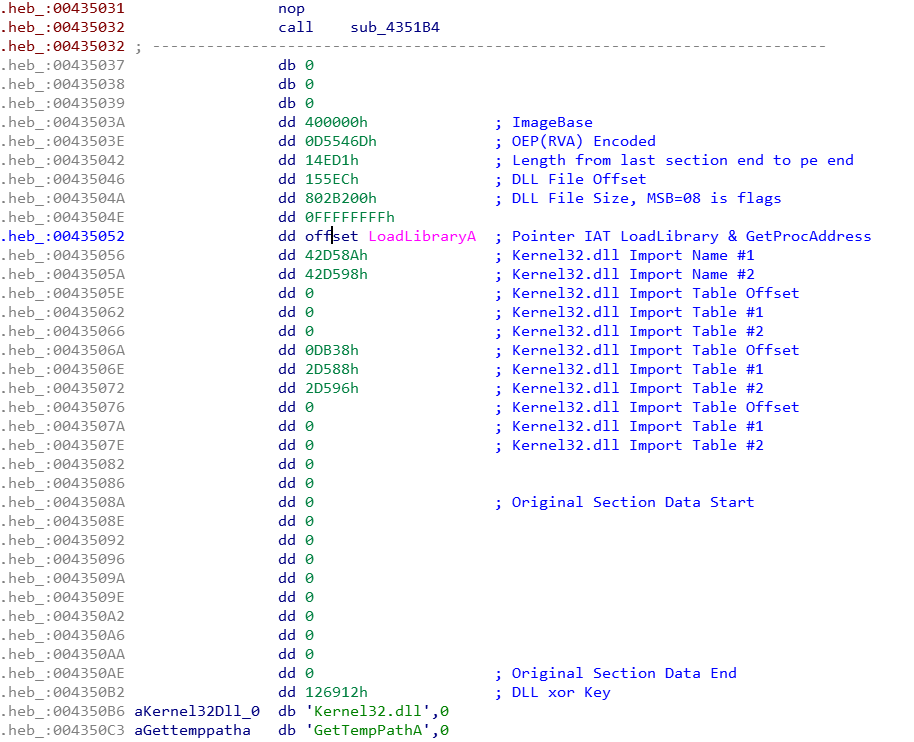
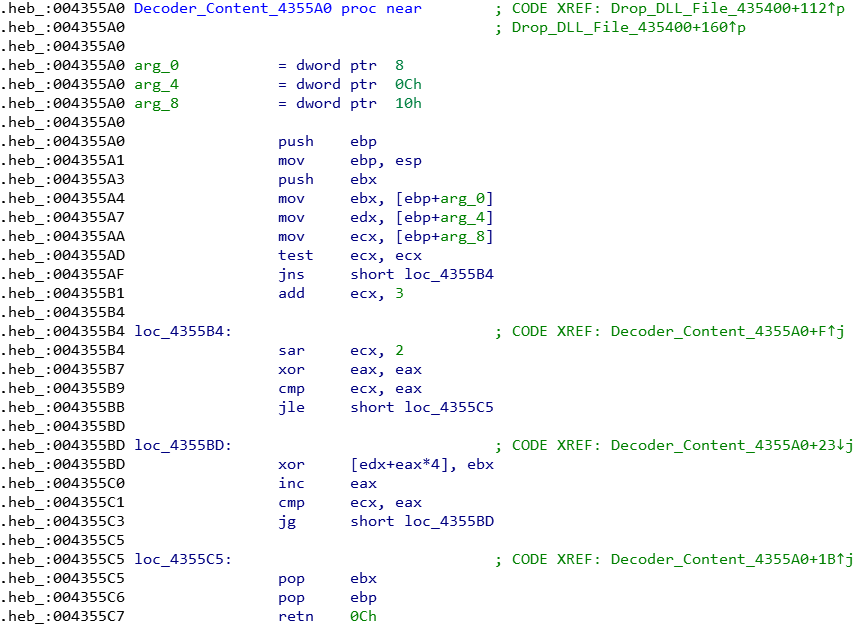
In the Drop_DLL_File(sub_435400) function, the Decoder_Content(sub_4355A0) function will be called, and the content is encoded and decoded using xor dword.
