本文改寫自 2024 年 1 月第一期的漏洞情資報告(VIR 2024 June H1)。
TeamT5 漏洞研究團隊致力於針對重大漏洞提供即時的應對措施與緩解方案。如欲進一步了解 TeamT5 的漏洞情資報告,請與我們聯繫。
CVE-2023-29300: Adobe ColdFusion 漏洞
CVE-2023-29300 是出現在 Adobe 旗下應用程式開發平台 ColdFusion 的 JAVA 反序列化漏洞。該漏洞將導致任意程式碼執行。未經授權的威脅行動者可利用 CVE-2023-29300 將 Webshell 部署到目標設備。
Alerts of Exploiting Adobe ColdFusion
TeamT5 released mitigation and response guidelines to CVE-2023-29300 in Adobe ColdFusion. CVE-2023-29300 is a JAVA deserialization vulnerability resulting in arbitrary code execution. Adobe ColdFusion is a commercial rapid web-application development computing platform. Unauthorized threat actors can exploit CVE-2023-29300 and deploy webshell to target's devices and establish persistence.
Executive Summary
We assess the severity level of CVE-2023-29300 is critical and urge our customers to use this report to mitigate the effects. First, Adobe ColdFusion is widely used by large companies and organizations, with more than 3000 devices in Japan. Even worse, our investigation revealed that at least 66 Adobe ColdFusion devices in Japan has been compromised. The victims are across different sectors, including healthcare, education, and manufacturing industry. Furthermore, the Proof of Concepts (PoC) exploiting CVE-2023-29300 has been circulating in the wild. Public reports also provide the root cause analysis on CVE-2023-29300.[1]
Threat actors, including cybercriminals and state-sponsored APT groups, has been actively exploiting CVE-2023-29300 in the attacks. Specifically, we have detected that threat actors exploited CVE-2023-29300 to deploy webshells such as Behinder. Aligned with our observation, U.S. Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2023-29300 to known exploited vulnerabilities catalog on January 8, 2024.[2] We summarized the activities in the Exploitation Status subsection.
Based on the exploitation status, we depicted the Possible Attack Scenario in this report. We also concluded the malware and IOCs in Appendix II: Malware and Appendix III: Indicators of Compromise (IoC), respectively. Most importantly, we prepare a comprehensive Mitigation and Response Advisory for our customers.
The Mitigation and Response Advisory includes:
- Mitigation Adversary
- Open-source nuclei-based vulnerability scanner
- Threat Hunting Tools, including a SIGMA rule and a nuclei-based webshell scanner.
- SIGMA rule to check if ColdFusion server
coldfusion.exelaunches suspicious process via malicious webshell. - Nuclei-based webshell scanner to detect webshells deployed after exploiting CVE-2023-29300.
Exploitation Status
CVE-2023-29300 has been actively exploited by threat actors, including cybercriminals and state-sponsored threat actors. We concluded all the related C2 in the report IoC.[3]
- Cybercriminals have exploited CVE-2023-29300 to deploy webshell in attacks. We have detected attacks against healthcare entities and Thai real estate entities.
- China-nexus APT group SLIME13 (as known as Flax Typhoon) exploited CVE-2023-29300 in the attacks.
- Notably, Chinese actors exploited CVE-2023-29300[4] in the 2023 HuWang Operation, China’s state-led penetration testing for enterprises.[5] Previously, China-nexus APT groups such as Amoeba, SLIME28, and SLIME37 have joined the HuWang Operation.
Affected Products
ColdFusion 2018 (Update 16 and earlier versions)
ColdFusion 2021 (Update 6 and earlier versions)
ColdFusion 2023 GA Release (2023.0.0.330468)
ColdFusion 2021 (Update 6 and earlier versions)
ColdFusion 2023 GA Release (2023.0.0.330468)
Mitigation and Response Advisory
1. Official Patch Information
Adobe has released the official patches for CVE-2023-29300.
2. Open-source Nuclei-based Vulnerability Scanner
Our customers can leverage the open-source nuclei-based vulnerability scanner to detect if the vulnerability is in the ColdFusion Component.
3. Threat Hunting Tools
Cybercriminals and state-sponsored threat actors have already actively exploited CVE-2023-29300. TeamT5 vulnerability intelligence team prepared a SIGMA rule and a nuclei-based webshell scanner for our customers to detect potential threats.
The Threat Hunting Tools in ThreatVision includes:
- SIGMA rule to check if ColdFusion server
coldfusion.exelaunches suspicious process - Nuclei-based webshell scanner to detect webshells deployed after exploiting CVE-2023-29300.
Our customers can download all tools from the Threat Hunting Tools in ThreatVision.
Possible Attack Scenario
Threat actors have to first abuse the unauthenticated ColdFusion Component (CFC) endpoint to exploit CVE-2023-29300. Public proof of concepts has exposed a ColdFusion Component endpoint
/CFIDE/adminapi/accessmanager.cfc that also been exploited in the wild. Our customers can check if your ColdFusion Component endpoint has been attacked with following IIS log.C:\inetpub\logs\LogFiles\W3SVC1\u_ex240112.log:2024-01-12 08:12:12 172.17.0.1 POST /CFIDE/adminapi/accessmanager.cfc _cfclient=true&method=foo 443 - 172.17.0.2 Mozilla/5.0+(Macintosh;+Intel+Mac+OS+X+10_10_1)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/37.0.2062.124+Safari/537.36 - 404 0 2 1466Our customers can also leverage the open-source nuclei-based webshell scanner to detect if the vulnerability is in the ColdFusion Component.
