TeamT5 and Macnica Networks have published our joint research on APT attacks targeting Japan over the past year. In this collaborative research, we provide valuable insight into four advanced persistent threat (APT) groups and actors. The full report will first be available in Japanese and can be accessed at Macnica Networks' website.
The APT groups' highlighted in this joint project were believed to have been launching cyber espionage campaigns elsewhere in the world. To enhance APT defense strategies, we take a closer look at the four APT groups, including DarkHotel, Huapi (BlackTech), Nian (Tick), and one unclassified backdoor LODEINFO. These APT groups have been threatening crucial sectors in Japan, such as government, military and defense, manufacturing, telecommunication, education, media, and etc.
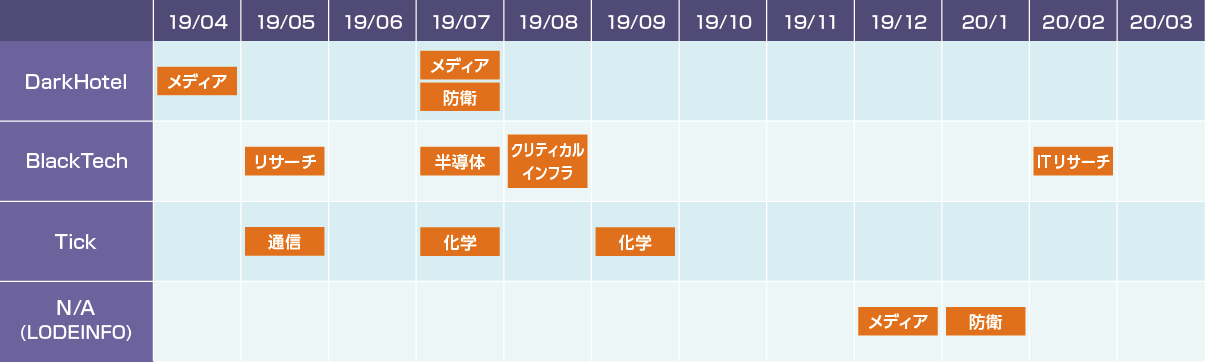 The attack timeline of the APT groups' campaigns in Japan in 2019.
The attack timeline of the APT groups' campaigns in Japan in 2019.About Macnica Networks
Macnica Networks is one of the largest system integrators (SI) in Japan. As a leading network distributor, it provides a wide range of advanced network products and information technology to government offices, educational institutions, and general companies.
To access the full report, please visit: https://www.macnica.net/mpressioncss/feature_06.html/
Related Post
新聞
2020.05.05
TeamT5 聯手 Macnica Networks 與 Terilogy Technology,幫助「關鍵基礎設施」對抗 APT 攻擊
ThreatSonar, APT, Japan, critical infrastructure, Macnica Networks, Terilogy Technology, cyber threat intelligence, threat hunting