Win32.Parite: Virus Body
The decoded DLL is packed with UPX, and the main virus module itself is written in Delphi. Line 23 of the exported Initiate function has a function to decode the original entry point (OEP).
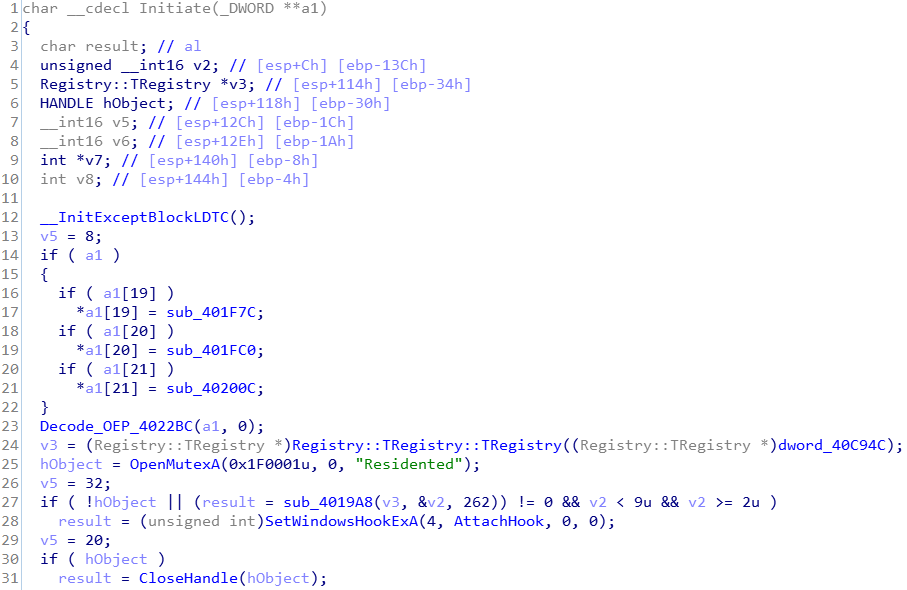
The program code in the Decode_OEP(sub_4022BC) function mainly obtains the two array addresses of 43504D and 43506E in the configuration block. It performs calculations through the sub_40232C function to generate a value of 16 bytes, which is divided into 4 groups of DWORD values, and The encoded OEP is XORed four times. The final result is the original OEP. With OEP, the infected PE execution file can be successfully repaired.
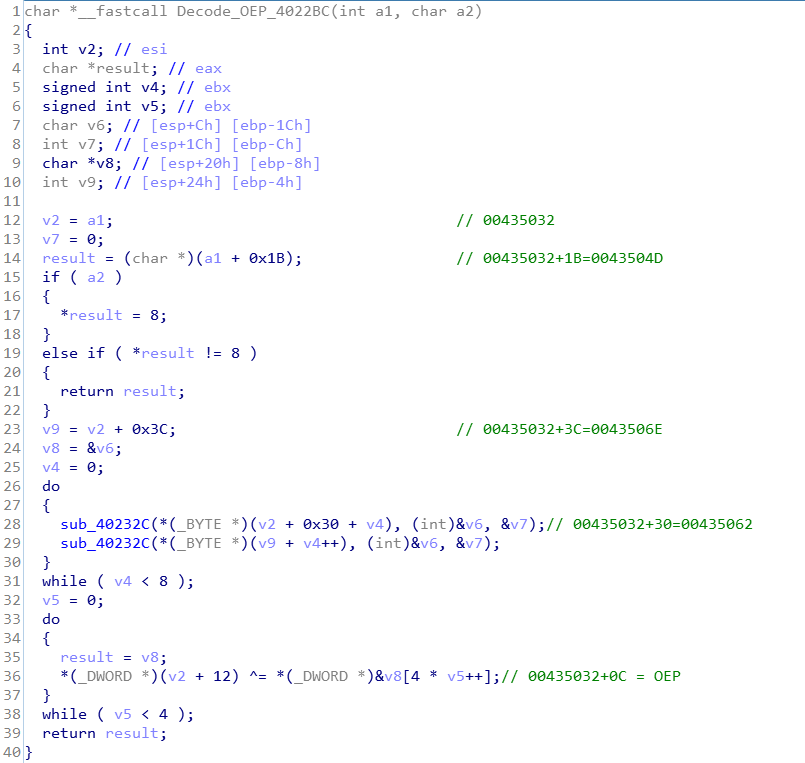
Then, use SetWindowsHookExA to set a global hook to inject the DLL into all handlers.
