We were glad to announce that TeamT5 was again accepted at Black Hat USA. And this time, our vulnerability research team, D39, presented their latest exploit research on Samsung S10 secure bootloader at the Black Hat Briefings. We were very honored to share our research findings with researchers and security experts all over the world in this annual flagship conference.
 TeamT5's vulnerability researcher presented on Black Hat USA 2020.
TeamT5's vulnerability researcher presented on Black Hat USA 2020.About D39's Vulnerability Research Finding
D39 has been focusing on vulnerability research and has identified several critical security flaws. We have found several vulnerabilities in Samsung Secure boot, which can break through Samsung Knox protections. In Black Hat USA 2020, we elaborated how did we discover and exploit the vulnerabilities in detail, demonstrated the exploit on a Samsung Galaxy S10 smartphone, and had a discussion on the possible impact of these vulnerabilities.
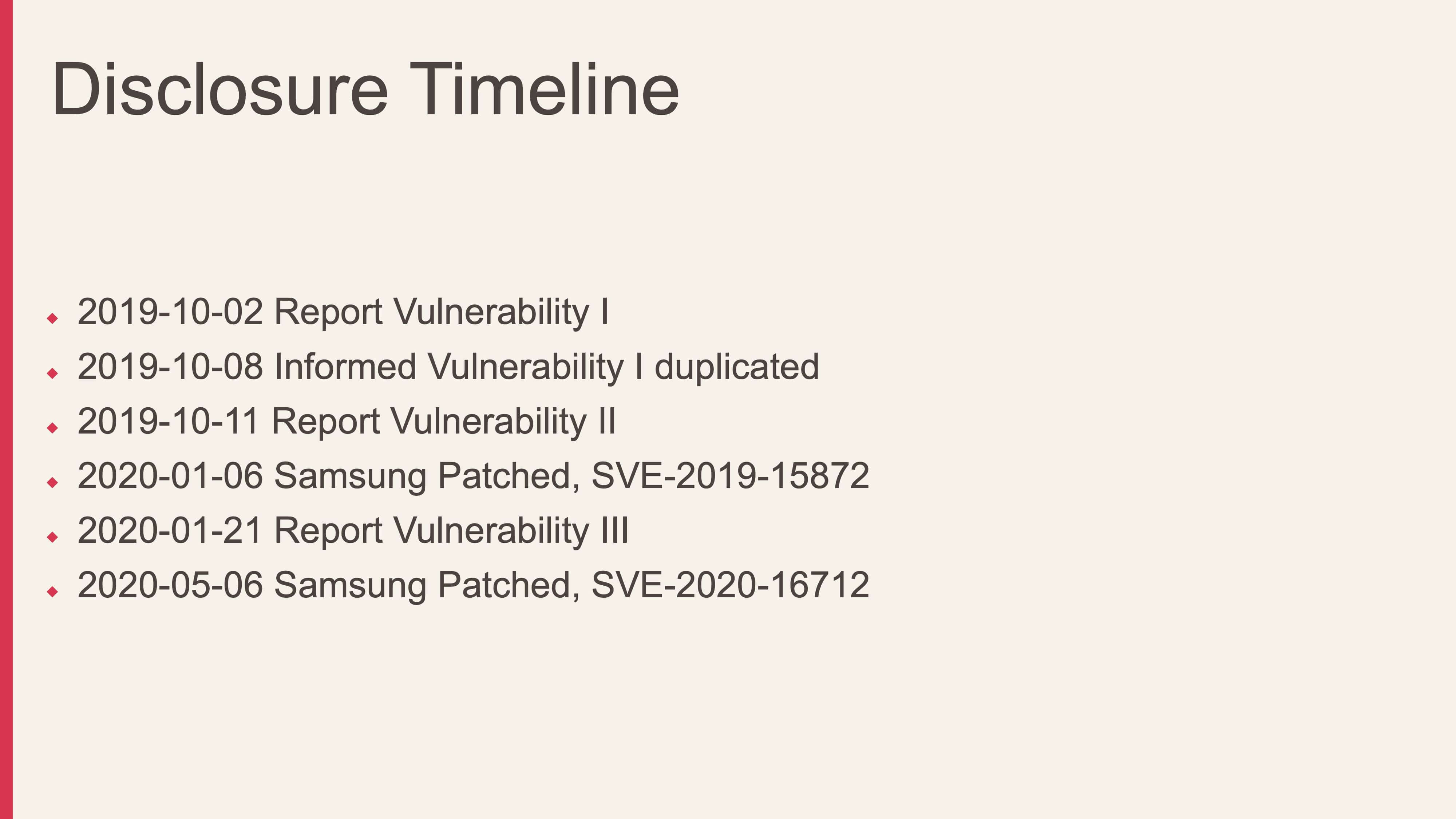 Timeline of the vulnerability disclosure, patch release and assignment of SVE IDs.
Timeline of the vulnerability disclosure, patch release and assignment of SVE IDs.About Black Hat
Black Hat is the world’s leading information security event, and remains the best and biggest event of its kind. It provides attendees with cutting-edge security research, development and trends, and has the ability to define tomorrow’s information security landscape. Black Hat USA 2020 went fully virtual this year, held over the same dates from 1 to 6 August, in light of the coronavirus pandemic.
*Image courtesy of Black Hat from https://www.blackhat.com/us-20/
Related Post
新聞
2022.03.22
【Cybernews 專訪】TeamT5 執行長蔡松廷表示企業不宜宣稱自身100%不會被駭入
ThreatSonar, cyber security, ThreatVision, cyber threat intelligence, threat hunting
活動訊息
2021.05.12
[BlackHat Asia] TeamT5 研究員登上亞洲黑帽安全大會
Black Hat, Mem2Img, CloudDragon, Black Hat Asia, cyber threat intelligence, threat hunting
活動訊息
2022.02.09
TeamT5 於 CTI Summit 2022 分享最新威脅情資研究
seminar, cyber threat intelligence, threat hunting
技術分析
2022.03.01
Mikrotik 漏洞揭露與通報 (CVE-2021-41987)
vulnerability research