CVE-2023-29300 is a deserialization vulnerability originated from the Web Distributed Data eXchange (WDDX) library. Once exploited, the vulnerability will allows the threat actors to load the payload via JNDI injection, connecting to the C2 and execute arbitrary codes.
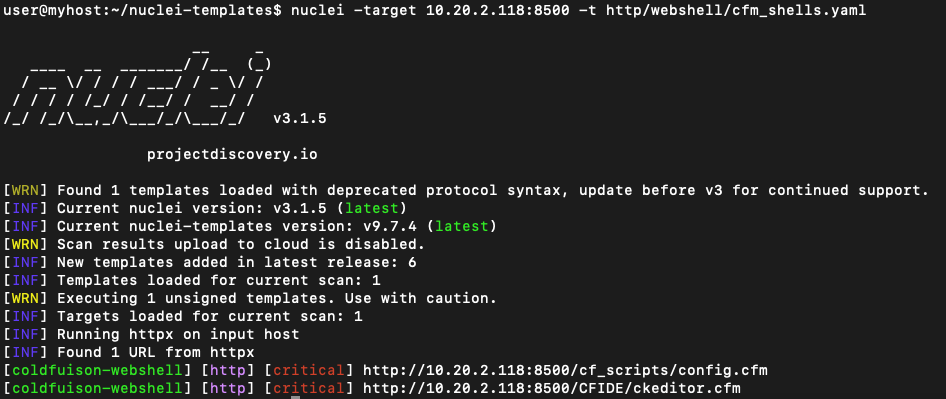
The threat actors can deploy webshell to ColdFusion after successfully exploited CVE-2023-29300. With such webshell exists, the threat actors can still access ColdFusion Component even after patching the vulnerability. Our analysis found that more than 1% of the ColdFusion Components in Japan has been compromised. The webshells contains following malicious URI:
- COLDFUSION_SERVER/cf_scripts/config.cfm
- COLDFUSION_SERVER/cf_scripts/123.cfm
- COLDFUSION_SERVER/cf_scripts/system.cfm
- COLDFUSION_SERVER/cf_scripts/classes/GetVars.cfm
- COLDFUSION_SERVER/cf_scripts/classes/ckeditor.cfm
Based on the research, we provide a nuclei-based webshell scanner and a SIGMA rule for our customers to check if your ColdFusion Component endpoint has been compromised, and the nuclei-based webshell scanner can identify implanted webshells as follows. Our customers can download the tools from The Threat Hunting Tools in ThreatVision.
Notably, we also detected that Chinese threat actors developed webshell designed for ColdFusion Markup, PowerShell[5]. PowerShell will download the second stage webshell from C2
http://113.141.91.61:63211/11.aspx. The second-stage webshell is Behinder[6], a famous open-source webshell in Chinese threat actors.Appendix I: Malware Table
Below malware table summarize the malware used in attacks related to CVE-2023-26360.
| Name | Type | Description | Attribution | First Seen |
|---|---|---|---|---|
| Behinder | Webshell | Behinder is a webshell developed by Chinese actor. It has different platform versions, such as PHP, ASP and JSP. Behinder loads an AES-encrypted binary payload which is difficult to detect by general firewall. | Open-source | 2020.06 |
Appendix II: Indicators of Compromise (IoC)
SHA-256
hash= webshell
cb493680d1a8ee7a70a2d339ece0b190db02fba4ba6af3b2c26a6b4841902d52
d6910571564cc4c61b1277334701c612fd3a25b96b63b267d64fcf48a5998254c2-IP= IP
113.141.91.61Appendix III: Other critical CVEs
TeamT5 also provides analysis of other caitical CVEs in Patch Management Report (PMR). Published every two weeks (or more), the PMR will provide our customers with concise yet comprehensive updates on the most critical and exploitable vulnerabilities selected by TeamT5 vulnerability research team during the period. Each vulnerability will be provided with patch information. If you are interested in subscribing to this new report series, please contact TeamT5 for more information.
[4] The HuWang Operation is China’s state-led penetration testing or red teaming operation for state-owned enterprises and critical information infrastructure (CII) operators, hosted by the Ministry of Public Security every summer. We have previously discovered that several APT groups such as Amoeba, SLIME28, and SLIME37 have joined China’s HuWang Operation.
[5] SHA-256: cb493680d1a8ee7a70a2d339ece0b190db02fba4ba6af3b2c26a6b4841902d52
[6] d6910571564cc4c61b1277334701c612fd3a25b96b63b267d64fcf48a5998254
Related Post
產品與服務
2023.10.31
什麼是資安漏洞? 資安漏洞有分級嗎?
vulnerability research
技術分析
2023.12.26
【TeamT5 杜浦數位安全】Pwn2Own 參賽心得分享及漏洞展示
vulnerability research