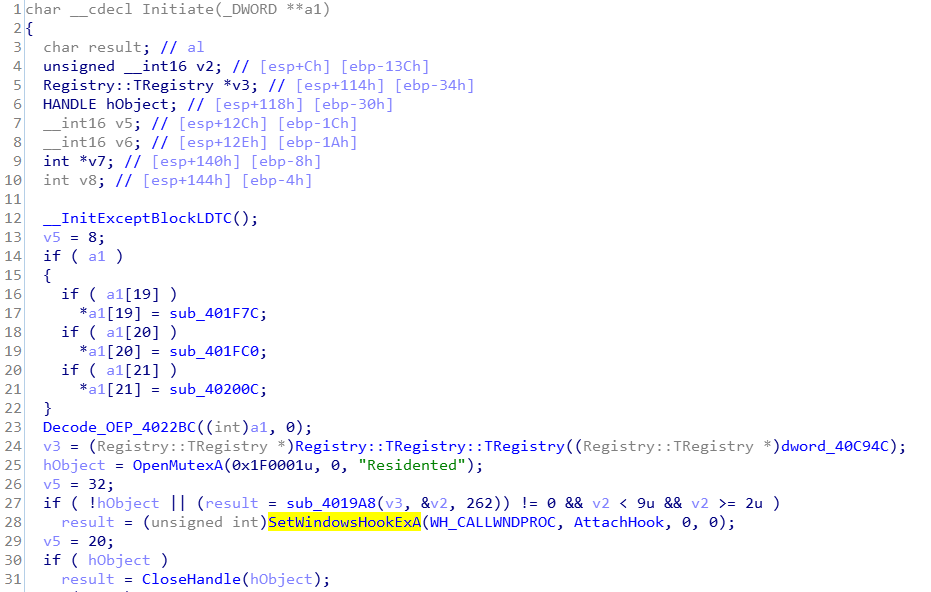
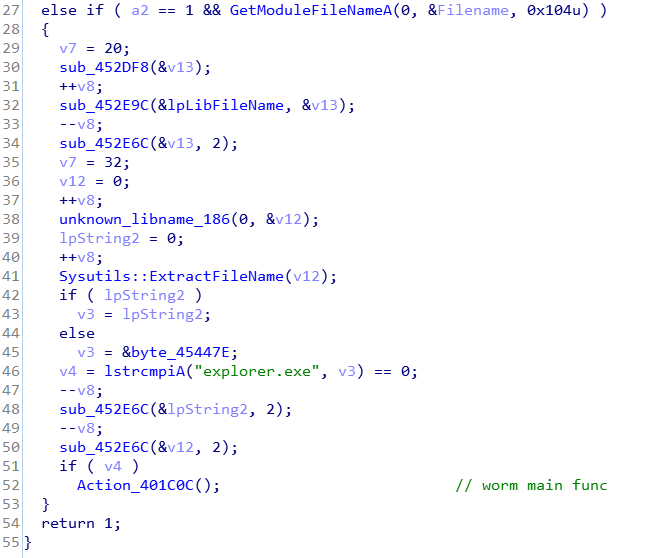
When the injected handler is explorer.exe, Win32.Parite will start to execute the behavior of the worm.
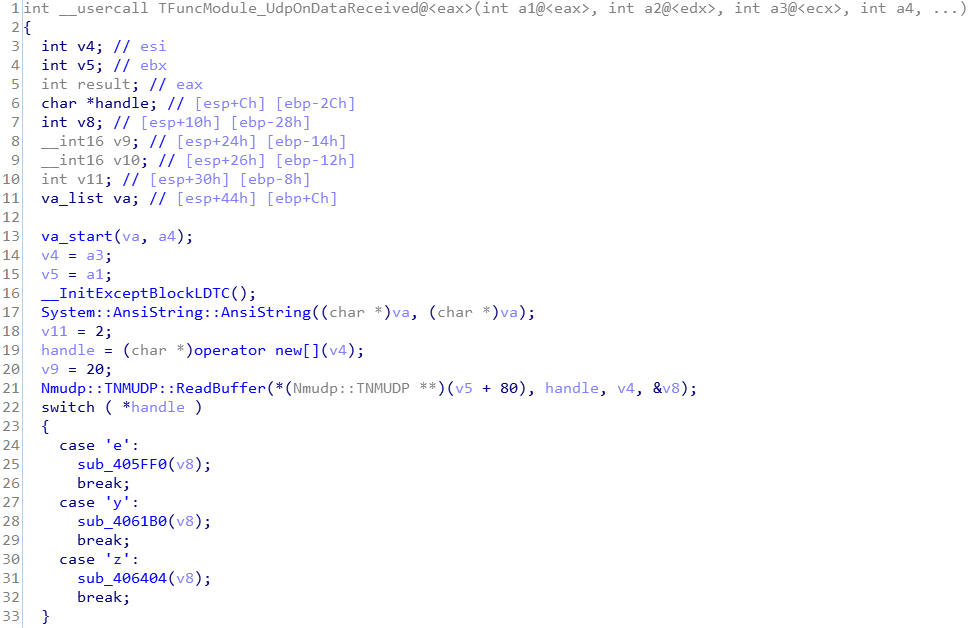
Win32.Parite: Backdoor Functionality
In the program code in the virus main DLL, you can see a piece of interesting code. Win32.Parite supports backdoor function. The backdoor uses UDP protocol to send commands. The result of the report will be sent back to the UDP 30168 communication port of the controlling terminal. When uploading data, it is necessary to monitor the TCP 30169 communication port on the controlling terminal and wait for the controlled terminal to actively connect, and then the data content can be uploaded.
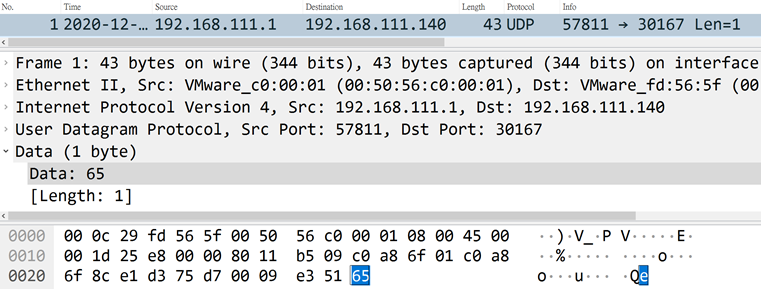
Report Information to the Host
The controlling terminal sends out the characters of "e" to the UDP 30167 communication port of the controlled end.
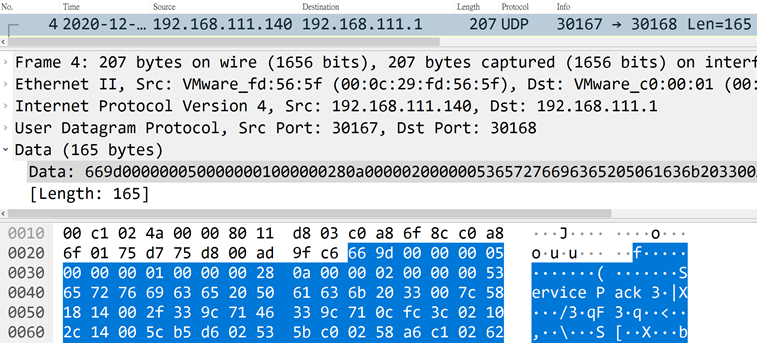
The controlled terminal will report the host information to the UDP 30168 communication port of the control terminal.
Execute Commands
The controlling terminal will report the host information to the UDP 30168 communication port of the control terminal.
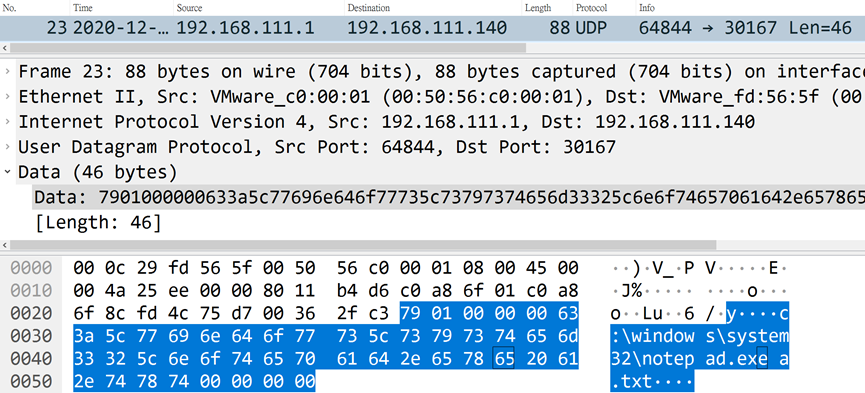
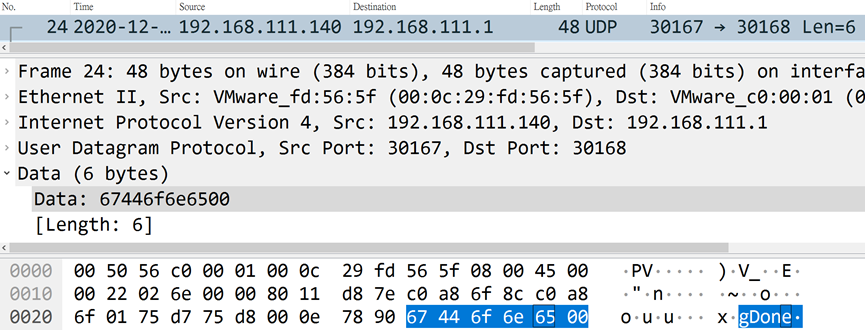
When the command is successfully executed, the controlled end will return the character "g", followed by the string of Done.
Upload Files
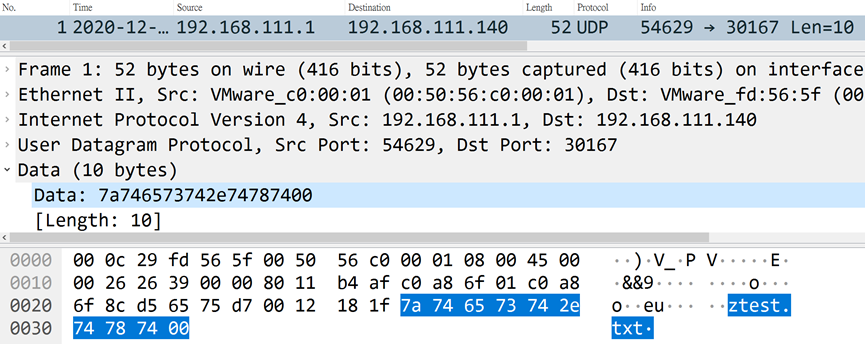
The controlled terminal sends out the character z, followed by the file name, and finally ends with \x00, and the file will be stored in the %WINDIR% folder.
The control terminal listens to the TCP 30169 communication port, and waits for the content of the data that can be sent after the successful connection of the controlled terminal. After the connection is terminated, the data will be written into the file.
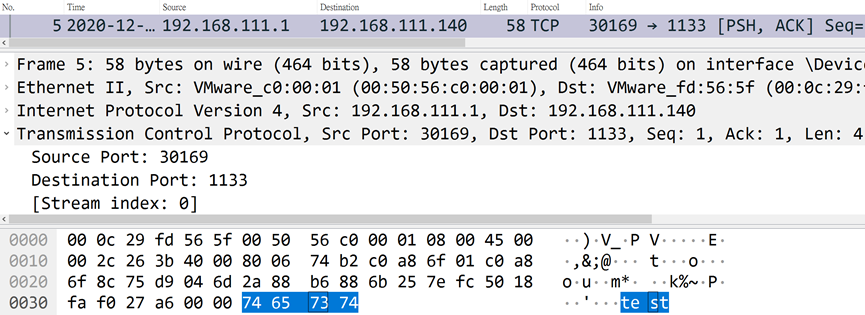
The control terminal listens to the TCP 30169 communication port, and waits for the content of the data that can be sent after the successful connection of the controlled terminal. After the connection is terminated, the data will be written into the file.
- Add 1 Section
- The original entry point (OEP) is pointed to the Section where the last virus is located
- The image file (Image) loaded into the memory becomes larger
- Modified the properties of .rdata
- Added new virus section
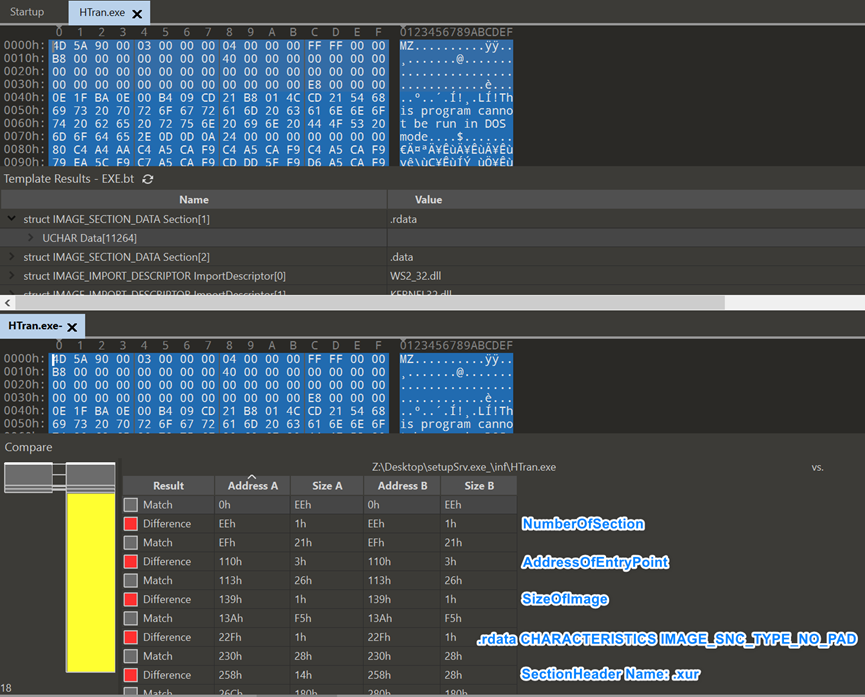
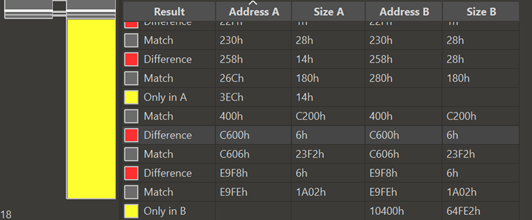
In the file comparison, there are two places that were last modified, namely C600 and E9F8.
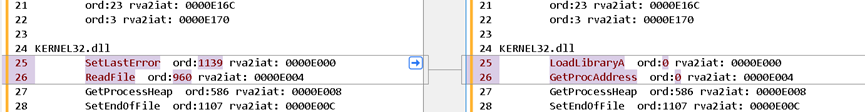
You can see that these two places are actually the first two functions of kernel32.dll in Import Tables. Because the infected file did not write its own Shellcode to fetch the API, it relies on inserting LoadLibraryA and GetProcAddress in the import table to ensure that it is included in the Shellcode. These two functions can be used normally to obtain the API to be used, and it will be restored when the Shellcode is executed.
Detox Program
After knowing what has changed in the infected file, we can write a detox program to repair the infected file. The detox program basically does the following:
Checks if the entry point falls on the last section with a section name of .
Instructions
Usage: fix.exe <file or directory>
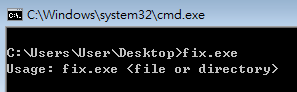
Test
> fix.exe setupSrv.exe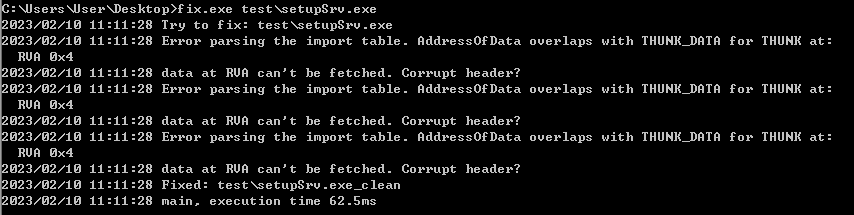
The repaired archives will be in the same path, with the archive name
_clean ending with . Looking at the repaired file, you can see that the last infected section and entry point (ep) have been fixed.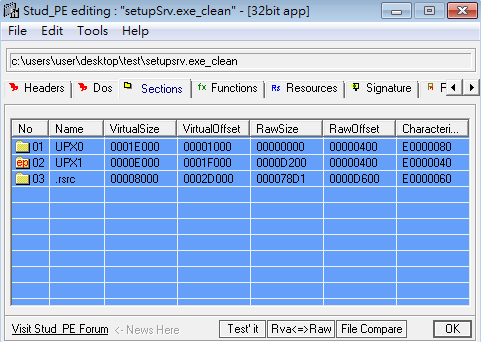
Check if the Host is Compromised
We understand that when the control end sends the character e to the UDP 30167 communication port of the controlled end, the controlled end will report the host information to the UDP 30168 communication port of the control end.
Therefore, we can use this point to develop a scanning program to send e characters to the intranet host and monitor the UDP 30168 communication port on the sending end to wait for the return information.
Scanner
Instructions
Usage: scan.exe iplist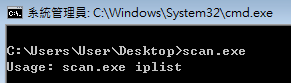
Test
> scan.exe 127.0.0.1
> scan.exe 192.168.0.0/16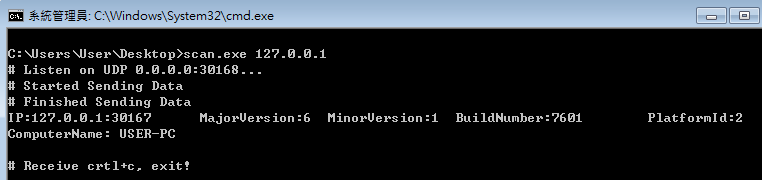
Download the Scanner Tool
IoC
| file name | md5 | compiler-stamp (UTC) | type |
|---|---|---|---|
| setupSrv.exe | c5e7e7007b7ea6a3361fea7d4b029859 | 2009-12-04 13:35:59 UTC | EXE |
| cft3B18.tmp | fe763c2d71419352141c77c310e600d2 | 2001-10-11 12:01:58 UTC | DLL |
Know more about us: https://teamt5.org/en/about-us/